How To Improve GraphQL API Security
Open-source GraphQL has become increasingly popular for API modernization — but securing GraphQL deployments requires foresight and smart execution.
Join the DZone community and get the full member experience.
Join For FreeThe open-source GraphQL query language has a ton to offer enterprises seeking a more scalable, flexible, developer-friendly, and modernized approach to API-driven development. That said, because I’m a security professional, I tend to focus on the new opportunities GraphQL also gives attackers. It’s been increasingly tempting for enterprises to dive headlong into GraphQL without fully assessing and addressing its security and operational requirements. However, doing so places intense pressure on security architects, DevOps and DevSecOps teams, and even developers themselves.
I’ve recently taken a deep dive into Inigo, a GraphQL security and management toolset. Here I’ll share a how-to guide for teams ready to introduce more secure GraphQL implementations based on what I’ve learned.
Implementing GraphQL Developer and DevOps Support
Inigo functions as an agent that runs alongside an organization’s GraphQL server or gateway (as middleware, in Docker, as a sidecar, or as a gateway plugin). It doesn’t require code changes, supports most GraphQL servers out of the box, and integration is pretty straightforward. For developers, the tools streamline some critical workflows, including access to analytics that capture GraphQL query insights, schema checks to understand usage patterns and plan effectively, and support across the API lifecycle. CI/CD tooling also reduces the need for more challenging custom builds and fixes.
Implementing GraphQL Security Support
Because I’m a security professional, my focus with GraphQL is focused on the vulnerabilities I see in immature GraphQL deployments and the safeguards I would like to see. If your organization is adopting GraphQL, you need to implement real-time query protection in order to prevent threats that hide within traffic to tamper with APIs and data — such as query-based DDoS or injection attacks. You need role-based access controls to restrict users’ visibility and access to only the required schema. You also need GraphQL rate limiting, which protects against overloads, data scraping, and performance issues in scenarios where an attack floods a single object with requests.
I was pleasantly surprised to see that the Inigo platform provides for each of those protections. For example, as a standard security practice, I always advise the organizations I work with to disable introspection queries to prevent schema exposure (accepting the trade-off of losing discoverability). However, with Inigo’s RBAC introspection separation, user access and schema visibility are already tightly controlled, so there’s no need to disable introspection. The schema-based access control and role-based declarative configurations provide granular access to types, fields, and arguments, which always helps security-minded individuals like myself sleep easier at night.
Another crucial best practice for enterprises is securing GraphQL from day one. Too often, enterprises dabble and experiment in GraphQL without committing the resources to achieve enterprise-grade security, imagining that they’ll do so once their GraphQL use case is proven. In reality, they’re allowing a gaping hole in their defenses and inviting severe consequences. Inigo’s platform stands as further proof that enterprise-grade tooling and expertise is now available, leaving no excuses for organizations that negligently leave themselves wide open to GraphQL attacks.
How To Give It a Test Run
Teams ready to try it should visit app.inigo.io and try out the available “Starwars Demo” setup.
With the demo up and running the Inigo dashboard will display analytics you can filter by timeframe.
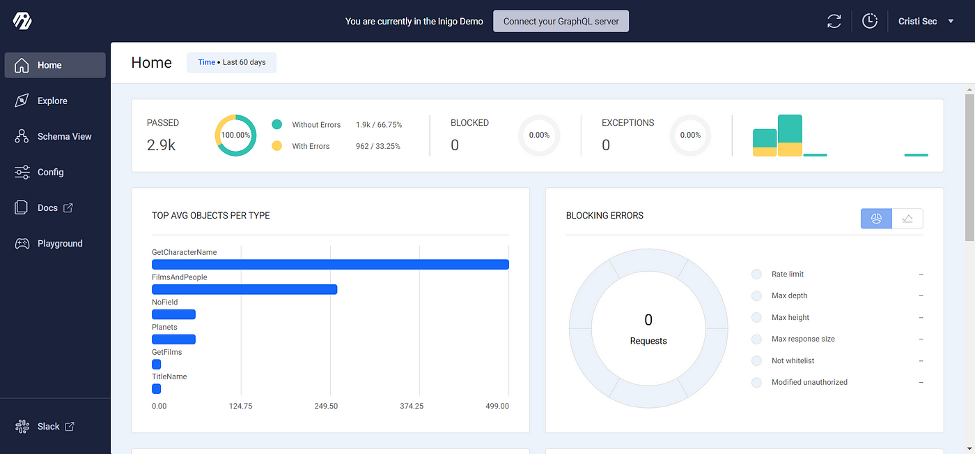
I particularly appreciate the ability to view the most recent errors (and errors on a user basis), as well as potential API implementation bottlenecks to be aware of.

Click the Explore tab. Here you can drill into any individual query to understand errors and performance.
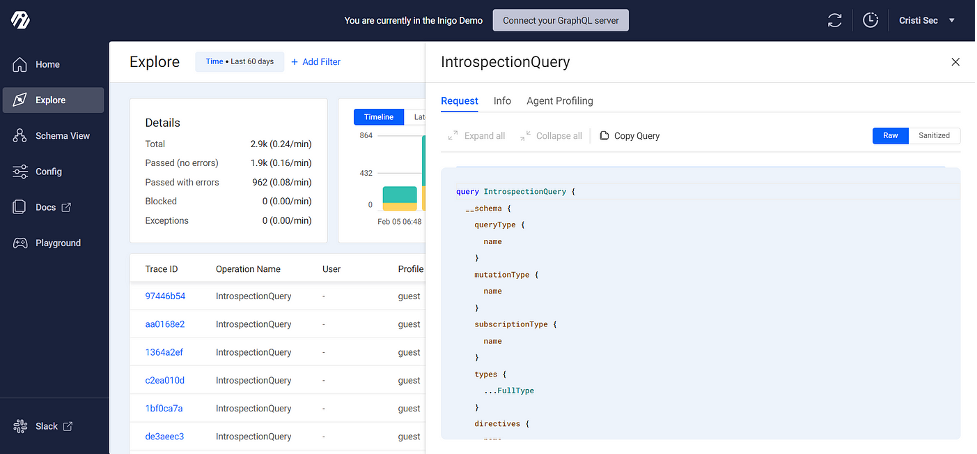
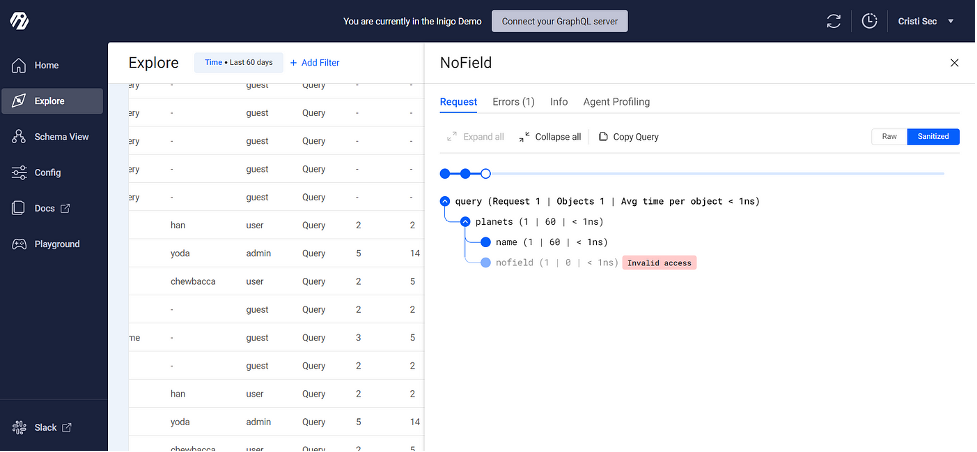
This sanitized version is also available to help to better recognize intentional attacks. From my perspective as a security provider, a client that offers me Inigo account access to inspect their GraphQL deployment with these tools is putting me in a better position to help them secure that deployment.
Click Schema View. This view features version control and makes information downloadable, which I find quite useful.
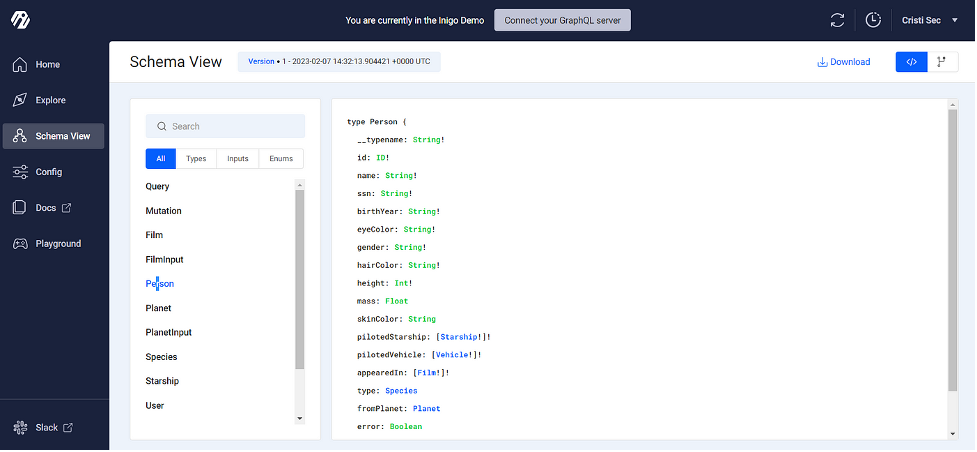
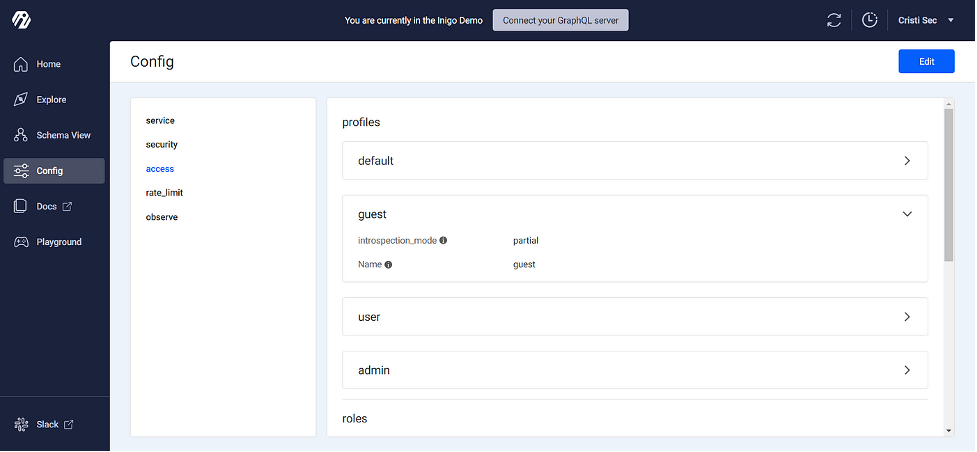
As I see it, the Config and Playground tabs are where the platform offers particularly unique value. Config lets you set up and edit configurations at a highly granular level, controlling all aspects of the service, security, access controls, and more. There’s also a CLI available, enabling configuration management via terminal and CI/CD pipeline integrations.
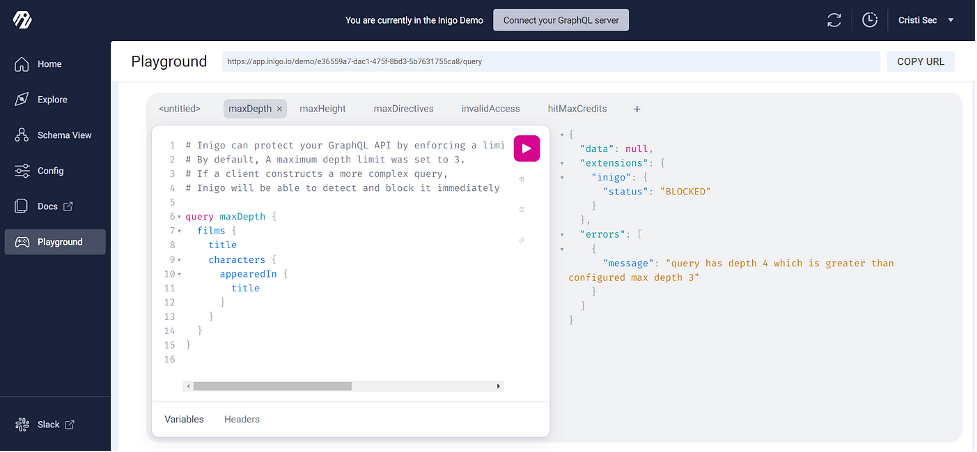
Playground enables you to fully test out queries and make sure they’re ready for primetime.
Security-Professional Approved
If your enterprise is about to embark on an exploration of GraphQL or needs to shore up an existing deployment (doing what you should have done from day one…), Inigo’s toolset is worth giving a spin. I now regularly recommend Inigo to my pen-testing clients and will be watching to see how future releases evolve this platform.
Opinions expressed by DZone contributors are their own.

Comments