DTrace Revisited: Advanced Debugging Techniques
Explore the power of DTrace for system debugging and optimization in this comprehensive guide on its capabilities, performance, and applications.
Join the DZone community and get the full member experience.
Join For FreeWhen we think of debugging, we think of breakpoints in IDEs, stepping over, inspecting variables, etc. However, there are instances where stepping outside the conventional confines of an IDE becomes essential to track and resolve complex issues. This is where tools like DTrace come into play, offering a more nuanced and powerful approach to debugging than traditional methods. This blog post delves into the intricacies of DTrace, an innovative tool that has reshaped the landscape of debugging and system analysis.
DTrace Overview
DTrace was first introduced by Sun Microsystems in 2004, DTrace quickly garnered attention for its groundbreaking approach to dynamic system tracing. Originally developed for Solaris, it has since been ported to various platforms, including MacOS, Windows, and Linux. DTrace stands out as a dynamic tracing framework that enables deep inspection of live systems – from operating systems to running applications. Its capacity to provide real-time insights into system and application behavior without significant performance degradation marks it as a revolutionary tool in the domain of system diagnostics and debugging.
Understanding DTrace’s Capabilities
DTrace, short for Dynamic Tracing, is a comprehensive toolkit for real-time system monitoring and debugging, offering an array of capabilities that span across different levels of system operation. Its versatility lies in its ability to provide insights into both high-level system performance and detailed process-level activities.
System Monitoring and Analysis
At its core, DTrace excels in monitoring various system-level operations. It can trace system calls, file system activities, and network operations. This enables developers and system administrators to observe the interactions between the operating system and the applications running on it. For instance, DTrace can identify which files a process accesses, monitor network requests, and even trace system calls to provide a detailed view of what's happening within the system.
Process and Performance Analysis
Beyond system-level monitoring, DTrace is particularly adept at dissecting individual processes. It can provide detailed information about process execution, including CPU and memory usage, helping to pinpoint performance bottlenecks or memory leaks. This granular level of detail is invaluable for performance tuning and debugging complex software issues.
Customizability and Flexibility
One of the most powerful aspects of DTrace is its customizability. With a scripting language based on C syntax, DTrace allows the creation of customized scripts to probe specific aspects of system behavior. This flexibility means that it can be adapted to a wide range of debugging scenarios, making it a versatile tool in a developer’s arsenal.
Real-World Applications
In practical terms, DTrace can be used to diagnose elusive performance issues, track down resource leaks, or understand complex interactions between different system components. For example, it can be used to determine the cause of a slow file operation, analyze the reasons behind a process crash, or understand the system impact of a new software deployment.
Performance and Compatibility of DTrace
A standout feature of DTrace is its ability to operate with remarkable efficiency. Despite its deep system integration, DTrace is designed to have minimal impact on overall system performance. This efficiency makes it a feasible tool for use in live production environments, where maintaining system stability and performance is crucial. Its non-intrusive nature allows developers and system administrators to conduct thorough debugging and performance analysis without the worry of significantly slowing down or disrupting the normal operation of the system.
Cross-Platform Compatibility
Originally developed for Solaris, DTrace has evolved into a cross-platform tool, with adaptations available for MacOS, Windows, and various Linux distributions. Each platform presents its own set of features and limitations. For instance, while DTrace is a native component in Solaris and MacOS, its implementation in Linux often requires a specialized build due to kernel support and licensing considerations.
Compatibility Challenges on MacOS
On MacOS, DTrace's functionality intersects with System Integrity Protection (SIP), a security feature designed to prevent potentially harmful actions. To utilize DTrace effectively, users may need to disable SIP, which should be done with caution. This process involves booting into recovery mode and executing specific commands, a step that highlights the need for a careful approach when working with such powerful system-level tools.
We can disable SIP using the command:
csrutil disable
We can optionally use a more refined approach of enabling SIP without dtrace using the following command:
csrutil enable --without dtrace Be extra careful when issuing these commands and when working on machines where dtrace is enabled. Back up your data properly!
Customizability and Flexibility of DTrace
A key feature that sets DTrace apart in the realm of system monitoring tools is its highly customizable nature. DTrace employs a scripting language that bears similarity to C syntax, offering users the ability to craft detailed and specific diagnostic scripts. This scripting capability allows for the creation of custom probes that can be fine-tuned to target particular aspects of system behavior, providing precise and relevant data.
Adaptability to Various Scenarios
The flexibility of DTrace's scripting language means it can adapt to a multitude of debugging scenarios. Whether it's tracking down memory leaks, analyzing CPU usage, or monitoring I/O operations, DTrace can be configured to provide insights tailored to the specific needs of the task. This adaptability makes it an invaluable tool for both developers and system administrators who require a dynamic approach to problem-solving.
Examples of Customizable Probes
Users can define probes to monitor specific system events, track the behavior of certain processes, or gather data on system resource usage. This level of customization ensures that DTrace can be an effective tool in a variety of contexts, from routine maintenance to complex troubleshooting tasks. The following is a simple "Hello, world!" dtrace probe:
sudo dtrace -qn 'syscall::write:entry, syscall::sendto:entry /pid == $target/ { printf("(%d) %s %s", pid, probefunc, copyinstr(arg1)); }' -p 9999
The kernel is instrumented with hooks that match various callbacks. dtrace connects to these hooks and can perform interesting tasks when these hooks are triggered. They have a naming convention, specifically provider:module:function:name. In this case, the provider is a system call in both cases. We have no module so we can leave that part blank between the colon (:) symbols. We grab a write operation and sendto entries. When an application writes or tries to send a packet, the following code event will trigger.
These things happen frequently, which is why we restrict the process ID to the specific target with pid == $target. This means the code will only trigger for the PID passed to us in the command line. The rest of the code should be simple for anyone with basic C experience: it's a printf that would list the processes and the data passed.
Real-World Applications of DTrace
DTrace's diverse capabilities extend far beyond theoretical use, playing a pivotal role in resolving real-world system complexities. Its ability to provide deep insights into system operations makes it an indispensable tool in a variety of practical applications.
To get a sense of how DTrace can be used, we can use the man -k dtrace command whose output on my Mac is below:
bitesize.d(1m) - analyse disk I/O size by process. Uses DTrace
cpuwalk.d(1m) - Measure which CPUs a process runs on. Uses DTrace
creatbyproc.d(1m) - snoop creat()s by process name. Uses DTrace
dappprof(1m) - profile user and lib function usage. Uses DTrace
dapptrace(1m) - trace user and library function usage. Uses DTrace
dispqlen.d(1m) - dispatcher queue length by CPU. Uses DTrace
dtrace(1) - dynamic tracing compiler and tracing utility
dtruss(1m) - process syscall details. Uses DTrace
errinfo(1m) - print errno for syscall fails. Uses DTrace
execsnoop(1m) - snoop new process execution. Uses DTrace
fddist(1m) - file descriptor usage distributions. Uses DTrace
filebyproc.d(1m) - snoop opens by process name. Uses DTrace
hotspot.d(1m) - print disk event by location. Uses DTrace
iofile.d(1m) - I/O wait time by file and process. Uses DTrace
iofileb.d(1m) - I/O bytes by file and process. Uses DTrace
iopattern(1m) - print disk I/O pattern. Uses DTrace
iopending(1m) - plot number of pending disk events. Uses DTrace
iosnoop(1m) - snoop I/O events as they occur. Uses DTrace
iotop(1m) - display top disk I/O events by process. Uses DTrace
kill.d(1m) - snoop process signals as they occur. Uses DTrace
lastwords(1m) - print syscalls before exit. Uses DTrace
loads.d(1m) - print load averages. Uses DTrace
newproc.d(1m) - snoop new processes. Uses DTrace
opensnoop(1m) - snoop file opens as they occur. Uses DTrace
pathopens.d(1m) - full pathnames opened ok count. Uses DTrace
perldtrace(1) - Perl's support for DTrace
pidpersec.d(1m) - print new PIDs per sec. Uses DTrace
