Building Trust Through "Zero Trust:" Transforming Organizational Security Culture
The zero-trust security model empowers developers to build and deploy applications with security as a core component.
Join the DZone community and get the full member experience.
Join For FreeEditor's Note: The following is an article written for and published in DZone's 2024 Trend Report, Enterprise Security: Reinforcing Enterprise Application Defense.
With organizations increasingly relying on cloud-based services and remote work, the security landscape is becoming more dynamic and challenging than ever before. Cyberattacks and data breaches are on the rise, with high-profile organizations making headlines regularly. These incidents not only cause significant financial loss but also result in irreparable reputational damage and loss of customer trust.
Organizations need a more robust security framework that can adapt to the ever-evolving security landscape to combat these threats. Traditional perimeter-based security models, which assume that everything inside the network is trustworthy, are proving to be insufficient in handling sophisticated cyber threats. Enter zero trust, a security framework built on the principle of "never trust, always verify."
Instead of assuming trust within the network perimeter, zero trust mandates verification at every access attempt, using stringent authentication measures and continuous monitoring. Unlike traditional security models that often hinder agility and innovation, this framework empowers developers to build and deploy applications with security as a core component. By understanding the core principles of zero trust, developers can play a crucial role in fortifying an organization's overall security posture, while maintaining development velocity.
Core Principles of Zero Trust
Understanding the core principles of zero trust is crucial to successfully implementing this security framework. These principles serve as a foundation for building a secure environment where every access is continuously verified. Let's dive into the key concepts that drive zero trust.
Identity Verification
The core principle of zero trust is identity verification. This means that every user, device, and application accessing organizational resources is authenticated using multiple factors before granting access. This often includes multi-factor authentication (MFA) and strong password policies. Treating every access attempt as a potential threat can significantly reduce an organization's attack surface.
Least-Privilege Access
The principle of least privilege revolves around limiting user access to only the minimum necessary resources to perform their specific tasks. By limiting permissions, organizations can mitigate the potential damage caused by a security breach. This can be done by designing and implementing applications with role-based access controls (RBAC) to reduce the risk of insider threats and lateral movement within the network.
Micro-Segmentation
Zero trust advocates for micro-segmentation to further isolate and protect critical assets. This involves dividing the network into smaller, manageable segments to prevent lateral movement of threats. With this, organizations isolate potential breaches and minimize the impact of a successful attack. Developers can support this strategy by designing and implementing systems with modular architectures that can be easily segmented.
Continuous Monitoring
The zero-trust model is not static. Organizations should have robust monitoring and threat detection systems to identify and respond to suspicious activities. A proactive monitoring approach helps identify anomalies and threats before they can cause any harm. This involves collecting and analyzing data from multiple sources like network traffic, user behavior, and application logs. Having all this in place is crucial for the agility of the zero-trust framework.
Assume Breach
Always operate under the assumption that a breach will occur. Rather than hoping to prevent all attacks, organizations should focus on quick detection and response to minimize the impact and recovery time when the breach occurs. This can be done by implementing well-defined incident response procedures, regular penetration tests and vulnerability assessments, regular data backups, and spreading awareness in the organization.
The Cultural Shift: Moving Toward a Zero-Trust Mindset
Adopting a zero-trust model requires a cultural shift within the organization rather than only a technological implementation. It demands collaboration across teams, a commitment to security best practices, and a willingness to change deeply integrated traditional mindsets and practices that have governed IT security for some time. To understand the magnitude of this transformation, let's compare the traditional security model with the zero-trust approach.
Traditional Security Models vs. Zero Trust
With traditional security models, organizations rely on a strong perimeter and focus on protecting it with firewalls and intrusion detection systems. The assumption is that if you could secure the perimeter, everything inside it is trustworthy. This worked well in environments where data and applications were bounded within corporate networks. However with the rise of cloud-based systems, remote work, and BYOD (bring your own device) policies, the boundaries of these networks have become blurred, thus making traditional security models no longer effective.
Figure 1. Traditional security vs. zero trust
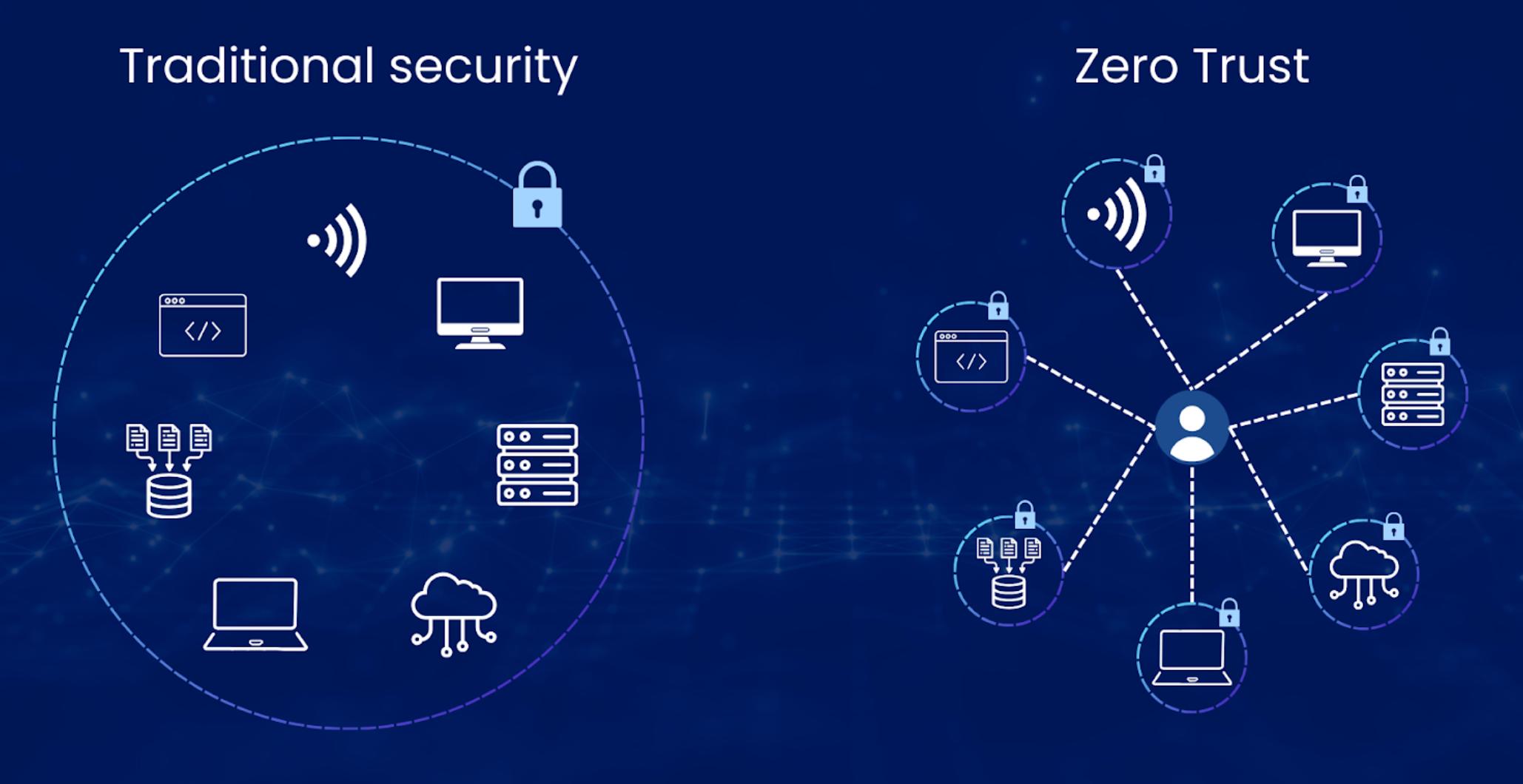
The zero-trust model, on the other hand, assumes that threats can come from anywhere, even from within the organization. It treats each access attempt as potentially malicious until proven otherwise. This is why the model requires ongoing authentication and authorization and is able to anticipate threats and take preventive actions. This paradigm shift requires a move away from implicit trust to a model where continuous verification is the norm.
Changing Mindsets: From Implicit Trust to Continuous Verification
Making this shift isn't just about implementing new technologies but also about shifting the entire organizational mindset around security. Zero trust fosters a culture of vigilance, where every access attempt is scrutinized, and trust must be earned every time. That's why it requires buy-in from all levels of the organization, from top management to frontline employees. It requires strong leadership support, employee education and training, and a transformation with a security-first mindset throughout the organization.
Benefits and Challenges of Zero Trust Adoption
Although the zero-trust model provides a resilient and adaptable framework for modern threats, the journey to implementation is not without its challenges. Understanding these obstacles, as well as the advantages, is crucial to be able to navigate the transition to this new paradigm and successfully adopt the model to leverage its full potential.
Some of the most substantial benefits of zero trust are:
- Enhanced security posture. By eliminating implicit trust and continuously verifying user identities and device compliance, organizations can significantly reduce their attack surface against sophisticated threats.
- Improved visibility and control over network activities. By having real-time monitoring and detailed analytics, organizations gain a comprehensive view of network traffic and user behavior.
- Improved incident response. Having visibility also helps for quick anomaly and potential threat detection, which enables fast and effective incident response.
- Adaptability to modern work environments. Zero trust is designed for today's dynamic workspaces that include cloud-based applications and remote work environments. It enables seamless collaboration and secure access regardless of location.
While the benefits of zero trust are significant, the implementation journey is also covered in challenges, the most common being:
- Resistance to change. To shift to a zero-trust mindset, it is necessary to overcome entrenched beliefs and behaviors in the organization that everything inside the network can be trusted and gain buy-in from all levels of the organization. Additionally, employees need to be educated and made aware of this mindset.
- Balancing security with usability and user experience. Implementing strict access control policies can impact user productivity and satisfaction.
- Potential costs and complexities. The continuous verification process can increase administrative overload as well as require a significant investment in resources and technology.
- Overcoming technical challenges. The zero-trust model involves changes to existing infrastructure, processes, and workflows. The architecture can be complex and requires the right technology and expertise to effectively navigate the complexity. Also, many organizations still rely on legacy systems and infrastructure that may not be compatible with zero-trust principles.
By carefully considering the benefits and challenges of an investment in zero-trust security, organizations can develop a strategic roadmap for implementation.
Implementing Zero Trust: Best Practices
Adopting the zero-trust approach can be a complex task, but with the right strategies and best practices, organizations can overcome common challenges and build a robust security posture.
Table 1. Zero trust best practices
|
Practice
|
Description
|
|---|---|
|
Define a clear zero-trust strategy |
Establish a comprehensive roadmap outlining your organization's goals, objectives, and implementation timeline. |
|
Conduct a thorough risk assessment |
Identify existing vulnerabilities, critical assets, and potential threats to inform your zero-trust strategy and allocate resources. |
|
Implement identity and access control |
Adopt MFA and single sign-on to enhance security. Implement IAM to enforce authentication and authorization policies. |
|
Create micro-segmentation of networks |
Divide your network into smaller segments to isolate sensitive systems and data and reduce the impact of potential breaches. |
|
Leverage advanced threat protection |
Employ artificial intelligence and machine learning tools to detect anomalies and predict potential threats. |
|
Continuously monitor |
Maintain constant vigilance over your system with continuous real-time monitoring and analysis of security data. |
Conclusion
The zero-trust security model is an essential component of today's cybersecurity landscape due to threats growing rapidly and becoming more sophisticated. Traditional security measures are not sufficient anymore, so transitioning from implicit trust to a state where trust is constantly checked adds a layer of strength to an organization's security framework.
However, implementing this model will require a change in organizational culture. Leadership must adopt a security-first mindset that involves every department and employee contributing to safety and security. Cultural transformation is crucial for a new environment where security is a natural component of everyone's activities.
Implementing zero trust is not a one-time effort but requires ongoing commitment and adaptation to new technologies and processes. Due to the changing nature of threats and cyber attacks, organizations need to keep assessing and adjusting their security measures to stay ahead of potential risks.
For all organizations looking to enhance their security, now is the best time to begin the zero-trust journey. Despite appearing as a complex change, it has long-term benefits that outweigh the challenges. Although zero trust can be explained as a security model that helps prevent exposure to today's threats, it also represents a general strategy to help withstand threats in the future.
Here are some additional resources to get you started:
- Getting Started With DevSecOps by Caroline Wong, DZone Refcard
- Cloud-Native Application Security by Samir Behara, DZone Refcard
- Advanced Cloud Security by Samir Behara, DZone Refcard
- "Building an Effective Zero Trust Security Strategy for End-To-End Cyber Risk Management" by Susmitha Tammineedi
This is an excerpt from DZone's 2024 Trend Report, Enterprise Security: Reinforcing Enterprise Application Defense.
Read the Free Report
Opinions expressed by DZone contributors are their own.

Comments