Implementing Cryptography (PGP And JCE) Module With MuleSoft
Cryptography is a way of securing the data/information when sending over a network or any source of communication between two or more entities.
Join the DZone community and get the full member experience.
Join For FreeIntroduction
Cryptography is a way of securing the data/information when sending over a network or any source of communication between two or more entities. In simpler words, it is used to convert plain text messages into encrypted messages and vice versa.
MuleSoft Cryptography module provides various techniques or algorithms for securing the message.
These techniques are capable of encrypting, decrypting, signing, and validating the data or messages.
- PGP Cryptography
- JCE Cryptography
- XML Cryptography
What Is Private and Public Key?
Private Key is used to encrypt and sign the data or information whereas public key is used to decrypt and validate the signature of data or information.
PGP Cryptography
PGP (Pretty Good Privacy) encryption is used for encrypting, signing, and decrypting data like emails, text, files, directories, and whole disk partitions. It also increases the security of email communication and it can be used to authenticate digital certificates. Public and private keys play a vital role in PGP to encrypt and decrypt the data. Generally, a public key is used to encrypt the data and it is always shared with end users. The private key is used to decrypt the data and it is never shared with anyone.
MuleSoft provides PGP Cryptography which is capable of compressing and securing the data when transmitted over the network. PGP Cryptography is capable of encryption, decryption, sign and validation.
We will be requiring the private and public for decrypting and encrypting the message and will be git bash to generate public and private keys in .gpg format.
Generate Key
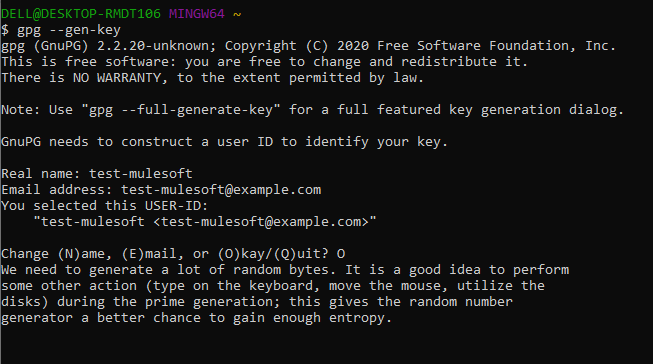
We will be executing below command on Git Bash and provide Real name and Email address.
gpg --gen-key
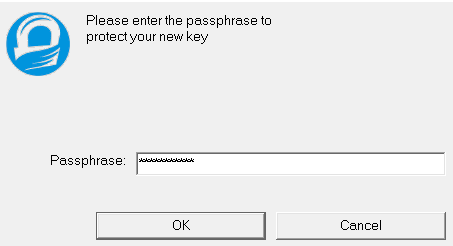
Once you provided Real name and Email address. Now, you need to provide a Passphrase and do not forget it.
Generate Public Key
We will be generating public keys from the above generated key. Execute below command on the Git Bash to list all the keys.
gpg --list-secret-keys --keyid-format LONG
Once we execute the command, we can see our keys in the list and it can be identified using name and email which we have given while generating the keys.
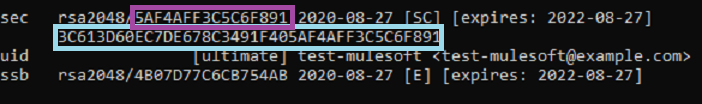
In the above screenshot, text highlighted in purple is fingerprint and text highlighted in blue is keyId.
We will execute the below command for generating the public key and key can be identified using email. This will generate a public key on a given location.
xxxxxxxxxx
gpg --output C:\\Certificates\\mule_pub.gpg --export test-mulesoft.com
Generate Private Key
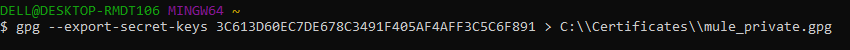
We will execute the below command for generating the private key and key can be identified using keyId.
xxxxxxxxxx
gpg --export-secret-keys 3C613D60EC7DE678C3491F405AF4AFF3C5C6F891 > C:\\Certificates\\mule_private.gpg
Once we execute the command, it will prompt for the Passphrase and we should give same Passphrase that has been provided during key generation.
This will generate a private key on a given location.