plockstat(1) - front-end to DTrace to print statistics about POSIX mutexes and read/write locks
priclass.d(1m) - priority distribution by scheduling class. Uses DTrace
pridist.d(1m) - process priority distribution. Uses DTrace
procsystime(1m) - analyse system call times. Uses DTrace
rwbypid.d(1m) - read/write calls by PID. Uses DTrace
rwbytype.d(1m) - read/write bytes by vnode type. Uses DTrace
rwsnoop(1m) - snoop read/write events. Uses DTrace
sampleproc(1m) - sample processes on the CPUs. Uses DTrace
seeksize.d(1m) - print disk event seek report. Uses DTrace
setuids.d(1m) - snoop setuid calls as they occur. Uses DTrace
sigdist.d(1m) - signal distribution by process. Uses DTrace
syscallbypid.d(1m) - syscalls by process ID. Uses DTrace
syscallbyproc.d(1m) - syscalls by process name. Uses DTrace
syscallbysysc.d(1m) - syscalls by syscall. Uses DTrace
topsyscall(1m) - top syscalls by syscall name. Uses DTrace
topsysproc(1m) - top syscalls by process name. Uses DTrace
Tcl_CommandTraceInfo(3tcl), Tcl_TraceCommand(3tcl), Tcl_UntraceCommand(3tcl) - monitor renames and deletes of a command
bitesize.d(1m) - analyse disk I/O size by process. Uses DTrace
cpuwalk.d(1m) - Measure which CPUs a process runs on. Uses DTrace
creatbyproc.d(1m) - snoop creat()s by process name. Uses DTrace
dappprof(1m) - profile user and lib function usage. Uses DTrace
dapptrace(1m) - trace user and library function usage. Uses DTrace
dispqlen.d(1m) - dispatcher queue length by CPU. Uses DTrace
dtrace(1) - dynamic tracing compiler and tracing utility
dtruss(1m) - process syscall details. Uses DTrace
errinfo(1m) - print errno for syscall fails. Uses DTrace
execsnoop(1m) - snoop new process execution. Uses DTrace
fddist(1m) - file descriptor usage distributions. Uses DTrace
filebyproc.d(1m) - snoop opens by process name. Uses DTrace
hotspot.d(1m) - print disk event by location. Uses DTrace
iofile.d(1m) - I/O wait time by file and process. Uses DTrace
iofileb.d(1m) - I/O bytes by file and process. Uses DTrace
iopattern(1m) - print disk I/O pattern. Uses DTrace
iopending(1m) - plot number of pending disk events. Uses DTrace
iosnoop(1m) - snoop I/O events as they occur. Uses DTrace
iotop(1m) - display top disk I/O events by process. Uses DTrace
kill.d(1m) - snoop process signals as they occur. Uses DTrace
lastwords(1m) - print syscalls before exit. Uses DTrace
loads.d(1m) - print load averages. Uses DTrace
newproc.d(1m) - snoop new processes. Uses DTrace
opensnoop(1m) - snoop file opens as they occur. Uses DTrace
pathopens.d(1m) - full pathnames opened ok count. Uses DTrace
perldtrace(1) - Perl's support for DTrace
pidpersec.d(1m) - print new PIDs per sec. Uses DTrace
plockstat(1) - front-end to DTrace to print statistics about POSIX mutexes and read/write locks
priclass.d(1m) - priority distribution by scheduling class. Uses DTrace
pridist.d(1m) - process priority distribution. Uses DTrace
procsystime(1m) - analyse system call times. Uses DTrace
rwbypid.d(1m) - read/write calls by PID. Uses DTrace
rwbytype.d(1m) - read/write bytes by vnode type. Uses DTrace
rwsnoop(1m) - snoop read/write events. Uses DTrace
sampleproc(1m) - sample processes on the CPUs. Uses DTrace
seeksize.d(1m) - print disk event seek report. Uses DTrace
setuids.d(1m) - snoop setuid calls as they occur. Uses DTrace
sigdist.d(1m) - signal distribution by process. Uses DTrace
syscallbypid.d(1m) - syscalls by process ID. Uses DTrace
syscallbyproc.d(1m) - syscalls by process name. Uses DTrace
syscallbysysc.d(1m) - syscalls by syscall. Uses DTrace
topsyscall(1m) - top syscalls by syscall name. Uses DTrace
topsysproc(1m) - top syscalls by process name. Uses DTrace
There's a lot here; we don't need to read everything. The point is that when you run into a problem you can just search through this list and find a tool dedicated to debugging that problem.
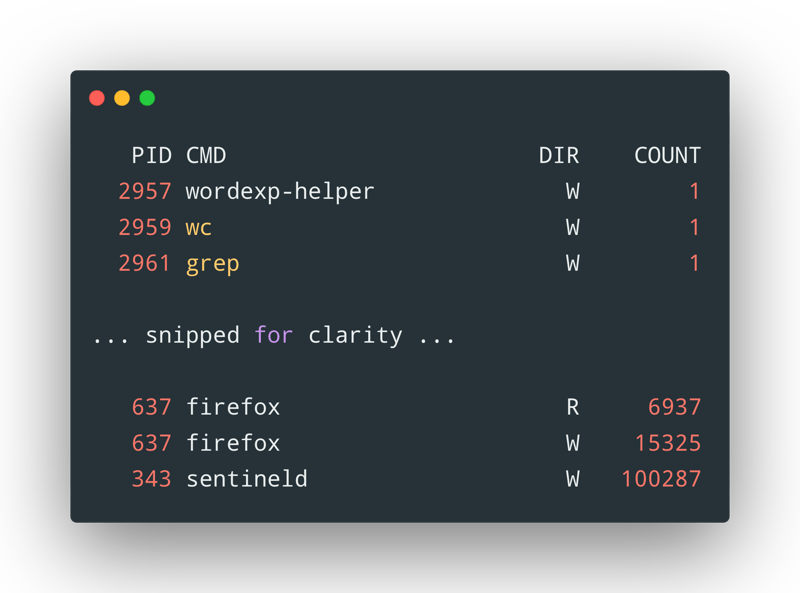
Let’s say you're facing elevated disk write issues that are causing the performance of your application to degrade. . . But is it your app at fault or some other app?
rwbypid.d can help you with that: it can generate a list of processes and the number of calls they have for read/write based on the process ID as seen in the following screenshot:
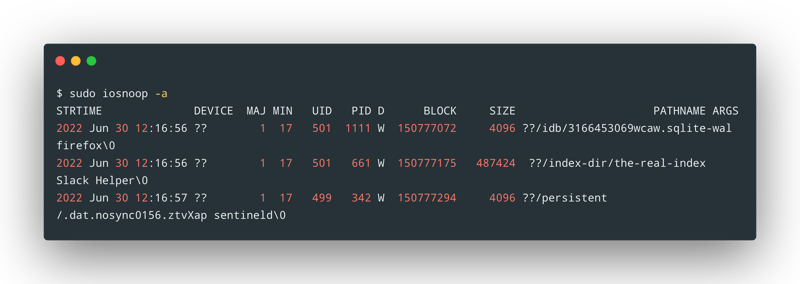
We can use this information to better understand IO issues in our code or even in 3rd party applications/libraries. iosnoop is another tool that helps us track IO operations but with more details:
In diagnosing elusive system issues, DTrace shines by enabling detailed observation of system calls, file operations, and network activities. For instance, it can be used to uncover the root cause of unexpected system behaviors or to trace the origin of security breaches, offering a level of detail that is often unattainable with other debugging tools.
Performance optimization is the main area where DTrace demonstrates its strengths. It allows administrators and developers to pinpoint performance bottlenecks, whether they lie in application code, system calls, or hardware interactions. By providing real-time data on resource usage, DTrace helps in fine-tuning systems for optimal performance.
Final Words
In conclusion, DTrace stands as a powerful and versatile tool in the realm of system monitoring and debugging. We've explored its broad capabilities, from in-depth system analysis to individual process tracing, and its remarkable performance efficiency that allows for its use in live environments. Its cross-platform compatibility, coupled with the challenges and solutions specific to MacOS, highlights its widespread applicability. The customizability through scripting provides unmatched flexibility, adapting to a myriad of diagnostic needs. Real-world applications of DTrace in diagnosing system issues and optimizing performance underscore its practical value.
DTrace's comprehensive toolkit offers an unparalleled window into the inner workings of systems, making it an invaluable asset for system administrators and developers alike. Whether it's for routine troubleshooting or complex performance tuning, DTrace provides insights and solutions that are essential in the modern computing landscape.
Published at DZone with permission of Shai Almog, DZone MVB. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments