How To Fix SignTool Error
Explore how to eliminate the SignTool Error "No certificates were found that met all the given criteria" in six easy steps.
Join the DZone community and get the full member experience.
Join For FreeAre you running into this error message but can’t seem to get past it to digitally sign your code using a code-signing certificate? We’ll walk you through the troubleshooting solutions that’ll fix the Signtool ‘no certificates were found’ error in no time.
Have you found yourself here because you’ve received the dreaded SignTool Error: No certificates were found that met all the given criteria message? If so, then you’ve come to the right place.
Let’s say you just finished developing and testing a great new application and are ready to move to production. You want to sign your code, but you feel like you’re running into walls because you keep getting this annoying error. Did you do something wrong to trigger this warning? Perhaps not directly. But it means there’s something amiss that you need to fix before you can proceed any further with your software.
Code signing is an important tool every developer and publisher should have in their toolbox. With this in mind, we'll walk you through some of the causes of this error message and will explore six ways to mitigate it.
What the SignTool Error: No Certificates Were Found That Met All the Given Criteria Warning Looks Like
Is SignTool not recognizing that you have certificates installed on your device? If so, then you’re likely seeing an error message that looks like this when you try to sign an executable using a code signing certificate in Windows:
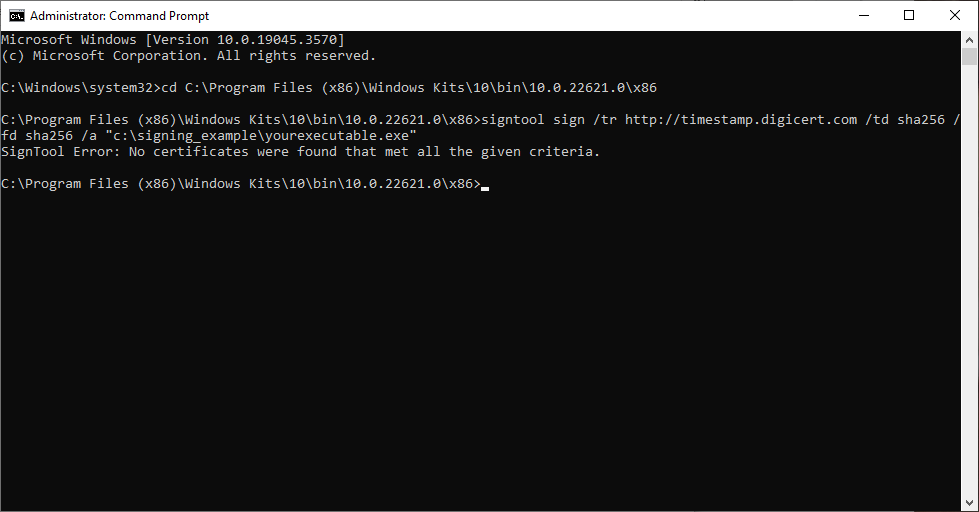
A screenshot of SignTool Error: No certificates were found that met all the given criteria message that displays when SignTool can’t find or recognize certificates installed on your computer.
When this happens, it’s not only an annoyance, but it can prevent you from being able to digitally sign your applications, updates, and code.
Common Causes of This SignTool Error
So, what are some reasons you might be seeing this error?
- No code signing certificate is listed in your local trust store (i.e., you didn’t properly import it).
- Your certificate isn’t publicly trusted (i.e., it’s a self-signed certificate).
- Your code signing certificate is listed but has expired
- You have imported the wrong type of certificate (e.g., a client authentication certificate instead of a code signing certificate).
- The Certificates snap-in hasn’t been added in MMC.
- Your user privileges may not be high enough.
Okay, so now you know some of the causes of the issue… So, what can you do to mitigate the error?
Six Ways To Fix the SignTool Error: No Certificates Were Found That Met All the Criteria
1. Check To See if Your Certificates Properly Imported
Do you see your certificates in Certificate Manager (CertMgr), as shown below?
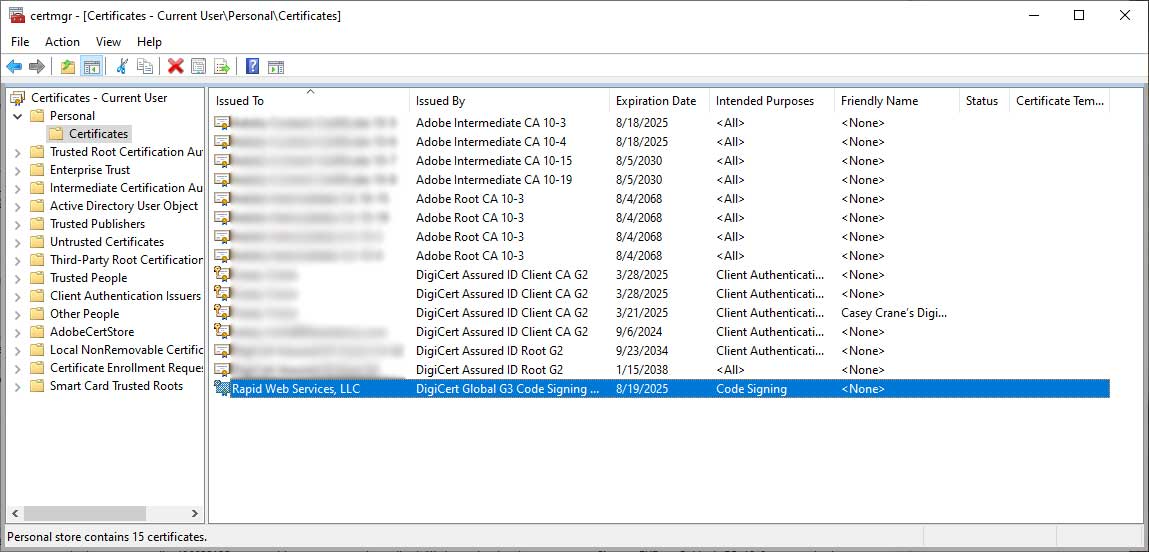
If so, great. Then, you can likely move forward with opening the Windows CMD prompt interface and using SignTool to digitally sign your software, code, and other executables. But if you don’t see your certificate there, it may mean that you’ll need to re-import your file, or you may be looking in the wrong place altogether.
Double-check to make sure you’ve opened the Certificate Manager (CertMgr) command-line utility on your device and not the Certificates – Local Computer (CertLM) screen. In the following screenshot, CertMgr is on the left, and CertLM is on the right:

Why point this out? Because both windows look very similar. But as you can see in the following example, when you dig a little deeper and click on the Certificates folder contained within each account, they won’t necessarily contain the same certificate files. This is because one is for managing computer certificates (CertLM), and the other is for managing user certificates (CertMgr).

2. Make Sure You Have a Code Signing Certificates Installed
This is easy to overlook, but this step requires you to check your CertMgr list to see whether you have a code signing certificate listed to begin with (ideally, a publicly trusted one if you’re planning to distribute your software outside your network). If you don’t have any certificates in there, it’ll definitely trigger the SignTool error.
If you’ve only used self-signed certificates during development and testing and haven’t purchased a publicly trusted certificate yet, now’s the time to do so before moving on to production.
Not only will using a publicly trusted certificate help to secure your software against tampering (in the case of organization validation [OV] certificates), but it also enables you to display your verified digital identity to users or even bypass the Windows Defender SmartScreen warning (in the case of extended validation [EV] code signing certificates) that cautions users to steer clear of your unrecognized app. Why? Because if it’s not digitally signed, Microsoft can’t verify the source of the app, so it doesn’t know whether you can be trusted as a publisher.
3. Check Your Certificate Expiration Dates
This is probably the easiest option for fixing the SignTool Error: No certificates were found that met all the given criteria issue. Look at the expiration dates listed for your certificates to see if they’re still valid.
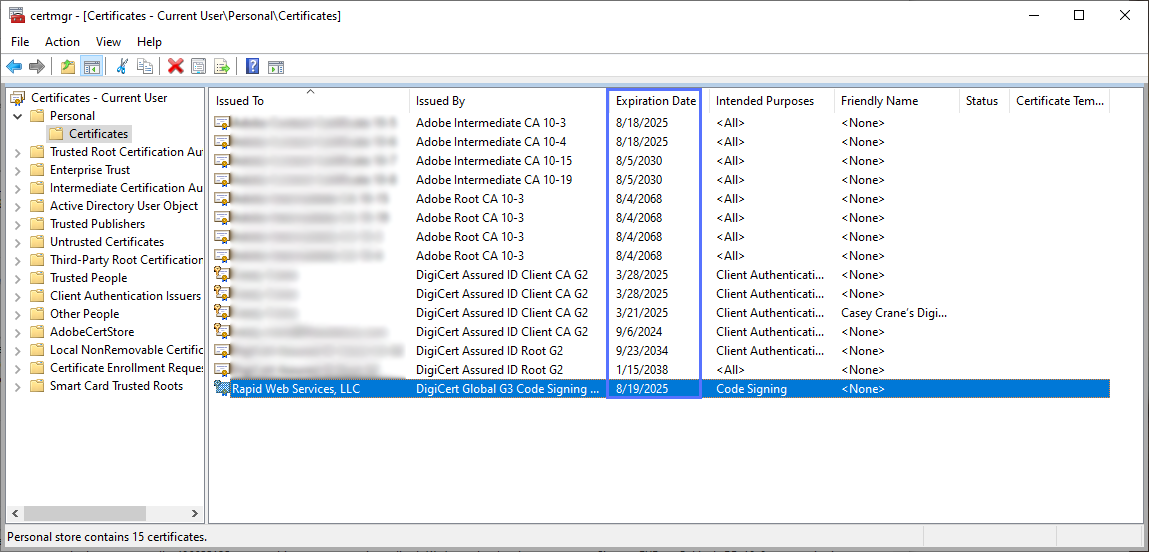
Oops — did you forget to renew your certificate, and now it’s expired? No worries, you can always get a new one. But if your organization’s validation information has also expired, you’ll need to get it revalidated with the certificate provider.
If your certificate hasn’t expired and you see a code signing certificate listed that’s valid, then it’s time to move on to the next step.
4. Check To See if Command Line Can Find Any Certificates
Another thing you can do is check to see what the command line is “seeing” (or, as the case may be, if it’s not “seeing” any certificates at all). You can do this using the following command in your command line window:
certutil -store -user My
Did it return a list of certificate details (as shown in the example below)?

Image caption: An example of the certificate information listed in Windows command line.
If so, that's excellent! Then, you can continue on to the next step.
If you’re not seeing a list of certificates, and Windows Command Prompt just says that the command has been completed (as shown in the next screenshot), then there’s more work to do.

Run the SignTool Debug Command
Another method to try to see what SignTool is seeing is to use the /debug parameter. You can insert this parameter into your signing command, like this:
signtool sign /debug /tr http://timestamp.digicert.com /td sha256 /fd sha256 /a "c:\signing_example\yourexecutable.exe"
Are you seeing a message like this? If so, it means that SignTool still isn’t seeing your certificates.

5. Check Your User Account Privileges
If everything you’ve done so far hasn’t mitigated the issue, then it may be time to reach out to your organization’s IT admin because you might not have the necessary privileges. This was the case for me, and frankly, it’s what spurred me to write this article!
In my case, I was logging in to SignTool using a temp IT admin account that was set up by our company’s administrator. It wasn’t until after my personal user account was upgraded to include certain admin-level privileges that I was finally able to start addressing the issue. After my privileges were increased, I no longer needed to log in to SignTool by selecting the “Run as Administrator” button and logging in using the separate temp admin account; I could simply sign software using the standard SignTool setting.
Upgrading my account privileges and simply opening SignTool using the standard setting (i.e., not selecting the “Run as Administrator”) setting was enough to fix it. In fact, when I tried to go back to sign software in SignTool using the “Run as Administrator” option (and logging in using the temp admin credentials), the SignTool error message “SignTool Error: No certificates were found that met all the given criteria” re-appeared because it could no longer locate the certificates.

But simply changing the privileges on my user account wasn’t the only thing we did…
6. Enable MMC Snap-Ins for Your Certificates
Remember the MMC Console Root utility we mentioned earlier? If you open that screen and see nothing (or no folder labeled “Certificates”) listed, then you may need to add the Certificates snap-in to your user account. This will allow you to view and manage the certificates associated with your account.
NOTE: You can manage only your user account's certificates if you don’t have administrator privileges.
The MMC’s Certificates snap-in enables you to install, monitor, and manage your digital certificates on your local machine, user account, or service account.
To enable the Certificates snap-in:
- Open the Microsoft Management Console (MMC) by going to the Start menu and using the run command MMC.

- Select File and choose Add/Remove Snap-In.

- In the left-hand column, select Certificates and hit the Add > button located between the two main columns. This should make Console Root > Certificates appear in the right-hand window.

- When prompted, select the certificates snap-in option you want (e.g., My user account, Service Account, or Computer account). In this case, since I just want the specific user to have access to the certificates, I’m just going to select My user account and hit Finish.

Wrapping Things Up
We hope that you’ve found this article useful and that it’s helped you get rid of that pesky SignTool error: No certificates were found that met all the given criteria. We’ve gone over several of the causes of this issue and have provided half a dozen potential solutions to help you mitigate it — one of which ways is to ensure you have a valid code signing certificate installed in your library.
Code signing is not only an industry best practice; it’s also a great way to strengthen your brand and reputation by asserting your digital identity up front in your software products.
Opinions expressed by DZone contributors are their own.

Comments