Database Audit Log Monitoring for Security and Compliance
In this article, we will outline the importance of audit log analysis for database security, using MariaDB and Enterprise MySQL as examples.
Join the DZone community and get the full member experience.
Join For Freewe recently conducted a webinar on audit log analysis for mysql & mariadb databases . this blog will further provide a deep dive into the security and compliance surrounding databases.
database auditing is the tracking of database resources utilization and authority, specifically, the monitoring and recording of user database actions. auditing can be based on a variety of factors, including individual actions, such as the type of sql statement executed, or on a combination of factors such as username, application, time, etc. performing regular database log analysis bolsters your internal security measures by answering questions like who changed your critical data, when it was changed, and more. database auditing also helps you comply with increasingly demanding compliance requirements.
the purpose of this blog is to outline the importance of audit log analysis using mariadb and enterprise mysql as examples.
auditing requirements
the requirement to track access to database servers and the data itself is not that new, but in recent years, there has been a marked need for more sophisticated tools. when auditing is enabled, each database operation on the audited database records a trail of information such as what database objects were impacted, who performed the operation and when . the comprehensive audit trail of executed database actions can be maintained over time to allow dbas, security staff, as well as any authorized personnel, to perform in-depth analysis of access and modification patterns against data in the dbms.
keep in mind that auditing tracks what a particular user has done once access has been allowed. hence, auditing occurs post-activity; it does not do anything to prohibit access. of course, some database auditing solutions have grown to include capabilities that will identify nefarious access and shut it down before destructive actions can occur.
audit trails produced by intrusion detection help promote data integrity by enabling the detection of security breaches. in this capacity, an audited system can serve as a deterrent against users tampering with data because it helps to identify infiltrators. your company’s business practices and security policies may dictate being able to trace every data modification back to the initiating user. moreover, government regulations may require your organization to analyze data access and produce regular reports, either on an ongoing basis or on a case-by-case basis, when there is a need to identify the root cause of data integrity problems. auditing is beneficial for all of these purposes.
moreover, should unauthorized, malicious, or simply ill-advised operations take place, proper auditing will lead to the timely discovery of the root cause and resolution.
the general data protection regulation
on april 27, 2016, the general data protection regulation (gdpr) was adopted by the european parliament and the council of the european union that will be taking effect starting on may 25, 2018. it’s a regulation in eu law governing data protection and privacy for all individuals within the european union. it introduces numerous security and compliance regulations to all organizations worldwide that handle, process, collect, or store the personal information of eu citizens. this means that organizations that work with personal data will have to elevate security measures and auditing mechanisms when handling personal identifiable information (pii) of eu citizens.
furthermore, organizations will have to ensure that only people who should have access to the personal information of eu citizens are granted access, and in case of unauthorized access, organizations must have mechanisms to detect and be alerted on any such incident in order to resolve any possible issues in an expeditious manner. following a data breach, organizations must disclose full information on these events to their local data protection authority (dpa) and all customers concerned with the data breach in no more than 72 hours so they can respond accordingly.
failing to comply with gdpr standards could result in heavy fines of up to 4% of the offending organization’s global revenue, or €20 million (whichever is greater). with this in mind, it is crucial for all affected organizations to make sure that they implement adequate log monitoring on their databases, as defined by the standard.
how databases implement auditing
there is no set standard that defines how a database should implement auditing, so vendors and database administrators (dbas) differ in their approach. some employ special tables while others utilize log files. the two dbmss that we’ll be looking at here today, mariadb and mysql, employ log-based auditing.
the mariadb audit plugin
prior to mariadb 5.5.20, in order to record user access, you would have had to employ third-party database solutions. to help businesses comply with internal auditing regulations and those of various regulatory bodies, mariadb developed the mariadb audit plugin. the mariadb audit plugin can also be used with mysql but includes some unique features that are available only for mariadb.
in mariadb, the audit plugin logs detailed information for any type of access from users to your database server and tables, including:
- timestamp
- server-host
- user
- client-host
- connection-id
- query-id
- operation
- database
- table
- error-code
installation
getting the maria audit plugin installed, configured, and the auditing activated is fairly simple. in fact, you only need a few minutes to enable auditing for your database. a restart of the server is not needed, so you do not need to plan any downtime for the installation of the plugin. the only requirement is that you are running mariadb or mysql server with version 5.5 or newer (mysql 5.5.14, mariadb 5.5.20).
