Full-Stack Security Guide: Best Practices and Challenges of Securing Modern Applications
Explore essential strategies, techniques, and tools to secure modern applications at every layer and the best practices and challenges encountered in full-stack security.
Join the DZone community and get the full member experience.
Join For FreeEditor's Note: The following is an article written for and published in DZone's 2024 Trend Report, Enterprise Security: Reinforcing Enterprise Application Defense.
Full-stack security protects every layer of a software application, including the front end, back end, infrastructure, and network. It integrates robust security measures to address vulnerabilities by employing tools and practices to maintain data integrity, prevent unauthorized access, and ensure compliance, especially as applications expand and integrate with various technologies and platforms.
Understanding the security measures required at each layer of an application is crucial for developers to ensure comprehensive protection. This guide explores essential strategies and tools to secure modern applications at every layer and addresses the best practices and challenges encountered in full-stack security.
Figure 1. Application security components
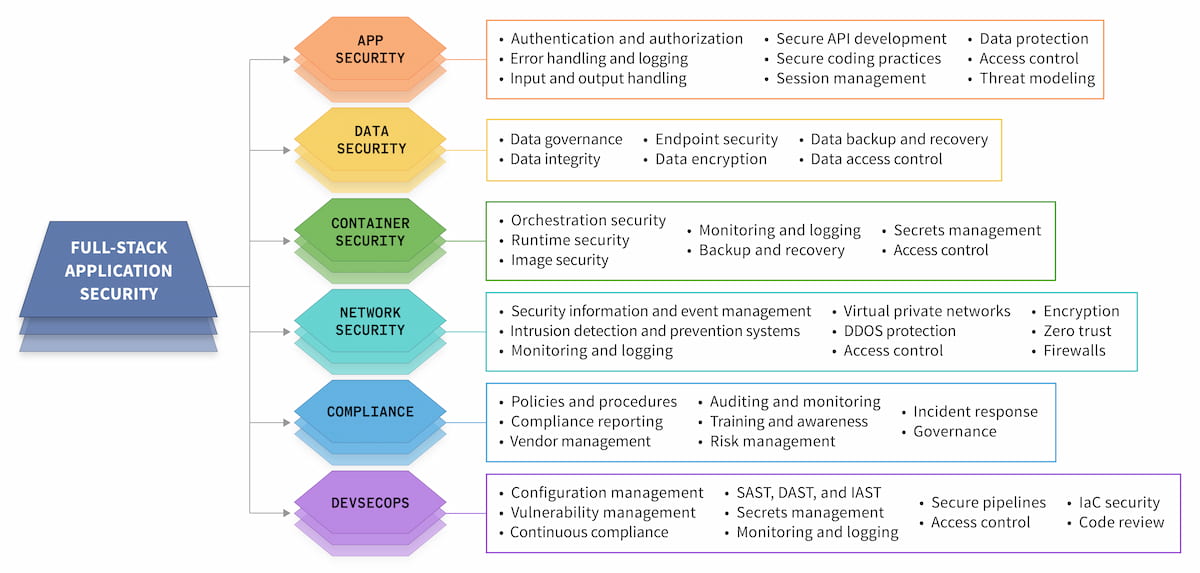
Threat Modeling for Full-Stack Applications
Threat modeling is crucial for keeping full-stack applications secure. It involves a thorough review to spot potential threats and weaknesses, allowing us to tackle these issues before the app goes live. This process requires a detailed look at the app's architecture, data flows, and how it operates. Using a checklist like the one below provides a structured approach to threat modeling.
Preparation Phase
- Understand the application's scope and purpose, including primary function and objectives, architecture, target audience, and application boundaries
- Assemble a cross-functional threat modeling team including developers, security experts, and system architects
Modeling Phase
- Document the application architecture, highlighting all components, data flows, and external interactions
- Identify trust boundaries and classify all data processed and stored by the application
Identification Phase
- List potential threat agents (e.g., hackers, third-party services)
- Catalog potential threats using frameworks like STRIDE
- Identify vulnerabilities (e.g., static analysis, code reviews)
Analysis Phase
- Assess the likelihood and impact of identified threats
- Prioritize threats based on their risk levels using a risk matrix
Mitigation Phase
- Propose mitigation strategies
- Assign responsibilities for implementing security measures
- Plan residual risk management for risks that cannot be fully mitigated
Implementation and Follow-Up Phase
- Implement the mitigation strategies and security controls
- Test and validate the implemented security measures
- Plan for regular updates to the threat model as the application or environment evolves
Continuous Improvement Phase
- Establish continuous monitoring to detect new threats using SIEM tools
- Schedule periodic reviews
- Encourage ongoing security training for the development and operations teams
Secure Coding Practices
Secure coding practices are vital for safeguarding full-stack applications from threats and vulnerabilities. In this section, we'll dive into guidelines that cover every layer of the stack, helping developers build resilient applications that can handle both current and future security challenges.