Implementing PGP in MuleSoft
We have generated Public and Private key. Now its time to implement in MuleSoft application, By default, Cryptography Module is not available in Mule palette. So we can install from the Anypoint exchange.
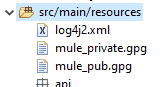
Copy and paste public and private key at src/main/resources.
PGP Encrypt
Click on Add (+) sign to perform Module configuration. Provide Public keyring and click on Add Pgp asymmetric key info (+). Public key is required to encrypt the data.

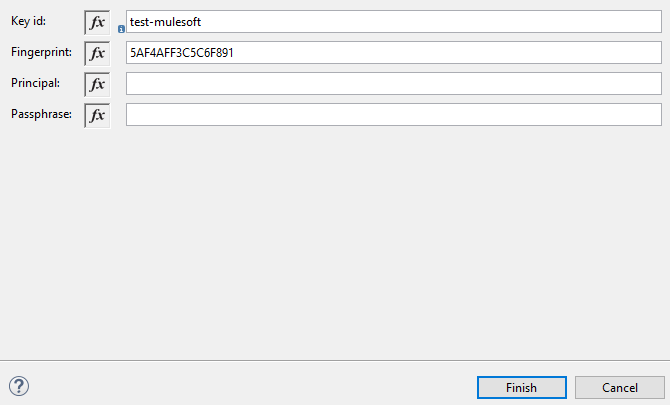
Once you click on the (+) button, it will open a pop-up window and provide any unique Key id and fingerprint. Click Finish.
 Now, we need to perform the General setting. Provide Algorithm and Key Id (i.e. it will be the same that we mentioned while configuring the asymmetric key info.
Now, we need to perform the General setting. Provide Algorithm and Key Id (i.e. it will be the same that we mentioned while configuring the asymmetric key info.
xxxxxxxxxx
<mule xmlns:ee="http://www.mulesoft.org/schema/mule/ee/core" xmlns:http="http://www.mulesoft.org/schema/mule/http"
xmlns:crypto="http://www.mulesoft.org/schema/mule/crypto"
xmlns="http://www.mulesoft.org/schema/mule/core" xmlns:doc="http://www.mulesoft.org/schema/mule/documentation" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://www.mulesoft.org/schema/mule/core http://www.mulesoft.org/schema/mule/core/current/mule.xsd
http://www.mulesoft.org/schema/mule/crypto http://www.mulesoft.org/schema/mule/crypto/current/mule-crypto.xsd
http://www.mulesoft.org/schema/mule/http http://www.mulesoft.org/schema/mule/http/current/mule-http.xsd
http://www.mulesoft.org/schema/mule/ee/core http://www.mulesoft.org/schema/mule/ee/core/current/mule-ee.xsd">
<http:listener-config name="HTTP_Listener_config" doc:name="HTTP Listener config" doc:id="5556a92f-b6c0-4a3d-9bbe-ba6f51686339" >
<http:listener-connection host="0.0.0.0" port="8081" ></http:listener>
</http:listener-config>
<flow name="pgp-exampleFlow" doc:id="99583c24-2a12-41d8-a2cb-5f8cc3cd05be" >
<http:listener doc:name="Listener" doc:id="ec92ce67-fd28-409d-a2c3-5bccec1d486f" config-ref="HTTP_Listener_config" path="/encrypt"></http:listener>
<crypto:jce-encrypt-pbe doc:name="Jce encrypt pbe" doc:id="e1debe02-6559-48cb-803a-2c2d302cb54c" password="mulesoft123"></crypto:jce>
<ee:transform doc:name="Transform To Base64" doc:id="0fdbf730-0499-482f-abb6-283aade46e8c" >
<ee:message >
<ee:set-payload ><![CDATA[%dw 2.0
output application/java
---
{
}]]></ee:set-payload>
</ee:message>
</ee:transform>
</flow>
</mule>-
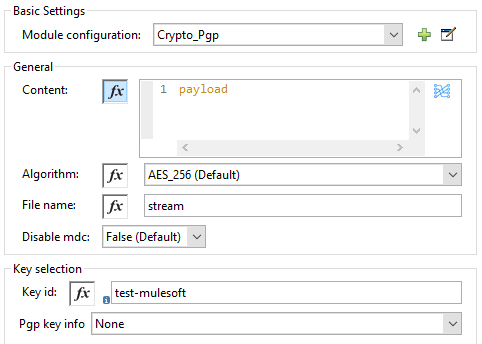
PGP Decrypt
Click on Add (+) sign to perform Module configuration. Provide Private keyring and click on Add Pgp asymmetric key info (+). Private key is required to decrypt the data.
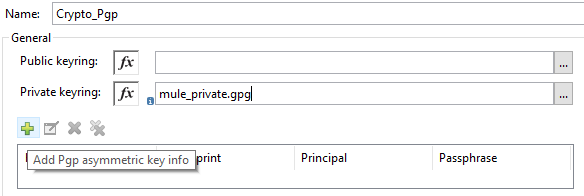
Once you click on the (+) button, it will open a pop-up window and provide any unique Key id, fingerprint and Passphrase (i.e. provided during key generation). Click Finish.
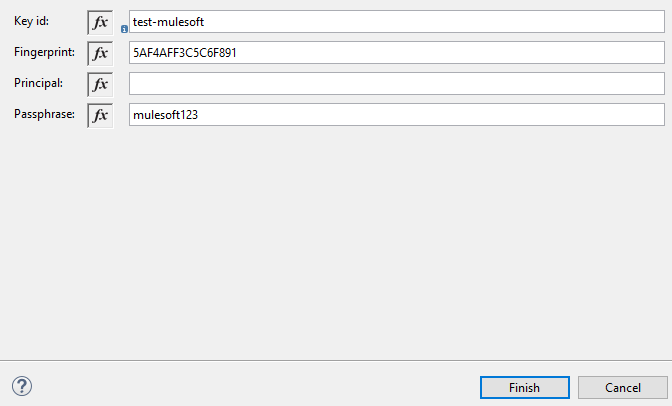
This are the only configuration required for message decryption.
PGP Decrypt [Code]
xxxxxxxxxx
<mule xmlns:http="http://www.mulesoft.org/schema/mule/http" xmlns:crypto="http://www.mulesoft.org/schema/mule/crypto"
xmlns="http://www.mulesoft.org/schema/mule/core"
xmlns:doc="http://www.mulesoft.org/schema/mule/documentation" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://www.mulesoft.org/schema/mule/core http://www.mulesoft.org/schema/mule/core/current/mule.xsd
http://www.mulesoft.org/schema/mule/crypto http://www.mulesoft.org/schema/mule/crypto/current/mule-crypto.xsd
http://www.mulesoft.org/schema/mule/http http://www.mulesoft.org/schema/mule/http/current/mule-http.xsd">
<http:listener-config name="HTTP_Listener_config" doc:name="HTTP Listener config" doc:id="5556a92f-b6c0-4a3d-9bbe-ba6f51686339" >
<http:listener-connection host="0.0.0.0" port="8081" />
</http:listener-config>
<crypto:pgp-config name="Crypto_Pgp" doc:name="Crypto Pgp" doc:id="8d1a5844-eb1c-4e9b-ab9d-5cbc29af293e" privateKeyring="mule_private.gpg" >
<crypto:pgp-key-infos >
<crypto:pgp-asymmetric-key-info keyId="test-mulesoft" fingerprint="5AF4AFF3C5C6F891" passphrase="mulesoft123" />
</crypto:pgp-key-infos>
</crypto:pgp-config>
<flow name="pgp-exampleFlow" doc:id="99583c24-2a12-41d8-a2cb-5f8cc3cd05be" >
<http:listener doc:name="Listener" doc:id="ec92ce67-fd28-409d-a2c3-5bccec1d486f" config-ref="HTTP_Listener_config" path="/encrypt"/>
<crypto:pgp-decrypt doc:name="Pgp decrypt" doc:id="89e65f04-4673-46c9-b78a-96f8bf9c1015" config-ref="Crypto_Pgp"/>
</flow>
</mule>
Implementing PGP Cryptography (Encryption And Decryption) For MuleSoft Applications
Implementing PGP Cryptography (Sign And Encrypt) For MuleSoft Applications
JCE Cryptography
JCE is stands for Java Cryptography Extension. We can use JCE Cryptography is 2 ways
- PBE (Password Based Encryption): - This enables to encrypt or decrypt or sign the data on basis of password.
- KBE (Key Based Encryption): - This enables to encrypt or decrypt or sign the data on basis of key (JKS, JCK, PKCS etc).
JCE Cryptography provides various operations like encrypt, decrypt, sign and validate like PGP.
Now, we will see how to configure JCE Encrypt and Decrypt using Password Based Encryption.
JCE Encrypt PBE
MuleSoft provides the JCE encrypt pbe component that can be used in mule flow to encrypt the data. We need to provide the password and Algorithm (i.e. there are many algorithms supported and we can select one of them). Finally, convert the JCE encrypt pbe output to Base64.
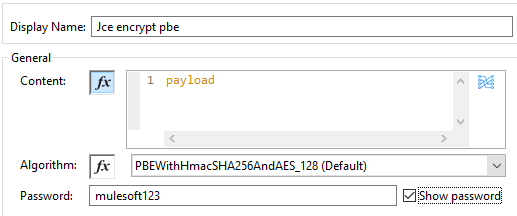
JCE Encrypt PBE [Code]
x
<mule xmlns:ee="http://www.mulesoft.org/schema/mule/ee/core" xmlns:http="http://www.mulesoft.org/schema/mule/http"
xmlns:crypto="http://www.mulesoft.org/schema/mule/crypto"
xmlns="http://www.mulesoft.org/schema/mule/core" xmlns:doc="http://www.mulesoft.org/schema/mule/documentation" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://www.mulesoft.org/schema/mule/core http://www.mulesoft.org/schema/mule/core/current/mule.xsd
http://www.mulesoft.org/schema/mule/crypto http://www.mulesoft.org/schema/mule/crypto/current/mule-crypto.xsd
http://www.mulesoft.org/schema/mule/http http://www.mulesoft.org/schema/mule/http/current/mule-http.xsd
http://www.mulesoft.org/schema/mule/ee/core http://www.mulesoft.org/schema/mule/ee/core/current/mule-ee.xsd">
<http:listener-config name="HTTP_Listener_config" doc:name="HTTP Listener config" doc:id="5556a92f-b6c0-4a3d-9bbe-ba6f51686339" >
<http:listener-connection host="0.0.0.0" port="8081" />
</http:listener-config>
<flow name="pgp-exampleFlow" doc:id="99583c24-2a12-41d8-a2cb-5f8cc3cd05be" >
<http:listener doc:name="Listener" doc:id="ec92ce67-fd28-409d-a2c3-5bccec1d486f" config-ref="HTTP_Listener_config" path="/encrypt"/>
<crypto:jce-decrypt-pbe doc:name="Jce decrypt pbe" doc:id="f1314308-89e2-4ee3-99de-5341fc72ccbe" password="mulesoft123"/>
<ee:transform doc:name="Transform To Base64" doc:id="0fdbf730-0499-482f-abb6-283aade46e8c" >
<ee:message >
<ee:set-payload ><![CDATA[%dw 2.0
output application/java
---
{
}]]></ee:set-payload>
</ee:message>
</ee:transform>
</flow>
</mule>-
JCE Decrypt PBE
MuleSoft provides the JCE decrypt pbe component that can be used in mule flow to decrypt the data. We need to provide the password (i.e. same password used during the JCE encrypt pbe) and Algorithm (i.e. same password used during the JCE decrypt pbe). We need to convert Base64 into Binary before applying JCE decrypt pbe.
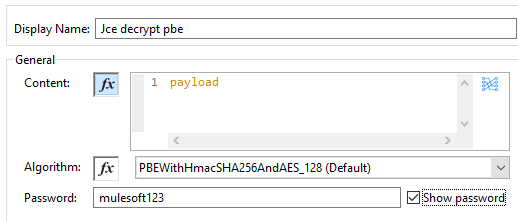
JCE Decrypt PBE [Code]
x
<mule xmlns:ee="http://www.mulesoft.org/schema/mule/ee/core" xmlns:http="http://www.mulesoft.org/schema/mule/http"
xmlns:crypto="http://www.mulesoft.org/schema/mule/crypto"
xmlns="http://www.mulesoft.org/schema/mule/core" xmlns:doc="http://www.mulesoft.org/schema/mule/documentation" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://www.mulesoft.org/schema/mule/core http://www.mulesoft.org/schema/mule/core/current/mule.xsd
http://www.mulesoft.org/schema/mule/crypto http://www.mulesoft.org/schema/mule/crypto/current/mule-crypto.xsd
http://www.mulesoft.org/schema/mule/http http://www.mulesoft.org/schema/mule/http/current/mule-http.xsd
http://www.mulesoft.org/schema/mule/ee/core http://www.mulesoft.org/schema/mule/ee/core/current/mule-ee.xsd">
<http:listener-config name="HTTP_Listener_config" doc:name="HTTP Listener config" doc:id="5556a92f-b6c0-4a3d-9bbe-ba6f51686339" >
<http:listener-connection host="0.0.0.0" port="8081" />
</http:listener-config>
<flow name="pgp-exampleFlow" doc:id="99583c24-2a12-41d8-a2cb-5f8cc3cd05be" >
<http:listener doc:name="Listener" doc:id="ec92ce67-fd28-409d-a2c3-5bccec1d486f" config-ref="HTTP_Listener_config" path="/encrypt"/>
<ee:transform doc:name="Transform Base64 to Binary" doc:id="0fdbf730-0499-482f-abb6-283aade46e8c">
<ee:message>
<ee:set-payload><![CDATA[%dw 2.0
import fromBase64 from dw::core::Binaries
output application/octet-stream
---
fromBase64(payload)]]></ee:set-payload>
</ee:message>
</ee:transform>
<crypto:jce-decrypt-pbe doc:name="Jce decrypt pbe" doc:id="0ffcacc6-1c5c-4a1a-ae83-495814b05f8f" password="mulesoft123"/>
</flow>
</mule>
Implementing JCE Cryptography (Password Based Encryption And Decryption) For MuleSoft Applications
Now, we will see how we can use JCE Key based encryption in the MuleSoft flow.
We can use symmetric or asymmetric keys for encryption and decryption. Symmetric key is basically used when a single secret key can perform both encryption and decryption whereas an asymmetric key is used when we require a private and public key for encryption and decryption.
In this article, we will be using the symmetric key. We will be using the below command to generate the jceks key and that we will be using for encryption and decryption.
xxxxxxxxxx
keytool -genseckey -keystore C:\Certificates\aeskeystore.jck -storetype jceks -storepass mulesoft -keyalg AES -keysize 128 -alias aeskey -keypass mulesoft
Copy aeskeystore.jck to folder src/main/resources of MuleSoft application.
JCE Encrypt
MuleSoft provides the JCE encrypt component that can be used in mule flow to encrypt the data.
Click on Add (+) sign to perform Module configuration. Provide keystore aeskeystore.jck, type and store password and click on Add Jce symmetric key info (+).
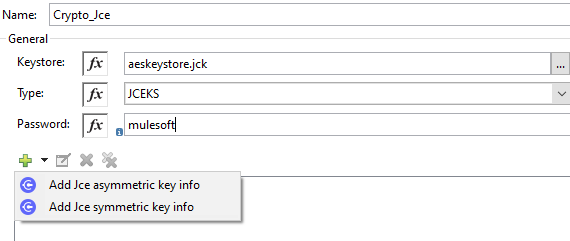
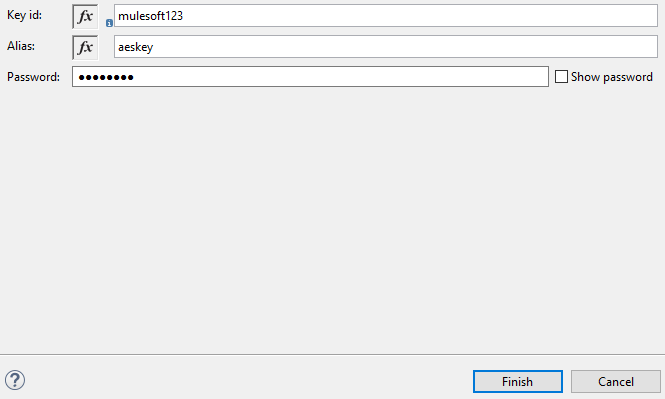
Once you click on the (+) button, it will open a pop-up window and provide any unique Key id, alias and key password. Click Finish.
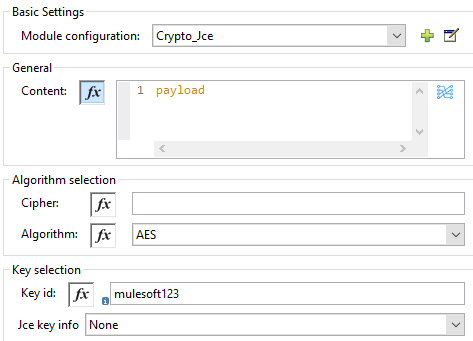
 Now, we need to perform the General setting. Provide Algorithm and Key Id (i.e. it will be the same that we mentioned while configuring the symmetric key info. Finally, convert the JCE encrypt pbe output to Base64.
Now, we need to perform the General setting. Provide Algorithm and Key Id (i.e. it will be the same that we mentioned while configuring the symmetric key info. Finally, convert the JCE encrypt pbe output to Base64.
JCE Encrypt [Code]
x
<mule xmlns:ee="http://www.mulesoft.org/schema/mule/ee/core" xmlns:http="http://www.mulesoft.org/schema/mule/http"
xmlns:crypto="http://www.mulesoft.org/schema/mule/crypto"
xmlns="http://www.mulesoft.org/schema/mule/core" xmlns:doc="http://www.mulesoft.org/schema/mule/documentation" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://www.mulesoft.org/schema/mule/core http://www.mulesoft.org/schema/mule/core/current/mule.xsd
http://www.mulesoft.org/schema/mule/crypto http://www.mulesoft.org/schema/mule/crypto/current/mule-crypto.xsd
http://www.mulesoft.org/schema/mule/http http://www.mulesoft.org/schema/mule/http/current/mule-http.xsd
http://www.mulesoft.org/schema/mule/ee/core http://www.mulesoft.org/schema/mule/ee/core/current/mule-ee.xsd">
<http:listener-config name="HTTP_Listener_config" doc:name="HTTP Listener config" doc:id="5556a92f-b6c0-4a3d-9bbe-ba6f51686339" >
<http:listener-connection host="0.0.0.0" port="8081" />
</http:listener-config>
<crypto:jce-config name="Crypto_Jce" doc:name="Crypto Jce" doc:id="0e01a75b-2eba-455a-932a-a43c0cc91bf6" keystore="aeskeystore.jck" type="JCEKS" password="mulesoft" >
<crypto:jce-key-infos >
<crypto:jce-symmetric-key-info keyId="mulesoft123" alias="aeskey" password="mulesoft" />
</crypto:jce-key-infos>
</crypto:jce-config>
<flow name="pgp-exampleFlow" doc:id="99583c24-2a12-41d8-a2cb-5f8cc3cd05be" >
<http:listener doc:name="Listener" doc:id="ec92ce67-fd28-409d-a2c3-5bccec1d486f" config-ref="HTTP_Listener_config" path="/encrypt"/>
<crypto:jce-encrypt doc:name="Jce encrypt" doc:id="ac5de28a-8880-4ec9-850f-dfe2f4b2ff51" config-ref="Crypto_Jce" algorithm="AES" keyId="mulesoft123"/>
<ee:transform doc:name="Transform To Base64" doc:id="0fdbf730-0499-482f-abb6-283aade46e8c">
<ee:message>
<ee:set-payload><![CDATA[%dw 2.0
import dw::Crypto
import toBase64 from dw::core::Binaries
output application/json
---
toBase64(payload)]]></ee:set-payload>
</ee:message>
</ee:transform>
</flow>
</mule>
JCE Decrypt
MuleSoft provides the JCE decrypt component that can be used in mule flow to decrypt the data.
Click on Add (+) sign to perform Module configuration. Provide keystore aeskeystore.jck, type and store password and click on Add Jce symmetric key info (+).
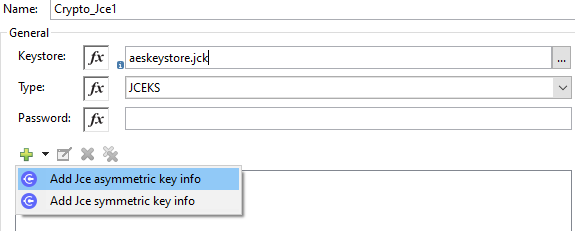
Once you click on the (+) button, it will open a pop-up window and provide any unique Key id, alias and key password. Click Finish.
 Now, we need to perform the General setting. Provide Algorithm and Key Id (i.e. it will be the same that we mentioned while configuring the symmetric key info. We need to convert Base64 into Binary before applying JCE decrypt.
Now, we need to perform the General setting. Provide Algorithm and Key Id (i.e. it will be the same that we mentioned while configuring the symmetric key info. We need to convert Base64 into Binary before applying JCE decrypt.
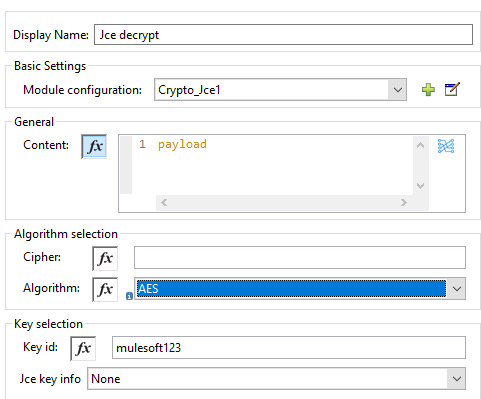
JCE Decrypt [Code]
xxxxxxxxxx
<mule xmlns:ee="http://www.mulesoft.org/schema/mule/ee/core" xmlns:http="http://www.mulesoft.org/schema/mule/http"
xmlns:crypto="http://www.mulesoft.org/schema/mule/crypto"
xmlns="http://www.mulesoft.org/schema/mule/core" xmlns:doc="http://www.mulesoft.org/schema/mule/documentation" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://www.mulesoft.org/schema/mule/core http://www.mulesoft.org/schema/mule/core/current/mule.xsd
http://www.mulesoft.org/schema/mule/crypto http://www.mulesoft.org/schema/mule/crypto/current/mule-crypto.xsd
http://www.mulesoft.org/schema/mule/http http://www.mulesoft.org/schema/mule/http/current/mule-http.xsd
http://www.mulesoft.org/schema/mule/ee/core http://www.mulesoft.org/schema/mule/ee/core/current/mule-ee.xsd">
<http:listener-config name="HTTP_Listener_config" doc:name="HTTP Listener config" doc:id="5556a92f-b6c0-4a3d-9bbe-ba6f51686339" >
<http:listener-connection host="0.0.0.0" port="8081" />
</http:listener-config>
<crypto:jce-config name="Crypto_Jce" doc:name="Crypto Jce" doc:id="0e01a75b-2eba-455a-932a-a43c0cc91bf6" keystore="aeskeystore.jck" type="JCEKS" password="mulesoft" >
<crypto:jce-key-infos >
<crypto:jce-symmetric-key-info keyId="mulesoft123" alias="aeskey" password="mulesoft" />
</crypto:jce-key-infos>
</crypto:jce-config>
<crypto:jce-config name="Crypto_Jce1" doc:name="Crypto Jce" doc:id="37453ff8-434d-43ba-be6c-cad24f5071ed" keystore="aeskeystore.jck" type="JCEKS" />
<flow name="pgp-exampleFlow" doc:id="99583c24-2a12-41d8-a2cb-5f8cc3cd05be" >
<http:listener doc:name="Listener" doc:id="ec92ce67-fd28-409d-a2c3-5bccec1d486f" config-ref="HTTP_Listener_config" path="/encrypt"/>
<ee:transform doc:name="Transform Base 64 to Binary" doc:id="0fdbf730-0499-482f-abb6-283aade46e8c">
<ee:message>
<ee:set-payload><![CDATA[%dw 2.0
import fromBase64 from dw::core::Binaries
output application/json
---
fromBase64(payload)]]></ee:set-payload>
</ee:message>
</ee:transform>
<crypto:jce-decrypt doc:name="Jce decrypt" doc:id="3604f6ad-4d34-432a-9063-27a42cbb0687" config-ref="Crypto_Jce1" algorithm="AES" keyId="mulesoft123"/>
</flow>
</mule>
Implementing JCE Cryptography (Key Based Encryption And Decryption) For MuleSoft Applications
Now, you know how to use PGP and JCE Cryptography With MuleSoft.
Opinions expressed by DZone contributors are their own.

Comments