if you installed mariadb from its official packages, you probably already have the plugin on your system, even though it’s neither installed nor enabled by default. look for a file called “server_audit.so” (in linux) or “server_audit.dll” (in windows) inside your plugins directory. the file path of the plugin library is stored in the plugin_dir system variable. to see the value of this variable and determine the file path of the plugin library, execute the following sql statement:
show global variables like 'plugin_dir';
+---------------+--------------------------+
| variable_name | value |
+---------------+--------------------------+
| plugin_dir | /usr/lib64/mysql/plugin/ |
+---------------+--------------------------+if you don’t find the plugin file inside your plugins directory, download it from the mariadb site and place it in the plugins directory manually (in linux, ensure that the mariadb server can read the file by giving it 755 permissions and root user ownership).
next, install the plugin using the command:to confirm the plugin is installed and enabled, run the query show plugins;. you should see it appear in the results list:
install plugin server_audit
soname 'server_audit.so';
to confirm the plugin is installed and enabled, run the query
show plugins;
. you should see it appear in the results list:
+-----------------------------+----------+--------------------+-----------------+---------+
| name | status | type | library | license |
+-----------------------------+----------+--------------------+-----------------+---------+
| server_audit | active | audit | server_audit.so | gpl |
+-----------------------------+----------+--------------------+-----------------+---------+
the mariadb audit plugin comes with many variables to let you fine-tune your auditing to help you better concentrate on just those events and statements that are important to you. you can see the currently set variables with the command show global variables like
"server_audit%";
:
mariadb [(none)]> show global variables like "server_audit%";
+-------------------------------+-----------------------+
| variable_name | value |
+-------------------------------+-----------------------+
| server_audit_events | |
| server_audit_excl_users | |
| server_audit_file_path | server_audit.log |
| server_audit_file_rotate_now | off |
| server_audit_file_rotate_size | 1000000 |
| server_audit_file_rotations | 9 |
| server_audit_incl_users | |
| server_audit_logging | on |
| server_audit_mode | 0 |
| server_audit_output_type | file |
| server_audit_syslog_facility | log_user |
| server_audit_syslog_ident | mysql-server_auditing |
| server_audit_syslog_info | |
| server_audit_syslog_priority | log_info |
+-------------------------------+-----------------------+
these variables should be specified in the mariadb server configuration file (e.g /etc/my.cnf.d/server.cnf) in the [server] section in order to be persistent between server restarts. for example, to have the variable
server_audit_logging
set to
on
, add the line
server_audit_logging=on
to the file:
[server]
…
server_audit_logging=off
…
here is a quick rundown of some of the most important variables:
-
server_audit_logging– enables audit logging; if it’s not set to on, audit events will not be recorded and the audit plugin will not do anything. -
server_audit_events– specifies the events you wish to have in the log. by default, the value is empty, which means that all events are recorded. the options are:- connection (users connecting and disconnecting)
- query (queries and their result)
- table (which tables are affected by the queries)
-
server_audit_excl_users,server_audit_incl_users– these variables specify which users’ activity should be excluded from or included in the audit.server_audit_incl_usershas the higher priority. by default, all users’ activity is recorded. -
server_audit_output_type– by default auditing output is sent to a file. the other option is “syslog”, meaning all entries go to the syslog facility. -
server_audit_syslog_facility,server_audit_syslog_priority– specifies the syslog facility and the priority of the events that should go to syslog.
understanding the log file entries
once you have the audit plugin configured and running, you can examine the log file, (e.g. /var/lib/mysql/server_audit.log). there you will find all the events that have been enabled by the
server_audit_logging
variable. for example, connection entries will show you the user and from where connects and disconnects occur:
20140901 15:33:43,localhost.localdomain,root,localhost,5,0,connect,,,0
20140901 15:45:42,localhost.localdomain,root,localhost,5,0,disconnect,,,0here are some example table and query entries:
20140901 15:19:44,localhost.localdomain,root,localhost,4,133,write,video_king,stores,
20140901 15:19:44,localhost.localdomain,root,localhost,4,133,query, video_king,'delete from stores limit 10',0the first entry shows that there were write operations on the database video_king and the table stores . the query that made the write changes follows: delete from stores limit 10. the order of these statements will be always the same – first the table event and then the query event that caused it.
