Distributed PKI vs Traditional PKI
Is Blockchain-based PKI a game-changing new technology or a solution that misses the mark?
Join the DZone community and get the full member experience.
Join For FreeWith the rise of cryptocurrency, blockchain technology has grown from an obscure niche solution to one of the most hyped new technologies of the last decade. Enthusiasts are claiming blockchain will revolutionize entire industries. Traditional PKI solutions and the Certificate Authority (CA) companies delivering these traditional PKI solutions are no exception.
Several blockchain-based PKI solutions have been proposed, and a few have been implemented. The groups developing distributed, or blockchain-based PKI solutions, claim they will replace traditional systems and solve problems with “old school” PKI implementations.
Hype vs Reality of Distributed PKI
Distributed PKI pundits point out a number of failures with traditional PKI solutions and claim that distributed PKI solutions address these shortcomings. Understanding the promise of distributed PKI requires a close examination of these claims.
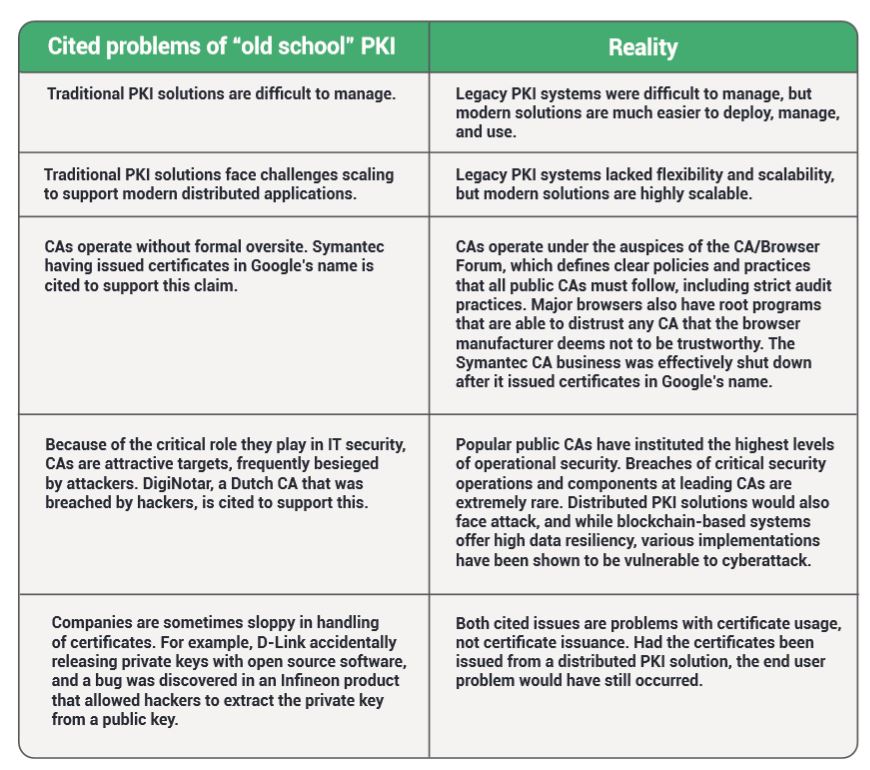
These arguments conflate criticism of the fundamental architecture with criticism of business models, common practices, or even individual companies. It is important to compartmentalize these concerns. While indeed the public CA DigiNotar was hacked, it takes a vast leap to conclude that one organization’s failure nearly a decade ago equates to the wholesale dismissal of an entire technology paradigm.
Note also that many of the above arguments are flawed in their facts or their reasoning. For example, Symantec’s mis-issuance of certificates in Google’s name was one of the key incidents that ultimately led to Google’s deprecation of trust for Symantec’s roots and forced Symantec to completely exit the digital certificate business. So oversight and accountability certainly were present in that case.
Claimed Advantages of Blockchain-Based PKI
Distributed PKI advocates say that because blockchain solutions run on tens of thousands of computers simultaneously, their design eliminates the risks of “Old School PKI systems” because:
- Blockchain is an open, transparent, and secure architecture.
- Anyone can read all of its contents; companies don’t need to put their trust in CAs
- If someone issues a cert in someone else’s name, it’s seen by everyone on the chain
CAs have implemented certificate transparency logs on which all issued certificates are published, and this provides the security advantages claimed with distributed PKI.
The Reality of Distributed PKI
Distributed PKI advocates focus heavily on supposed weaknesses in traditional PKI systems, but in doing so fail to address critical components of any PKI implementation. A modern PKI solution must provide many critical capabilities that are not clearly addressed by blockchain-based systems.
The Need for a Centralized Authority
Certificate Authority companies provide issuance of certificates for both public and private use cases. The name, Certificate Authority derives from the role these companies play in validating and authenticating requests for digital certificates. Before a certificate can be issued, it is critical to validate that the requester is, in fact, the person claimed to be. For public certificate issuance, CAs follow CA/Browser Forum rules in verifying the identity of the requestor. These rules specify multiple levels of trust with more extensive validation requirements for higher levels of trust. At a minimum, a requestor must validate control of the domain for which certificate is being issued. For higher levels of trust, additional steps are required, potentially including a phone call and providing legal documents to prove identity.
For distributed PKI solutions to be widely usable, a method of validating requestors is needed. This is required for both public and private PKI solutions. For private certificate issuance, this function could potentially be performed “on the blockchain” using smart contracts. For public certificate issuance this would have to be performed “off the blockchain.”
Who Holds the Keys?
The entire operation of any PKI solution depends upon protecting the private keys for the root certificate in the certificate hierarchy. The importance of this requirement cannot be overstated.
If the private root keys are stolen, whoever has access to those keys can undermine the entire PKI operation. CAs go to great lengths to protect these keys, storing them in HSMs, highly secured hardware located in data centers protected by both physical security and cybersecurity measures and generally stored offline. CAs have decades of experience and investment in secure measures and protocols to ensure the safety of these most critical assets.
To ensure the security of a distributed PKI solution, similar measures are required and would greatly limit the distributed nature of a distributed PKI solution. While some aspects of the PKI process could utilize the blockchain, any signing operation requiring root keys would have to be performed at a central location and off the blockchain.
Private Ecosystem Enablement
Many enterprises require a private PKI ecosystem for user authentication certificates to replace password-based logins, device identity certificates for IoT device authentication, and process authentication certificates for DevOps use cases. Enterprises require security and privacy that would be difficult, if not impossible, to maintain on a public blockchain. For example, enterprises may wish to keep details on the number of certificates issued, who they were issued to, and other details private, eliminating the option to use an open/public blockchain.
While a private blockchain could be utilized, this approach is impractical. One of the major benefits of a public blockchain is that the blockchain is run on hundreds if not thousands of nodes. The cost of spinning up a private blockchain of this scale would defeat any cost savings of using a blockchain. A centralized PKI solution would be much more cost-effective.
Integration With Enterprise Solutions
PKI is a tool used by enterprises, government IT systems, and other large-scale identity systems. The success of the PKI systems depends upon the ease with which it can integrate with these systems. CAs have been developing automation tools and enterprises have been integrating with these solutions for decades now. For distributed PKI solutions to be viable, they will need to enable standard PKI protocols, some of which assume a centralized application. Migrating existing solutions to distributed PKI will require a tremendous amount of integration work, and for many use cases, this simply is not viable.
Use Cases for Distributed PKI
While distributed PKI is unlikely to become the solution of choice for most systems, there are some use cases in which blockchain-based implementations may provide a very good tool to implement some of the elements of a PKI solution.
Certificate Transparency Logs
Certificate authorities publish all issued public certificates on Certificate Transparency (CT) logs. This enables transparency and accountability and allows audit of certificate issuance practices to ensure compliance with CA/Browser Forum requirements. CT logs are implemented as a Merkle-tree which, like a blockchain, labels nodes with cryptographic hashes to ensure integrity.
Blockchain would be an ideal alternative for implementing certificate transparency logs for private PKI, or even for future versions of public CT logs.
Blockchain-Based Certificate Revocation
Certificate revocation checking is performed by distributing Certificate Revocation Lists (CRLs) that can be checked for revoked certificates, or more commonly using Online Certificate Status Protocol (OCSP), a protocol for on-demand certificate revocation checking. OCSP is often implemented using large scale distributed systems for scalable.
A blockchain-based certificate revocation checking system could provide advantages over the current OCSP and CRL systems. A lightweight blockchain-based certificate revocation checking protocol could be valuable in a variety of use cases including IoT systems with limited resources.
Certificate Issuance for Blockchain-Based Systems
Distributed PKI solutions may be an ideal choice for providing identities to nodes and users in a blockchain-based system such as a cryptocurrency system. In these cases, there is already a blockchain in place, so using it to store issued certificates and revocation information could be a natural fit.
Such a system may be able to utilize a protocol component for issuing certs, but there will still need to be a centralized registration and signing authority to provide protection of private root keys and validation of certificate signing requests.
Summary
Distributed PKI projects currently suffer from overreaching claims, and implementations lack maturity. More importantly, distributed PKI solutions fail to provide an inherent advantage over traditional solutions. The problems they claim to solve are largely implementation errors, flaws in legacy systems, and lack of automation, all of which have been addressed by existing CA vendors.
Distributed PKI solutions also fail to address the protection of root keys for the PKI hierarchy. Ensuring the security of root keys requires storing them in an HSM, which is the opposite of a distributed solution. Distributed PKI implementations also lack validation, determining if the entity requesting a certificate is truly who it claims to be.
While blockchain-based technologies may play a role in some PKI implementations, it does not seem poised to overturn the industry. While blockchain is a very cool new technology and has a variety of exciting real-world applications, it is not yet ready to replace existing PKI security implementations.
Opinions expressed by DZone contributors are their own.

Comments