Don’t Get Hacked! Essential Cybersecurity Tips You Need To Know
Exploring common cybersecurity threats online and teaching best practices to build protections for yourself and those most important to you.
Join the DZone community and get the full member experience.
Join For FreeTechnology in the digital age has revolutionized our lives. However, this convenience comes with a growing threat: cybercrime. Malicious actors, ranging from petty thieves to sophisticated cybercriminals, operate online, seeking to exploit vulnerabilities and steal sensitive information, financial data, and even identities.
From online banking and shopping to social media and remote work, the internet has become an essential part of our daily routines. What does it mean when your online identity is turned against you? Or when you need to prove your own identity to regain control of tools you previously assumed were solely there to make your life easier?
This article equips you with the fundamental knowledge and practices to protect yourself online. Some of the topics I’ll address are the core principles of cybersecurity, exploring strong passwords, two-factor authentication, software updates, and securing your devices. In particular, I’ll deep dive into how to identify and avoid phishing attacks and scams. Finally, I want you to leave this article to understand the importance of online privacy and data protection, not just for yourself but for protecting your families and broader social networks, as well.
Building a Robust Defense: Passwords and Authentication
The first line of defense in cybersecurity is access control. Strong passwords and robust authentication methods are crucial for this. A weak password, like your birthday or pet's name, is easily compromised by automated programs or even educated guesses.
Here are some key principles for creating unbreakable passwords:
- Length is key: Aim for at least 12-15 characters.
- Embrace diversity: Use a combination of uppercase and lowercase letters, numbers, and symbols.
- Avoid predictability: Steer clear of dictionary words, keyboard patterns (e.g., "qwerty"), and personal details.
- Uniqueness is essential: Don't reuse passwords across different accounts.
Remembering numerous complex passwords can be a challenge. Password managers offer a solution that can prevent you from tearing out your hair trying to remember each service’s login credentials. These secure applications store your passwords and can even generate strong, unique passwords for each of your accounts. In its typically humorous fashion, this XKCD comic has some surprisingly poignant and useful tips, which can be specifically useful for generating and remembering the password for a password manager.
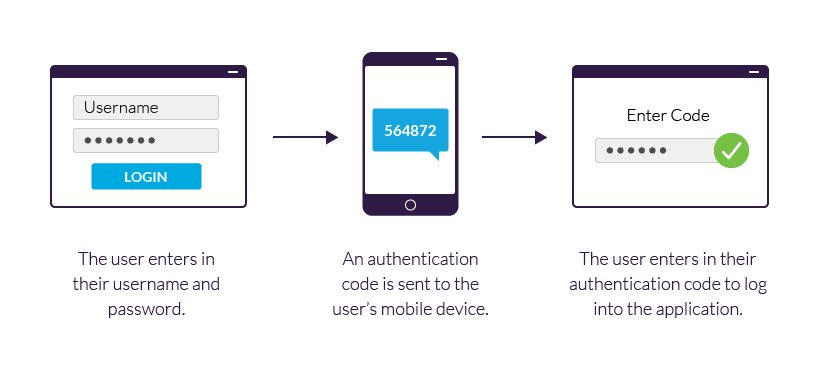
Two-factor authentication (2FA) adds another layer of security by requiring a second verification step after entering your password. This could be a code sent to your phone via text message, a fingerprint scan, or a facial recognition prompt. Enabling 2FA significantly reduces the risk of unauthorized access, even if your password is compromised.
Keeping Your Software Updated: Patching the Gaps
Unpatched software vulnerabilities are like cracks in your digital armor. Hackers constantly scan for these weaknesses to exploit them and gain access to your system. Software updates, often free and readily available, patch these vulnerabilities, significantly hindering attackers.
Here are some best practices for software updates:
- Enable automatic updates: Most software allows you to configure automatic updates for the operating system, applications, and web browsers. This ensures you're always protected by the latest security patches.
- Stay informed: Keep an eye out for critical security updates that require manual installation.
- Prioritize updates for security software: Regularly update your antivirus, anti-malware, and firewall software to benefit from the latest threat detection capabilities.
Securing Your Devices: Beyond the Desktop
Our digital lives extend beyond desktops and laptops. Smartphones and tablets hold a wealth of personal information and require equal attention to security.
Here's how to safeguard your mobile devices:
- Use strong passwords or PINs: Don't underestimate the importance of a secure screen lock on your phone or tablet.
- Download apps only from trusted sources: App stores vet apps for security risks, so avoid downloading from unknown sources.
- Be cautious with app permissions: Grant apps only the permissions they absolutely need to function.
- Enable remote wipe: This allows you to erase all data from your device remotely in case it gets lost or stolen.
One point, often overlooked, is that public Wi-Fi networks may be convenient but are often unsecured. Avoid accessing sensitive information or financial accounts while connected to public Wi-Fi. If necessary, consider using a virtual private network (VPN) to encrypt your internet traffic on public networks.
Recognizing Deception: Phishing Attacks and Scams
Phishing attacks attempt to trick you into revealing personal information or clicking on malicious links. They often come disguised as emails, text messages, or fake websites imitating legitimate entities like banks, social media platforms, or even your boss.
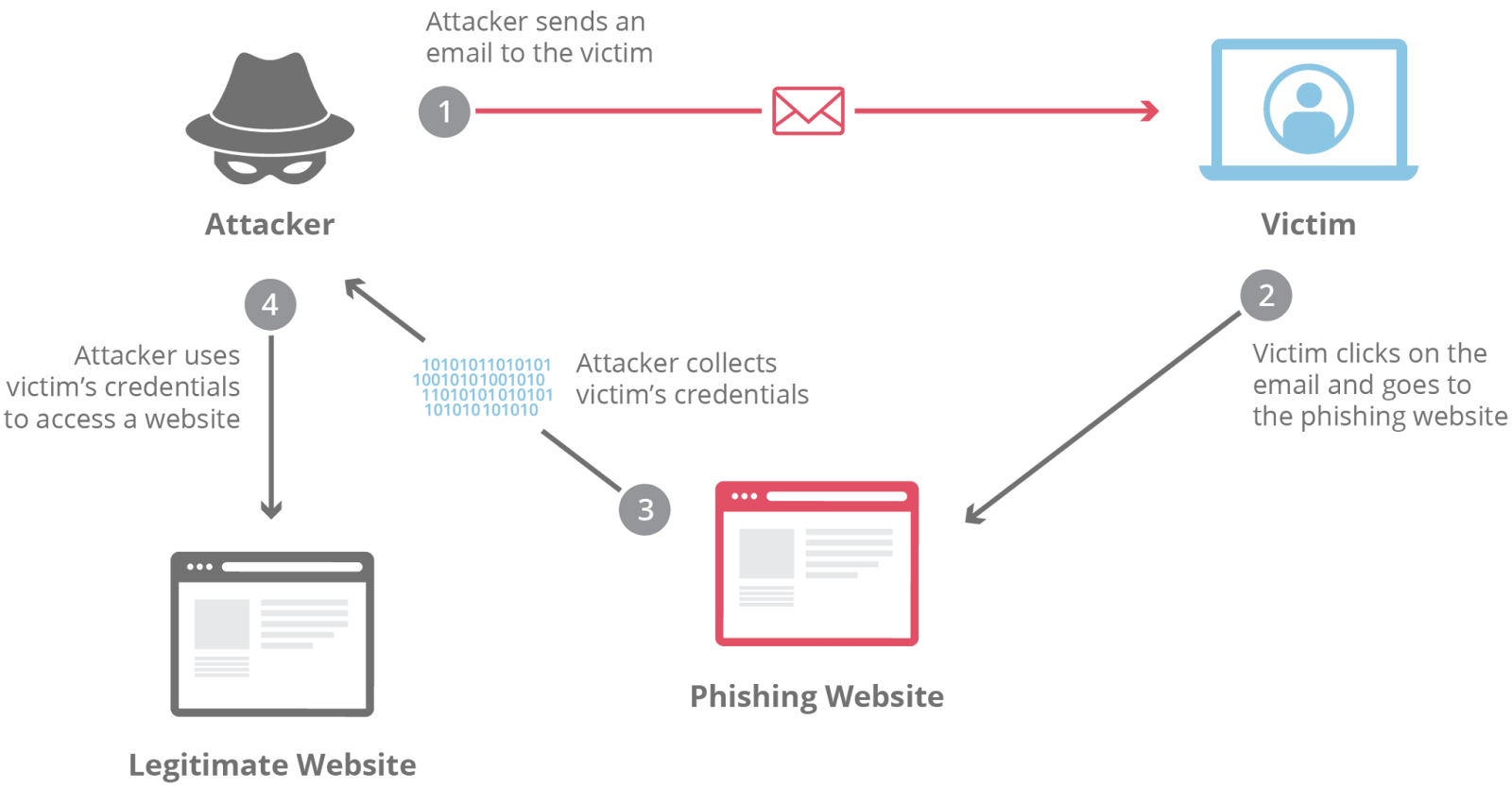
Here's how to identify phishing attempts:
- Suspicious sender addresses: Check the sender's email address carefully for typos or inconsistencies.
- Urgency and pressure tactics: Phishing emails often create a sense of urgency or pressure to compel you to act without thinking critically.
- Grammatical errors and poor formatting: Legitimate companies usually maintain high standards for email communication.
- Unrealistic offers or threats: Be wary of emails offering unbelievable deals or threatening dire consequences if you don't comply.
- Hover over links before clicking: Don't click on suspicious links directly. Hover your mouse cursor over the link to see the actual destination URL in the bottom left corner of your browser window.
If you suspect a phishing attempt, don't respond to the email or click on any links. Many email providers/websites have a "report phishing" button. Use this option to report the attempt and help prevent others from falling victim.
Safeguarding Your Privacy: Controlling Your Digital Footprint
The vast amount of data we generate online creates a digital footprint, a trail of our activities and preferences. While some data collection is necessary for certain online services, it's important to be mindful of how much information you share and with whom.
Here are some steps you can take to protect your online privacy:
- Review your privacy settings on social media platforms and other online accounts. Limit the information that is publicly visible and control who can see your posts and activity.
- Be cautious about what information you share online. Avoid posting personal details like your home address, phone number, or birthdate publicly.
- Beware of data breaches. Enable data breach notifications for the services you use and consider using a service that monitors your email address for breaches.
Data breaches can compromise your personal information. Strong passwords and not reusing them across accounts help mitigate this risk. However, it's also important to be aware of data breaches and take steps to protect yourself if your information is exposed.
Here's what to do in case of a data breach:
- Change your passwords immediately. If your login credentials are compromised in a data breach, change your passwords for the affected accounts and any other accounts where you've used the same password.
- Monitor your accounts for suspicious activity. Be vigilant for any unauthorized transactions or changes to your account information.
- Consider credit freezing or monitoring. Depending on the severity of the data breach, you may want to consider placing a credit freeze on your accounts or enrolling in credit monitoring services.
Embracing a Secure Digital Lifestyle
The digital age offers immense benefits, but it also comes with inherent risks. By following the cybersecurity essentials outlined in this article, you can significantly reduce your risk of falling victim to cyberattacks and protect your online privacy. Remember, cybersecurity is an ongoing process. Stay informed about evolving threats, update your software regularly, and be vigilant about the information you share online. By embracing these practices, you can navigate the digital world with confidence and enjoy the vast possibilities it offers.
Opinions expressed by DZone contributors are their own.

Comments