a read operation looks like this:
20140901 15:20:02,localhost.localdomain,root,localhost,4,134,read,video_king,stores,
20140901 15:20:05,localhost.localdomain,root,localhost,4,134,query,stores,'select * from stores limit 100',0mysql enterprise audit
mysql enterprise edition includes mysql enterprise audit, implemented using a server plugin named audit_log . mysql enterprise audit uses the open mysql audit api to enable standard, policy-based monitoring, logging, and blocking of connection and query activity executed on specific mysql servers. designed to meet the oracle audit specification, mysql enterprise audit provides an out of box auditing and compliance solution for applications that are governed by both internal and external regulatory guidelines.
installation
the plugin is included with mysql enterprise audit, so you simply need to add the following to your my.cnf file to register and enable the audit plugin:
[mysqld]
plugin-load=audit_log.so
(keep in mind the audit_log suffix is platform dependent, so .dll on windows, etc.)
alternatively, you can load the plugin at runtime:
mysql> install plugin audit_log soname 'audit_log.so';
auditing for a specific mysql server can be dynamically enabled and disabled via the
audit_log_policy
global variable. it uses the following named values to enable or disable audit stream logging and to filter the audit events that are logged to the audit stream:
- “all” – enable audit stream and log all events.
- “logins” – enable audit stream and log only login events.
- “queries” – enable audit stream and log only query events.
- “none” – disable audit stream.
another global variable,
audit_log_rotate_on_size
, allows you to automate the rotation and archival of audit stream log files based on size. archived log files are renamed and appended with a datetime stamp when a new file is opened for logging.
the mysql audit stream is written as xml, using uft-8 (without compression or encryption) so that it can be easily formatted for viewing using a standard xml parser. this enables you to leverage third-party tools to view the contents. you may override the default file format by setting the
audit_log_format
system variable at server startup. formats include:
-
old-style xml format (
audit_log_format=old): the original audit logging format used by default in older mysql series. -
new-style xml format (
audit_log_format=new): an xml format that has better compatibility with oracle audit vault than old-style xml format. mysql 5.7 uses new-style xml format by default. -
json format (
audit_log_format=json)
by default, the file is named “audit.log” and resides in the server data directory. to change the name of the file, you can set the
audit_log_file
system variable at server startup.
mysql enterprise audit was designed to be transparent at the application layer by allowing you to control the mix of log output buffering and asynchronous or synchronous disk writes to
minimize the associated overhead that comes when the audit stream is enabled. the net result is that, depending on the chosen audit stream log stream options, most application users will see little to no difference in response times when the audit stream is enabled.
monyog mysql monitor
while reading the audit log file is great for a quick casual look, it’s not the most practical way to monitor database logs. chances are you’ll be better off using the syslog option or, better still, taking advantage of tools that report on the audit log and/or syslogs. there, you can process entries to focus on certain type of events of interest.
one such tool is monyog mysql monitor. version 8.5.0 introduces audit log analysis for mysql enterprise and mariadb. this feature parses the audit log maintained by the server and displays the content in clean tabular format.
monyog accesses the audit log file, the same way it does for other mysql log files, including the slow query, general query, and error log.
