Infrastructure Provisioning for Cloud-Native Applications
Learn about Infrastructure as Code, its benefits, popular IaC tools, how to model infrastructure as part of the CI/CD pipeline, and how to incorporate it.
Join the DZone community and get the full member experience.
Join For FreeThis is an article from DZone's 2022 DevOps Trend Report.
For more:
Read the Report
Enterprises are embracing cloud-native technologies to migrate their monolithic services to a microservices architecture. Containers, microservices, container orchestration, automated deployments, and real-time monitoring enable you to take advantage of cloud-native capabilities. However, the infrastructure required to run cloud-native applications differs from traditional ones.
This article will describe Infrastructure as Code, its benefits, and the popular IaC tools. You will also learn how to model infrastructure as part of the CI/CD pipeline and incorporate it into the standard development lifecycle.
What Is Infrastructure as Code?
IaC helps to manage and provision infrastructure resources through code and automation. In a traditional on-premises environment, operators log into the server and execute a series of commands via the command line or console to perform changes. However, these manual configurations are prone to drifts and create inconsistent environments. It's also a time-consuming process to deploy similar changes across your infrastructure. There is no quick way to verify the correctness of these manual changes. If there are issues, it isn't easy to recreate them.
In comes IaC to simplify the management and provisioning of your infrastructure resources. With IaC, you don't make manual changes to servers, instances, containers, or environments. Both the creation and modification of the resources are automated. IaC is the practice of using code to create, describe, and manage infrastructure resources.
Infrastructure as Code Benefits
Let's now take a close look at how IaC can benefit your organization.
Increased Productivity Through Automation
Making infrastructure changes and deploying them is a repetitive process, and it is time-consuming if your developers/ operations team needs to do these manually in a recurring interval. With IaC, you can focus on coding and be more productive by automating the infrastructure deployments. As a result, IaC enables faster time to market for your business features.
Repeatable Deployments With High Predictability
Having your infrastructure defined in source control lets you automate the deployment process and enable developers to follow the software development lifecycle for infrastructure changes. It also empowers developers to perform successful deployments backed by efficient practices like peer review, static code analysis, and automated testing.
Improved Consistency With Minimal Configuration Drift
Performing infrastructure changes manually can lead to inconsistency between the servers and is generally the primary reason for configuration drifts. Applying changes manually is error-prone, and so IaC saves the day by standardizing the infrastructure modification process. The deployment process is faster, repeatable, and more consistent with automation and version control.
Documented Process for Deploying Changes
It would be best not to completely rely upon your sysadmin or operations team to deploy infrastructure changes. This increased dependency on selected operators to make server changes can create blocker scenarios when they are not available. In the long run, it is not a scalable solution. Having the infrastructure code in source control provides visibility to everyone in your organization about the current state. Developers can deploy infrastructure changes if all the stages in the CI/CD pipeline pass. If there are any issues, it's easy to troubleshoot by looking at the change history in the source control.

Figure 1: Infrastructure as Code in action
Infrastructure as Code Tools
Some open-source IaC tools can be categorized into various groups:
- Configuration management tools – Chef, Puppet, and Ansible are popular tools that allow you to install, update, and manage resources on existing infrastructure.
- Server templating tools – Tools like Docker and Vagrant allow you to create an image from a configuration file, which is then used to provision infrastructure in a repeatable manner. They promote the idea of an immutable infrastructure, which we will explain later in this article.
- Container orchestration tools – Tools like Kubernetes and Docker Swarm allow you to orchestrate container workloads in a dynamic cloud-native landscape.
- Provisioning tools – Tools like Terraform, Azure Resource Manager, Google Cloud Deployment Manager, and AWS CloudFormation allow you to provision servers and other resources in the respective cloud environment.
Figure 2: Infrastructure-as-Code tools
Mutable vs. Immutable Infrastructure
With immutable infrastructure, you create a new server with the revised configuration if you want to modify an existing server. In a cloud-native environment, where containers are spinning up and down every minute, immutability is a required feature. You should package your application and its dependencies into a container image, and as you want to modify the configuration, you deploy a new container version.
The pets vs. cattle analogy for infrastructure management is popular in the dynamic container space. You treat your infrastructure resources like cattle so that you can delete and build them from scratch when a configuration change is required. Pets are indispensable resources where you make configuration changes in place. Immutability helps simplify your operations, minimize drift, boost consistency between environments, and build a secure infrastructure.
Declarative vs. Procedural Approach
With a procedural approach, you write separate scripts to achieve the desired state. Over time, you tend to have many scripts that have been applied to your environment, and you can review the modifications via change history. The order of execution of the scripts matters, or else you end up with a different end state. Tools like Chef and Puppet follow the procedural style of infrastructure management. Please find below some of the frequently used Puppet commands:
| Command | Action |
|---|---|
puppet agent |
Retrieve configuration from a remote server and apply to localhost |
puppet apply |
Apply individual manifests to the local system |
puppet module |
Find, install, and manage modules in the puppet repository |
puppet describe |
Displays metadata about puppet resource types |
puppet config |
Review and modify settings in the puppet configuration file |
With the declarative approach, you maintain the desired state in a configuration template. If you want to make any modifications, you update the same template to reflect the desired state and let the IaC tool generate the difference script and apply it to the environment. Tools like Terraform follow the declarative approach, where the code in source control always reflects the current state of the infrastructure. The declarative approach helps you to create reusable code since you are just focused on describing the desired state and offloading the complexity of syncing the current and desired state to the IaC tool.
Using Terraform to Manage Infrastructure
Terraform is a cloud-agnostic, open-source tool for infrastructure provisioning. Created by HashiCorp in 2014, Terraform uses HashiCorp Configuration Language (HCL) to describe infrastructure code. It supports many providers and can help manage resources in individual cloud providers, such as AWS, Azure, and Google Cloud. Terraform is backed by a large and growing community. The primary function of Terraform is to help you create, modify, and destroy infrastructure resources. To provision resources using Terraform, you need to use the following commands:
| Command | Action |
|---|---|
terraform init |
Initializes the working directory that contains the configuration files |
terraform plan |
Compares the current state and desired state and creates an execution plan for making changes |
terraform apply |
Applies the changes that were proposed by the Terraform plan and ensures that the desired state is reached |
terraform destroy
|
Cleans up the infrastructure resources that are managed by the configuration files |
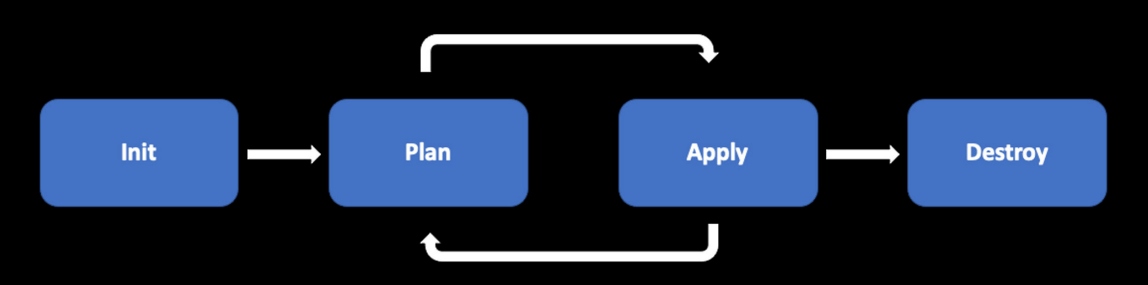
Figure 3: Terraform lifecycle
Infrastructure Automation With GitOps
GitOps workflows apply DevOps best practices for application development (version control, code review, automated deployments, etc.) to infrastructure deployments. GitOps is based on the declarative model, where configuration files get stored in Git, and approved changes get automatically deployed to the environment. As shown in Figure 4, the GitOps operator ensures that the desired state stored in Git is in sync with the actual state of the deployed infrastructure. Enterprises are rapidly adopting GitOps to manage their Kubernetes cloud-native environments at scale. Applying GitOps practices enables continuous deployments with proper auditing and high reliability.
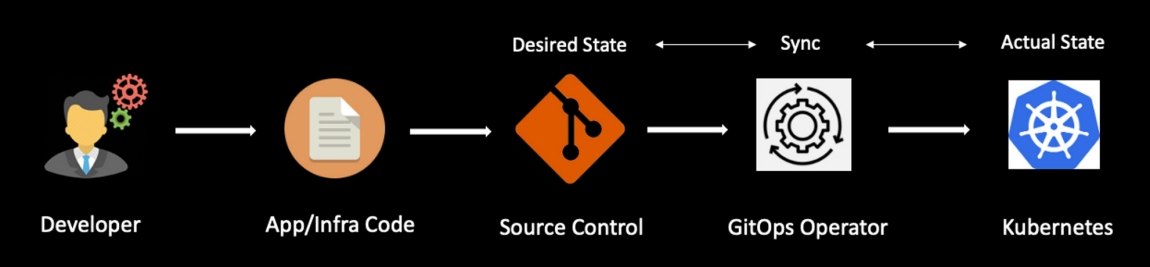
Figure 4: GitOps pipeline
Conclusion
IT infrastructures are growing exponentially and embedding automation into every stage of the delivery pipeline ensures faster and more consistent deployments. Automating your IaC processes is as important as the automation of your application deployment. You can leverage multiple IaC tools together to automate your infrastructure management. Each of the tools mentioned in this article has its strengths and weaknesses, so having a sound understanding of those and selecting the right tool that fits your use case is critical. IaC is the future, and organizations are readily embracing it to increase the reliability of their infrastructure.
This is an article from DZone's 2022 DevOps Trend Report.
For more:
Read the Report
Opinions expressed by DZone contributors are their own.

Comments