Zero Trust and Its Impact on Cybersecurity
With the rise of remote work and the dissolution of the traditional security perimeter, enterprises have shifted to a Zero-Trust model to improve security.
Join the DZone community and get the full member experience.
Join For FreeAccording to Forbes, 1 out of 5 people are working remotely. With a more distributed workforce, enterprises have significantly changed their operation style, encompassing shifts in company culture, meeting structures, and a surge in Virtual and Augmented Reality. Along with them, the approach to cybersecurity also evolved.
To better understand, let's rewind to the early 2000s when employees were onsite, connected to the company's corporate network acting as a security perimeter. All the egress and ingress traffic went through the perimeter protected by firewalls. With the advancement in Internet infrastructure, employees started working from home but continued connecting to corporate networks using VPNs. As years passed, devices became smarter, and how we access work spread from company-issued devices to personal mobiles and tablets. Subsequent growth in Cloud and IoT moved the workloads from running on-prem to operating globally, effectively dissolving the concept of a security perimeter, and demanding a new approach to secure enterprises.
This is when the term "Zero Trust" was coined. But like any other software adoption, the adoption of Zero Trust also did not start immediately. According to a report from Microsoft, the rise in remote work due to COVID-19 is among the contributing reasons organizations pushed to invest in the Zero Trust strategy.
Zero Trust
Zero Trust is an architectural approach that assumes no network is inherently trustworthy and treats every access request as potentially compromised.
Key principles of Zero Trust include the following:
1. Multi-Factor Authentication (MFA)
MFA involves using more than one authentication mechanism to access a system. Instead of just the user name and password, combine them with phone notification/pass keys. So if an attacker manages to steal a user's password, they would still need the second (or third) factor to access the account. Microsoft and Google have their offering in this space.
2. Network Segmentation
With Network Segmentation, you divide an organization network into multiple smaller isolated subnets with their security policies. As a result, even if a hacker gains access to one segment they cannot move laterally to other parts. Among the toughest ones to achieve but provides the biggest bang for the buck.
Network Segmentation has two types:
- Physical Segmentation: A simple illustration can be breaking a large network into small subnets and having a firewall at each subnet to monitor ingress and egress traffic. However, this approach requires significant hardware investments.
- Logical Segmentation: A software strategy that can either use VLAN or network addressing schemes to perform the segmentation. Also, it is easier and cheaper compared to Physical Segmentation.
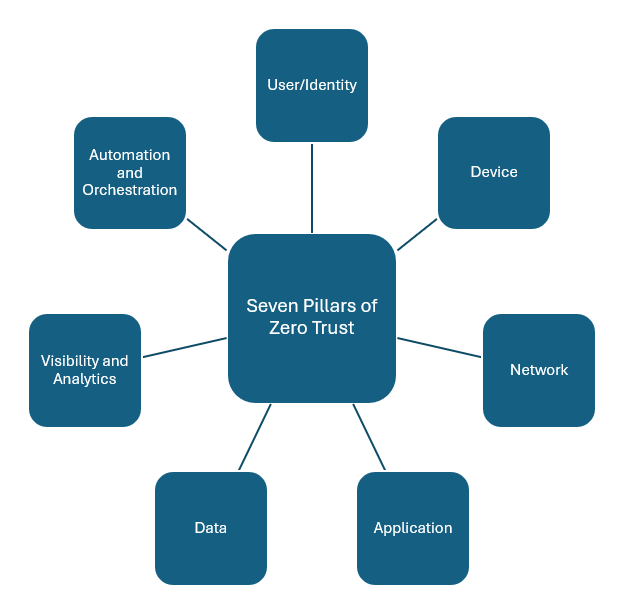
![Seven pillars of Zero Trust]()
Attack Surface Management
Attack Surface Management is also crucial for implementing Zero Trust. With Attack Surface Management, the organization does three things:
- Get an inventory of their digital assets like applications, networks, and devices.
- Identify vulnerabilities in the assets and categorize them with ratings like Critical, High, Medium, and Low. This will give a picture of the impact if an asset is compromised.
- Prioritize work to fix the vulnerabilities.
SolarWinds
The SolarWinds hack tells us keeping our supply chain secure is as important as securing ourselves.
- For S/W supply chain security, integrating tools that check for vulnerabilities in the CI/CD process drastically reduces hacks because of not patching vulnerabilities.
- For companies depending on third-party suppliers, conducting a risk assessment of each supplier's cybersecurity posture will help understand the impact on the company if the supplier is compromised. Using the results we can either limit access to the supplier or work with them to increase their security posture.
Emerging Technologies in the Zero Trust Space
Secure Access Service Edge (SASE)
Simply put, SASE is a cloud-based security framework that combines networking and security into a single service. Instead of connecting to the data centers using a VPN, connections happen to the nearest cloud edge. Then, Zero Trust policies are applied at the Cloud edge making this solution more scalable, secure, and seamless for worldwide connectivity.
User Behavior Analytics (UBA)
Tools in this area analyze user behavior to detect anomalies. For example, a person accessing a resource from an unknown device or trying to access a ton of resources in a short span can be tied to threat actors, demanding the organization to take immediate action.
Final Thoughts
All in all, remote work is here to stay. We will see companies adopting zero-trust policies and cloud-native security to improve their security posture while simultaneously offering a seamless experience to their employees.
Opinions expressed by DZone contributors are their own.

Comments