figure 1: audit log options
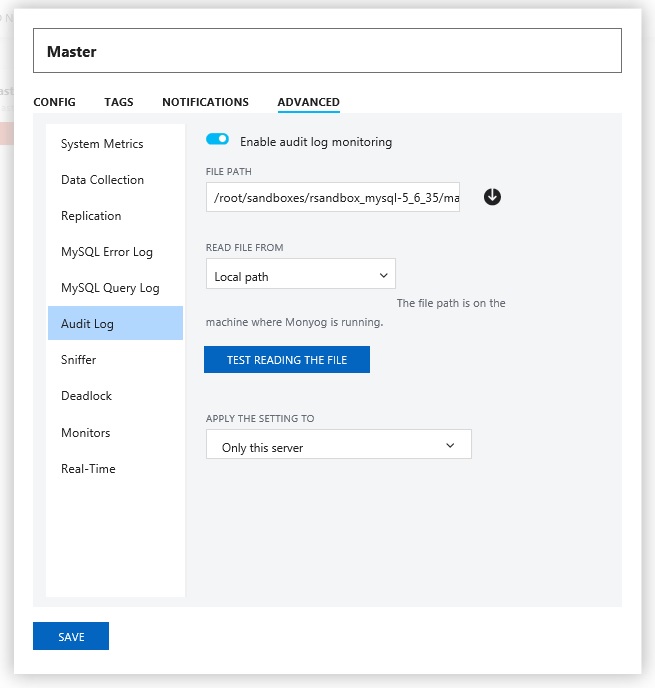
you can select the server and the time-frame for which you want the audit log to be seen from. then, clicking on “show audit log” fetches the contents of the log. the limit on the number of rows which can be fetched in one time-frame is 10000.
figure 2: audit log screen
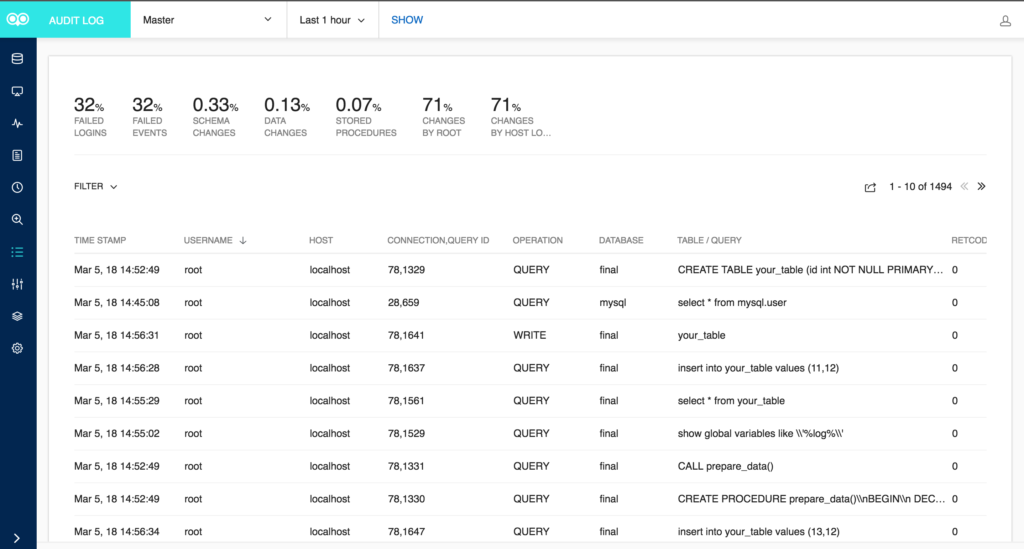
the section on the top gives you a quick summary of the audit log in percentages like failed logins, failed events, schema changes, data changes, and stored procedure. all these legends are clickable and show the corresponding audit log entries on clicking. furthermore, you can use the filter option to fetch audit log based on username, host, operation, database, and table/query. there is also an option to export the fetched audit log content in csv format.
conclusion
in this post, we outlined the importance of audit log analysis using mariadb and enterprise mysql as examples.
in recent years, there has been a marked need for more sophisticated tools due to increased internal and external security and auditing policies.
a properly audited system can serve as a deterrent against users tampering with data because it helps to identify infiltrators. once an unauthorized, malicious, or simply ill-advised operation has taken place, proper auditing will lead to the timely discovery of the root cause and resolution.
both mariadb and mysql implement auditing via native plugins. these are fully configurable and may record database activities in a variety of formats. the resulting log files may be read directly or analyzed by a tool such as the monyog mysql monitor. it provides a summary of failed logins, failed events, schema changes, data changes and stored procedure, as well as fields such as username, host, operation, database and table/query, all within an easy-to-read tabular format.
download a 14-day free trial of monyog mysql monitor .
Published at DZone with permission of Shree Nair. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments