Design Patterns for Microservices: Ambassador, Anti-Corruption Layer, and Backends for Frontends
In this article, you will gain a comprehensive understanding of three design patterns and other commonly used patterns for microservices.
Join the DZone community and get the full member experience.
Join For FreeMicroservices architecture has become increasingly popular in recent years due to its ability to enable flexibility, scalability, and rapid deployment of applications. However, designing and implementing microservices can be complex, and it requires careful planning and architecture to ensure the success of the system. This is where design patterns for microservices come in.
Design patterns provide a proven solution to common problems in software architecture. They help to establish best practices and guidelines for designing and implementing microservices, making it easier to create scalable and maintainable systems. In this article, we will focus on three design patterns for microservices: Ambassador, Anti-Corruption Layer, and Backends for Frontends. We will discuss their definitions, implementation, advantages, and disadvantages, as well as their use cases.
By the end of this article, you will have a solid understanding of these three design patterns, as well as other popular patterns for microservices. Additionally, we will provide best practices and guidelines for designing microservices with these patterns, along with common pitfalls to avoid. So, let's dive in and explore the world of design patterns for microservices.
Ambassador Pattern
Definition and Purpose of the Ambassador Pattern
The Ambassador Pattern is a design pattern for microservices that allows communication between microservices while minimizing the complexity of that communication. The pattern involves the use of a separate service, called the "ambassador," that sits between the client and the microservices. The ambassador is responsible for handling the communication between the client and the microservices, which reduces the complexity of the client's requests.
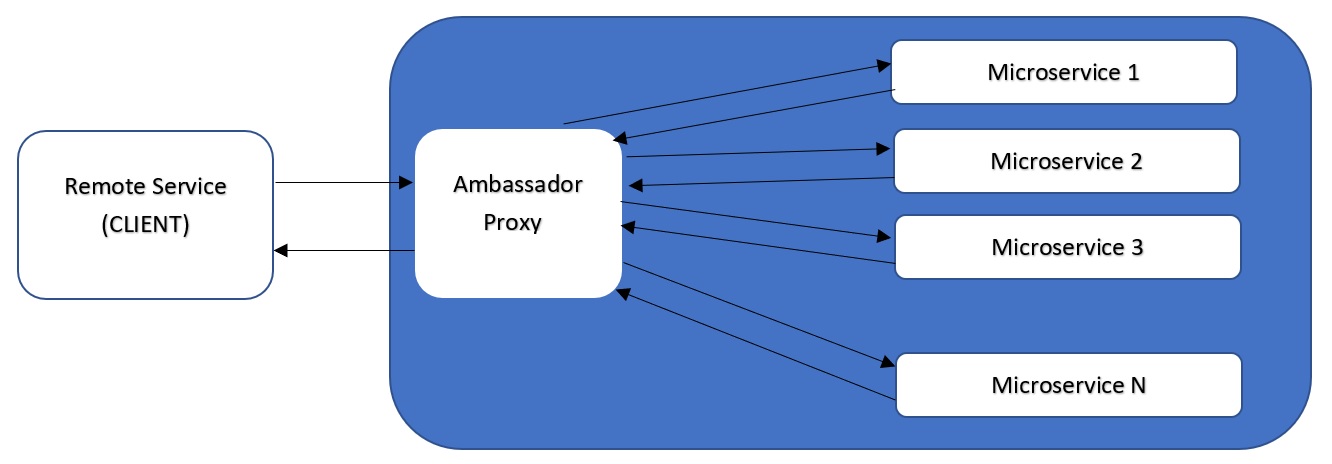
The main purpose of the Ambassador Pattern is to reduce the complexity of communication between microservices. This pattern is particularly useful when microservices use different protocols or when microservices are updated at different times, as it allows for flexibility in communication without requiring changes to the microservices themselves.
Another key benefit of the Ambassador Pattern is that it can help to improve the reliability and scalability of microservices. By separating the communication responsibilities from the microservices, the pattern allows for better fault tolerance and easier scaling of individual services.
In summary, the Ambassador Pattern is a design pattern that uses a separate service to handle communication between microservices and clients. Its main purpose is to reduce the complexity of communication and improve the reliability and scalability of microservices.
Implementation of the Ambassador Pattern
To implement the Ambassador Pattern, you must create an ambassador service between the client and the microservices. The ambassador service will act as a proxy for the microservices, handling communication and translating requests between the client and the microservices.
The following steps can be followed to implement the Ambassador Pattern:
- Define the APIs: First, define the APIs that will be exposed to the client and implemented by the microservices. This will ensure that the client and the microservices agree on the data formats and the communication protocols.
- Create the Ambassador Service: The Ambassador Service should be a separate service that handles communication between the client and the microservices. This service should be responsible for routing requests from the client to the appropriate microservice and translating the data formats, if necessary.
- Deploy the Ambassador Service: Once the Ambassador Service is created, it should be deployed to a separate container or server that is easily accessible to the client and the microservices.
- Route Requests: The Ambassador Service should route requests from the client to the appropriate microservice. This can be done using various techniques, such as routing based on the request URL or using a service registry to locate the microservice.
- Translate Data Formats: If the microservices use different data formats, the Ambassador Service should translate the data formats as necessary. This can be done using a data transformation tool or by writing custom code.
- Implement Fault Tolerance: The Ambassador Service should implement fault tolerance to ensure that it can handle failures in the microservices or the client. This can be done using techniques such as retries, circuit breakers, or fallbacks.
In summary, implementing the Ambassador Pattern involves creating a separate service that acts as a proxy for the microservices and handles communication between the client and the microservices. The Ambassador Service should route requests, translate data formats, and implement fault tolerance to ensure the reliability and scalability of the microservices.
Advantages and Disadvantages of the Ambassador Pattern
Like any design pattern, the Ambassador Pattern has its advantages and disadvantages. Understanding these pros and cons can help you determine whether the pattern is a good fit for your microservices architecture.
Advantages:
- Reduced Complexity: The Ambassador Pattern reduces the complexity of communication between microservices by providing a separate service to handle the communication.
- Protocol Agnostic: The Ambassador Pattern can be used with any protocol, allowing microservices to use different protocols as needed.
- Better Reliability: The Ambassador Pattern can improve the reliability of microservices by providing fault tolerance and better handling of failures.
- Easier Scalability: The Ambassador Pattern makes it easier to scale individual microservices, as the communication between them is handled by a separate service.
Disadvantages:
- Added Complexity: While the Ambassador Pattern reduces the complexity of communication between microservices, it does add an extra layer of complexity to the overall architecture.
- Performance Overhead: The use of an additional service can result in a performance overhead for the microservices architecture.
- Additional Management: The Ambassador Service requires additional management and maintenance, which can increase the overall cost and complexity of the microservices architecture.
- Potential Single Point of Failure: The Ambassador Service can become a single point of failure for the microservices architecture, which can have significant impacts on the system's reliability.
In summary, the Ambassador Pattern offers several advantages, such as reduced complexity, protocol agnosticism, and better reliability and scalability. However, it also has some disadvantages, such as added complexity, potential performance overhead, additional management, and the potential for a single point of failure. Understanding these pros and cons can help you determine whether the pattern is a good fit for your microservices architecture.
Use Cases for the Ambassador Pattern
The Ambassador Pattern can be used in a variety of scenarios within a microservices architecture. Here are some common use cases:
- Service Discovery: The Ambassador Pattern can be used to help microservices discover each other in a decentralized and scalable manner. The Ambassador Service can act as a service registry, allowing microservices to register themselves and discover other services.
- Protocol Translation: The Ambassador Pattern can be used to translate between different protocols used by microservices. The Ambassador Service can act as a protocol translator, allowing microservices to use different protocols as needed.
- Load Balancing: The Ambassador Pattern can be used to balance the load across multiple instances of a microservice. The Ambassador Service can route requests to the least busy instance of a microservice, improving performance and reliability.
- Security: The Ambassador Pattern can be used to implement security measures such as authentication and authorization. The Ambassador Service can act as a security gateway, enforcing security policies and protecting microservices from unauthorized access.
- API Management: The Ambassador Pattern can be used to manage APIs exposed by microservices. The Ambassador Service can act as an API gateway, providing a single entry point for clients to access microservices APIs and enforcing API policies such as rate limiting and request throttling.
In summary, the Ambassador Pattern can be used in a variety of scenarios within a microservices architecture, including service discovery, protocol translation, load balancing, security, and API management. Understanding these use cases can help you determine whether the pattern is a good fit for your microservices architecture.
Anti-Corruption Layer Pattern
Definition and Purpose of the Anti-Corruption Layer Pattern
The Anti-Corruption Layer (ACL) Pattern is a design pattern used to isolate and insulate a microservice from another service with a different domain model or communication protocol. This pattern is used to prevent the spread of "corruption" from one service to another, where corruption refers to the introduction of foreign concepts or terminology into a microservice's domain model.
The purpose of the Anti-Corruption Layer Pattern is to provide a translation layer between microservices that have different domain models or communication protocols. This layer allows microservices to communicate with each other without having to understand each other's domain models, reducing complexity and increasing maintainability.
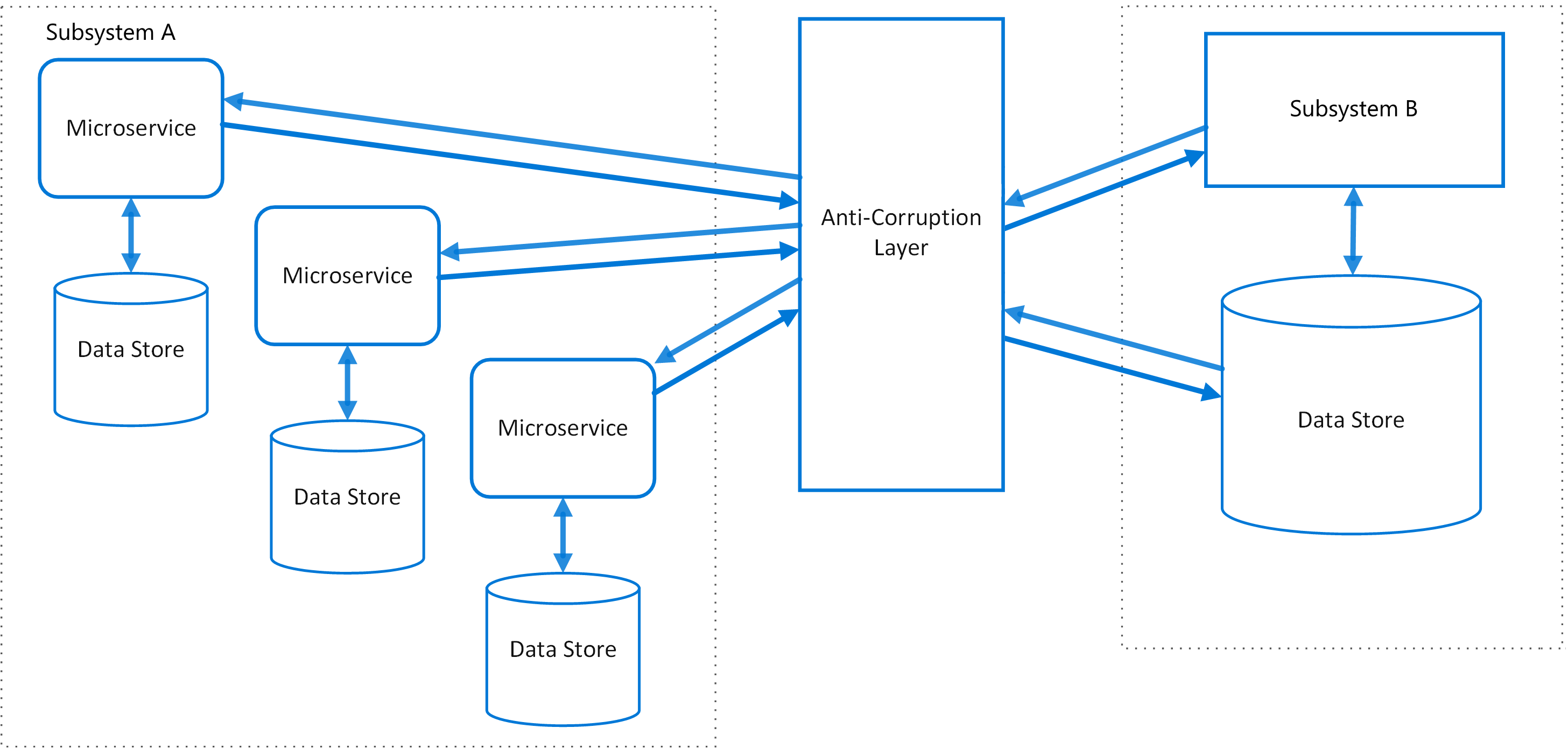
The Anti-Corruption Layer Pattern is especially useful in large-scale microservices architectures where services may be developed by different teams using different technologies and domain models. By providing a translation layer, the ACL pattern allows these services to communicate with each other without having to be modified or refactored to accommodate each other's, domain models.
In summary, the Anti-Corruption Layer Pattern is a design pattern used to isolate and insulate a microservice from another service with a different domain model or communication protocol. The purpose of the ACL pattern is to provide a translation layer between microservices that have different domain models or communication protocols, reducing complexity and increasing maintainability.
Implementation of the Anti-Corruption Layer Pattern
The implementation of the Anti-Corruption Layer Pattern involves creating an intermediary layer between two microservices that have different domain models or communication protocols. This layer acts as a translator, allowing the two microservices to communicate with each other without having to understand each other's, domain models.
To implement the Anti-Corruption Layer Pattern, you can follow these steps:
- Identify the services that need to communicate with each other but have different domain models or communication protocols.
- Create an intermediary layer between the two services. This layer can be implemented as a separate microservice, a library, or a set of classes within a microservice.
- Define a translation layer within the intermediary layer that maps data between the two services. This translation layer should be designed to isolate the microservices from each other, preventing corruption from spreading between them.
- Implement the translation layer using a combination of techniques such as data mapping, data transformation, and data validation.
- Test the intermediary layer to ensure that it is functioning as expected and handling all possible scenarios.
- Deploy the intermediary layer and configure the microservices to use it for communication.
By following these steps, you can successfully implement the Anti-Corruption Layer Pattern in your microservices architecture. The ACL pattern can be implemented in various ways, and the specific implementation details may vary depending on your use case and the technologies you're using.
In summary, implementing the Anti-Corruption Layer Pattern involves creating an intermediary layer that acts as a translator between microservices with different domain models or communication protocols. To implement the ACL pattern, you need to identify the services that need to communicate, create an intermediary layer, define a translation layer, implement the translation layer, test the intermediary layer, and deploy and configure the microservices to use it.
Advantages and Disadvantages of the Anti-Corruption Layer Pattern
Like any design pattern, the Anti-Corruption Layer Pattern has its advantages and disadvantages. Here are some of them:
Advantages:
- Isolation: The ACL pattern provides a way to isolate microservices from each other, preventing the spread of corruption between them. This helps to maintain the integrity of each microservice's domain model.
- Flexibility: The ACL pattern provides a way to integrate microservices with different domain models or communication protocols. This flexibility allows you to develop microservices using different technologies and frameworks.
- Maintainability: By isolating microservices from each other, the ACL pattern makes it easier to maintain each microservice independently. This reduces the risk of unintended changes and makes it easier to update or replace microservices.
- Scalability: The ACL pattern can help to improve the scalability of your microservices architecture by allowing you to add or remove microservices without affecting the rest of the system.
Disadvantages:
- Complexity: The ACL pattern adds an additional layer of complexity to your microservices architecture. This can make it harder to understand and maintain, especially if the translation layer is not well-designed.
- Performance: The ACL pattern can introduce additional latency and overhead to your microservices communication, especially if the translation layer requires significant processing.
- Development Time: Implementing the ACL pattern requires additional development time and effort to design, implement, and test the intermediary layer.
- Additional Infrastructure: The ACL pattern may require additional infrastructure to support the intermediary layer, which can add to the cost and complexity of your microservices architecture.
In summary, the Anti-Corruption Layer Pattern has several advantages, including isolation, flexibility, maintainability, and scalability. However, it also has several disadvantages, including complexity, performance, development time, and additional infrastructure requirements. When deciding whether to use the ACL pattern, you should carefully consider these factors and determine if the benefits outweigh the costs in your specific use case.
Use Cases for the Anti-Corruption Layer Pattern
The Anti-Corruption Layer Pattern can be useful in a variety of scenarios where microservices need to communicate with each other but have different domain models or communication protocols. Here are some examples of use cases for the ACL pattern:
- Legacy Systems Integration: When integrating microservices with legacy systems, it's common to encounter different domain models and communication protocols. The ACL pattern can be used to translate data between the microservices and the legacy systems, allowing them to communicate without having to understand each other's models.
- Multi-Tenant Applications: In multi-tenant applications, different tenants may have different data models or requirements. The ACL pattern can be used to translate data between the microservices and the tenants, allowing them to communicate with each other without affecting each other's data models.
- Service Reusability: In some cases, a microservice may need to be reused in different contexts with different domain models or communication protocols. The ACL pattern can be used to isolate the microservice from the different contexts, allowing it to be reused without modification.
- System Migration: When migrating from one system to another, it's common to encounter different domain models and communication protocols. The ACL pattern can be used to translate data between the old and new systems, allowing them to communicate during the migration process.
- Vendor Integration: When integrating with third-party services or vendors, it's common to encounter different domain models and communication protocols. The ACL pattern can be used to translate data between the microservices and the vendors, allowing them to communicate without having to understand each other's models.
These are just a few examples of use cases for the Anti-Corruption Layer Pattern. In general, the ACL pattern is useful in any scenario where microservices need to communicate with each other but have different domain models or communication protocols. By using the ACL pattern, you can achieve greater flexibility, maintainability, and scalability in your microservices architecture.
Backends for Frontends Pattern
Definition and Purpose of the Backends for Frontends Pattern
The Backends for Frontends (BFF) Pattern is a microservices architecture pattern that involves creating multiple backends to serve different client applications, such as web or mobile applications. Each backend is tailored to a specific client application's needs, providing optimized data and functionality for that application.
The purpose of the BFF pattern is to improve the performance and user experience of client applications by providing them with optimized backends. By tailoring the backends to the needs of each client application, you can ensure that the application has access to the data and functionality it needs without having to make multiple requests or process unnecessary data. This can lead to faster load times, reduced latency, and a more responsive user experience.

Another benefit of the BFF pattern is that it allows you to maintain the separation of concerns between client applications and microservices. Instead of exposing the entire microservices architecture to each client application, you can create tailored backends that provide only the necessary data and functionality. This can help to improve security and reduce the risk of unauthorized access to sensitive data.
Overall, the BFF pattern can be a valuable tool for improving the performance and user experience of client applications while maintaining the separation of concerns and improving security.
Implementation of the Backends for Frontends Pattern
To implement the BFF pattern, you will need to create multiple backends that are tailored to the needs of each client application. Here are the key steps involved in implementing the BFF pattern:
- Identify the client applications: The first step is to identify the client applications that will be using your microservices architecture. For each client application, you will need to create a tailored backend that provides the necessary data and functionality.
- Define the backend APIs: Once you have identified the client applications, you will need to define the APIs for each backend. The APIs should be designed to provide the necessary data and functionality for the specific client application.
- Implement the backend services: Once you have defined the APIs, you will need to implement the backend services that provide the necessary data and functionality. Each backend service should be designed to provide the specific data and functionality required by the client application.
- Implement the BFF layer: The BFF layer is a middleware layer that sits between the client applications and the backend services. Its role is to receive requests from the client application, process them, and forward them to the appropriate backend service. The BFF layer should be designed to provide the necessary data and functionality to the client application without exposing the entire microservices architecture.
- Deploy and test the BFF layer: Once you have implemented the BFF layer, you will need to deploy it and test it to ensure that it is working as expected. You should test each backend service individually, as well as test the entire BFF layer in conjunction with the client application.
By following these steps, you can implement the BFF pattern and create tailored backends that provide the necessary data and functionality for each client application. This can help to improve performance and user experience while maintaining separation of concerns and improving security.
Advantages and Disadvantages of the Backends for Frontends Pattern
Advantages:
- Tailored backends: By creating tailored backends for each client application, you can ensure that the application has access to the data and functionality it needs without having to make multiple requests or process unnecessary data. This can lead to faster load times, reduced latency, and a more responsive user experience.
- Separation of concerns: The BFF pattern allows you to maintain the separation of concerns between client applications and microservices. Instead of exposing the entire microservices architecture to each client application, you can create tailored backends that provide only the necessary data and functionality. This can help to improve security and reduce the risk of unauthorized access to sensitive data.
- Improved performance: By providing optimized backends, you can improve the performance and user experience of client applications. The BFF pattern can help to reduce load times, minimize network traffic, and improve response times.
- Scalability: The BFF pattern can be easily scaled horizontally by adding additional instances of the BFF layer. This can help to ensure that the client applications have access to the necessary resources, even during periods of high traffic.
Disadvantages:
- Increased complexity: The BFF pattern can increase the complexity of the microservices architecture, as it involves creating multiple tailored backends and a middleware layer. This can make the architecture harder to manage and maintain, particularly if there are multiple client applications.
- Increased development time: Creating tailored backends for each client application can be time-consuming and can require additional development resources. This can increase the development time and cost of the microservices architecture.
- Increased testing requirements: With multiple backends and a middleware layer, testing requirements can be more complex and time-consuming. Each backend service and the BFF layer will need to be tested individually and in conjunction with the client applications.
- Increased infrastructure requirements: Creating multiple backends and a middleware layer can require additional infrastructure resources, such as servers and databases. This can increase the infrastructure requirements and cost of the microservices architecture.
Overall, the Backends for Frontends pattern can provide significant benefits for improving the performance and user experience of client applications while maintaining separation of concerns and improving security. However, it can also introduce additional complexity, development time, testing requirements, and infrastructure requirements, which should be carefully considered before implementing the pattern.
Use Cases for the Backends for Frontends Pattern
The Backends for Frontends pattern can be particularly useful in microservices architectures that have multiple client applications with different requirements for data and functionality. Here are some use cases for the BFF pattern:
- Mobile applications: Mobile applications often have specific requirements for data and functionality, such as optimized performance and reduced data usage. By creating tailored backends for each mobile application, you can provide optimized access to the necessary data and functionality while maintaining security and separation of concerns. Additionally, the BFF pattern can help to reduce the load on mobile devices, as the backend can handle processing and optimization tasks.
- Web applications: Web applications can also have specific requirements for data and functionality, such as personalized content and real-time updates. By creating tailored backends for each web application, you can provide access to the necessary data and functionality while maintaining security and separation of concerns. Additionally, the BFF pattern can help to reduce the load on the web browser, as the backend can handle processing and optimization tasks.
- Third-party integrations: Microservices architectures often need to integrate with third-party services, such as payment gateways and social media platforms. By creating tailored backends for each third-party integration, you can provide access to the necessary data and functionality while maintaining security and separation of concerns. Additionally, the BFF pattern can help to reduce the risk of exposing the entire microservices architecture to third-party services.
- IoT applications: IoT applications often have specific requirements for data and functionality, such as real-time data processing and device management. By creating tailored backends for each IoT application, you can provide access to the necessary data and functionality while maintaining security and separation of concerns. Additionally, the BFF pattern can help to reduce the load on IoT devices, as the backend can handle processing and optimization tasks.
Overall, the Backends for Frontends pattern can be a useful approach for creating tailored backends for different client applications and use cases. By maintaining the separation of concerns and providing optimized access to the necessary data and functionality, the BFF pattern can help to improve the performance, scalability, and security of microservices architectures.
Other Design Patterns for Microservices
In addition to the Ambassador, Anti-Corruption Layer, and Backends for Frontends patterns, there are several other design patterns that are commonly used in microservices architectures. Here's a brief overview of some of these patterns:
- Circuit Breaker: The Circuit Breaker pattern is used to prevent cascading failures in distributed systems. It works by monitoring the availability of a service and, if it detects a failure, temporarily halting requests to that service. This allows the system to recover and prevents it from being overwhelmed with failed requests.
- Service Registry: The Service Registry pattern is used to keep track of available services in a microservices architecture. It works by having each service register itself with a central registry, which can then be used to look up and locate services as needed. This allows for more flexible and dynamic communication between services.
- API Gateway: The API Gateway pattern provides a single point of entry for client applications to access a microservices architecture. It works by routing requests from client applications to the appropriate services and can also handle authentication, caching, and other cross-cutting concerns.
- Saga: The Saga pattern manages distributed transactions in microservices architectures. It works by breaking up a transaction into a series of smaller, local transactions that are managed by each individual service. If any part of the transaction fails, the Saga can be used to roll back or compensate for the changes made by the other services.
- Event Sourcing: The Event Sourcing pattern is used to capture and store all changes made to a system as a sequence of events. It works by recording each change as an event, which can then be used to reconstruct the state of the system at any point in time. This can be useful for auditing, debugging, and replaying events.
These are just a few examples of the many design patterns that are used in microservices architectures. Each pattern has its own strengths and weaknesses, and the appropriate pattern(s) to use will depend on the specific requirements and constraints of your system.
Tips and Guidelines for Effectively Designing Microservices Using Design Patterns
Designing a microservices architecture using design patterns can be complex, but there are several tips and guidelines that can help ensure a successful implementation. Here are some best practices to keep in mind:
- Choose the right pattern(s) for your system: Each design pattern has its own strengths and weaknesses, so it's important to choose the pattern(s) that best fit the specific requirements and constraints of your system. Be sure to consider factors such as scalability, maintainability, and performance when selecting patterns.
- Use a consistent set of patterns: Using a consistent set of design patterns throughout your system can help make it easier to understand and maintain. This can also help with testing and debugging, as issues in one part of the system can often be traced to patterns used elsewhere.
- Use automated testing and monitoring: Automated testing and monitoring are crucial for ensuring the reliability and performance of a microservices architecture. Be sure to test each service and the system as a whole, and use monitoring tools to track performance and detect issues in real time.
- Avoid tightly-coupled services: Tightly-coupled services can be difficult to maintain and scale and can lead to cascading failures. Instead, use design patterns such as the Anti-Corruption Layer and Circuit Breaker to help decouple services and prevent failures from spreading.
- Design for resilience: Microservices architectures are inherently distributed and complex, so it's important to design for resilience. Use patterns such as the Circuit Breaker and Saga to help manage failures and design services to be resilient to network latency and other issues.
- Ensure security and privacy: Microservices architectures can create security and privacy challenges, so it's important to ensure that each service is secure and that sensitive data is protected. Use patterns such as the API Gateway and Access Token to help control access to services, and ensure that each service follows secure coding practices.
By following these tips and guidelines, you can help ensure that your microservices architecture is reliable, scalable, and secure.
Common Pitfalls to Avoid
While design patterns can help address many of the challenges of designing microservices architectures, there are also several common pitfalls to be aware of. Here are some pitfalls to avoid:
- Over-engineering: It's easy to fall into the trap of over-engineering a microservices architecture by using too many patterns or building overly complex services. This can lead to reduced performance, increased maintenance costs, and a higher risk of failure.
- Underestimating testing and monitoring: Testing and monitoring are critical for ensuring the reliability and performance of a microservices architecture, but they can be time-consuming and complex. Don't underestimate the effort required for testing and monitoring, and be sure to use automated tools to help manage these tasks.
- Ignoring security and privacy: Security and privacy should be a top priority when designing microservices architectures, but they are often overlooked. Be sure to design services to be secure by default and use patterns such as the API Gateway and Access Token to help manage access to services.
- Failing to consider non-functional requirements: Non-functional requirements, such as scalability, maintainability, and performance, are just as important as functional requirements when designing microservices architectures. Be sure to consider these requirements when choosing design patterns and designing services.
- Choosing patterns based on hype: There are many design patterns available for microservices architectures, and it can be tempting to choose patterns based on hype or popularity. However, it's important to choose patterns based on the specific requirements and constraints of your system rather than blindly following trends.
By being aware of these common pitfalls, you can help ensure that your microservices architecture is well-designed, reliable, and secure.
Summary of Key Takeaways
In this article, we have explored several key design patterns for microservices, including the Ambassador Pattern, Anti-Corruption Layer Pattern, and Backends for Frontends Pattern. Here are some of the key takeaways from our discussion:
- Design patterns can help address common challenges in microservices architectures, such as service discovery, communication, and scalability.
- The Ambassador Pattern can be used to provide a proxy for service discovery and to add additional functionality to services, while the Anti-Corruption Layer Pattern can help isolate services from external dependencies and legacy systems.
- The Backends for Frontends Pattern can be used to provide customized APIs for different types of clients and to simplify communication between services.
- While design patterns can offer many advantages, they also have some disadvantages, such as increased complexity and potential performance issues.
- When designing microservices architectures, it's important to consider non-functional requirements, such as scalability, maintainability, and security, and to avoid common pitfalls such as over-engineering and failing to consider testing and monitoring.
- Choosing the right design patterns depends on the specific requirements and constraints of your system and should not be based solely on hype or popularity.
By keeping these key takeaways in mind, you can effectively design microservices architectures that are scalable, maintainable, and secure.
Final Thoughts on the Importance of Design Patterns for Microservices
In today's fast-paced software development world, microservices have emerged as a popular approach to building scalable, maintainable, and flexible software systems. However, implementing a microservices architecture can be challenging, particularly as the number of services and interdependencies increase.
This is where design patterns can play a crucial role. By applying design patterns, you can address common challenges in microservices architectures and make your system more robust, scalable, and maintainable. Moreover, design patterns can provide a common language for developers to communicate and share best practices.
However, it's important to remember that design patterns are not a silver bullet and should be applied judiciously based on the specific requirements and constraints of your system. In addition, design patterns should be adapted and customized to suit your unique needs rather than blindly applied without consideration of the larger context.
In conclusion, design patterns can be a valuable tool for designing and implementing microservices architectures. Still, they should not be seen as a replacement for sound architectural principles and good engineering practices. By combining design patterns with solid engineering practices, you can build microservices architectures that are robust, scalable, and maintainable and that can evolve over time to meet changing business needs.
Opinions expressed by DZone contributors are their own.

Comments