Table 1. Secure coding practices for full-stack applications
| Category | Best Practices | Tools/Techniques |
| Input validation | - Validate all inputs to prevent common vulnerabilities (e.g., cross-site scripting, SQL injection) - Use strict type, format, and content checks |
- OWASP Validator - sanitize-html - Joi (for Node.js) |
| Authentication | - Implement strong multi-factor authentication - Securely manage session tokens and cookies - Utilize secure password storage techniques |
- OAuth - JSON Web Token (JWT) |
| Authorization | - Enforce the principle of least privilege - Use role-based or attribute-based access controls - Regularly review and update access controls |
- Spring Security - CASBIN (for Go and Node.js) |
| Data protection | - Encrypt sensitive data at rest and in transit - Use secure data serialization and deserialization methods - Apply data masking |
- Transport layer security - Advanced Encryption Standard - Data masking tools |
| API security | - Secure API endpoints against common attacks - Implement rate limiting - Use API gateways for additional security layers |
- API gateways - JWT - OAuth |
| Error handling | - Avoid detailed error messages revealing system information - Implement centralized error handling to prevent leakage |
- Custom error handlers - Logging libraries |
| Logging and monitoring | - Log all access and changes to sensitive data - Ensure logs do not contain sensitive information - Use real-time monitoring for security alerts |
- SIEM systems - ELK stack (Elasticsearch, Logstash, Kibana) |
| Configuration management | - Secure all application and server configurations - Automate configurations - Use configuration management tools for consistency |
- Configuration management tools (e.g., Ansible) |
| Security testing | - Perform static and dynamic analysis - Regularly conduct penetration testing - Utilize automated security scanning tools |
- SAST and DAST tools - Penetration testing services |
| Container security | - Use trusted base images - Secure runtime configurations - Ensure strong container isolation - Regularly scan for vulnerabilities |
- Docker Bench for Security - Clair |
| Network security | - Isolate sensitive components using network segmentation - Use firewalls and intrusion detection systems - Secure communication channels - Enforce zero-trust architectures |
- Firewalls - Intrusion detection system/intrusion prevention system - VPNs |
| Incident response | - Develop and update incident response plans - Train staff on detection and response - Simulate security incidents |
- NIST Incident Response - NCSC Cyber Incident Response |
Authentication and Authorization Mechanisms
Authentication and authorization are foundational to securing full-stack applications. Implementing robust authentication and authorization mechanisms is essential for protecting sensitive data and functionalities in full-stack applications.
Implementing Authentication
Authentication verifies a user's identity to ensure they are who they claim to be. Core methods of authentication include username/password, multi-factor authentication (MFA), certificate based, single sign-on (SSO), token based, and public key infrastructure (PKI). Implementing authentication methods involves adopting best practices that ensure security and user trust:
- Developers should leverage strong authentication protocols such as OAuth2 and JWT for secure and scalable authentication processes.
- Enforcing MFA adds an extra layer of security, reducing the risk of unauthorized access.
- Passwords must be hashed using strong algorithms like bcrypt before storage, and make sure session management is secure enough to prevent session hijacking.
- Developers should also ensure that all authentication-related communication is encrypted using HTTPS to avoid interception.
- Implement account lock-out policies to prevent brute force attacks.
- Regularly review and update your authentication methods to stay ahead of emerging threats and vulnerabilities, ensuring the application remains secure.
Table 2. Pros and cons of authentication methods
| Method | Pros | Cons |
| Password based | - Simple to understand and implement - Ubiquitous, supported by most systems |
- Vulnerable to brute-force and dictionary attacks - Requires strong password policies and secure storage |
| MFA | - Adds an extra layer of security - Significantly reduces risk of compromised accounts |
- Can be cumbersome for users - Additional costs for implementation and maintenance - Dependent on user's access to a second factor (e.g., phone) |
| Token based | - Stateless and scalable - Supports SSO |
- Token theft can lead to unauthorized access - Token management and storage complexity - Requires secure token issuance and validation |
| Certificate based | - Strong security with digital certificates - Suitable for device and user authentication |
- Complexity in managing certificates - Certificate issuance and revocation processes - High initial set-up costs |
| SSO | - Convenient for users, with one login for multiple systems - Reduces password fatigue |
- Single point of failure - Complex implementation and configuration - Dependency on identity providers |
| Federated identity management | - Simplifies user management across systems - Reduces password fatigue with SSO |
- Requires trust between federated partners - Complex implementation and configuration - Dependency on identity providers |
| PKI | - Strong security with cryptographic keys - Suitable for secure communications and data integrity |
- Complex key management - High initial set-up and maintenance costs - Requires secure key storage and distribution |
Implementing Authorization
Authorization determines what an authenticated user is allowed to do within a system. Methods of authorization are role-based access control (RBAC), attribute-based access control (ABAC), and permission-based access control (PBAC). Implementing authorization methods in applications requires thoughtful planning to ensure users have the right access levels based on their roles and responsibilities:
- Developers should adopt effective authorization methods to manage permissions efficiently, ensuring that users have only necessary access.
- Following the principle of least privilege by granting minimal permissions helps reduce the risk of unauthorized actions.
- Securing APIs and back-end services by validating tokens and user roles for every request is critical.
- Regularly auditing permissions and access logs helps identify and fix any unauthorized access attempts.
- Using access reconciliation processes to regularly check that user permissions match their current roles ensures that access rights are always up to date and adhere to the principle of least privilege.
- Centralizing and keeping authorization logic consistent across the application boosts security and simplifies management.
Table 3. Pros and cons of authorization methods
| Method | Pros | Cons |
| RBAC | - Simple and easy to manage - Centralized control over user permissions - Reduces administrative overhead |
- Can become complex with many roles - Roles can become outdated or overly broad |
| ABAC | - Highly flexible - Can handle complex access policies - Context aware |
- Complex to implement and manage - Performance overhead due to policy evaluation |
| PBAC | - Centralized management of access policies - Highly adaptable to different contexts and environments |
- Requires sophisticated policy management tools - Potential performance impact |
Database Security and Data Protection
Database security and data protection are crucial aspects of managing and safeguarding information within an organization. They involve a range of practices and technologies designed to protect databases from unauthorized access, use, or modification as well as disclosure, disruption, or destruction. Understanding database security and protection is crucial for developers to ensure the integrity, confidentiality, and availability of data, which protects against breaches, ensures compliance, and maintains user trust.
Table 4. Database security and data protection best practices
| Category | Best Practices |
| Database access control | - Implement RBAC - Use MFA - Review and update access permissions regularly |
| Data encryption | - Encrypt sensitive data at rest and in transit using strong protocols - Use key management solutions to secure key handling |
| Data masking and redaction | - Use dynamic data masking for real-time protection - Apply static masking in test environments |
| SQL injection prevention | - Use prepared statements and parameterized queries - Conduct regular code reviews and security testing - Employ web application firewalls to block SQL injection attacks |
| Backup and recovery | - Implement automated and regular backups - Store backups securely, possibly off site - Regularly test recovery procedures to ensure effective data restoration |
| Data privacy regulations compliance | - Stay informed about data protection laws (e.g., GDPR, HIPAA) - Implement compliance policies and technologies - Regularly audit practices and conduct training |
Cloud Security Considerations
Cloud security considerations are crucial for protecting data, ensuring compliance, and maintaining service reliability in cloud environments. They guide developers in securing application design, deployment, and management, ultimately safeguarding against breaches and ensuring user trust. Key cloud security considerations include:
- Shared responsibility model – Understand and define what security components are managed by the cloud provider versus those managed by your team.
- Cloud-specific identity and access management (IAM) – Utilize cloud provider IAM tools to manage user identities and permissions securely.
- Data residency and sovereignty – Comply with laws and regulations regarding where data is stored and how it is transferred across borders.
- Cloud network security – Implement virtual private clouds and private subnets to control network traffic. Use security groups and network ACLs to enforce security.
- Cloud compliance and legal considerations – Adhere to cloud-specific regulations and standards to ensure compliance across all operational regions.
- Cloud threat detection and monitoring – Deploy cloud-native monitoring solutions that offer integration with cloud platforms for real-time threat detection and security logging.
- Cloud incident response – Develop cloud-specific incident response protocols leveraging cloud services for faster and more scalable responses.
- Cloud disaster recovery – Utilize cloud infrastructure to set up and manage disaster recovery solutions that are robust and geographically distributed.
- Cloud security posture management (CSPM) – Use CSPM tools to continuously evaluate and manage the cloud security posture across various cloud environments.
Conclusion
Securing full-stack applications is increasingly complex but crucial in today's digital world. As technology advances and threats grow more sophisticated, robust security measures across all layers of your stack are vital. Organizations must foster a culture of security, continuously update practices, and stay proactive. The future of full-stack security will be shaped by AI for better threat detection, zero-trust models for continuous verification, and evolving practices for cloud-native technologies and DevSecOps integration.
Additional resources:
- Cloud-Application Security Patterns and Anti-Patterns by Samir Behara, DZone Refcard
- Identity and Access Management Core Practices by Apostolos Giannakidis, DZone Refcard
- "Take Control of Your Application Security" by Josephine Eskaline Joyce, Deepika Kothamasu, and Swathi Pemmaraju
- "Securing Cloud Infrastructure: Leveraging Key Management Technologies" by Josephine Eskaline Joyce and Shikha Maheshwari
This is an excerpt from DZone's 2024 Trend Report, Enterprise Security: Reinforcing Enterprise Application Defense.
Read the Free Report
Opinions expressed by DZone contributors are their own.

Comments