Building a Semantic Web Search App Using Resource Description Framework and Flask for Cyber Resilience
Learn how to integrate Resource Description Framework (RDF) with a Flask-based application to perform the semantic web search for a cyber resilience use case.
Join the DZone community and get the full member experience.
Join For FreeIn cyber resilience, handling and querying data effectively is crucial for detecting threats, responding to incidents, and maintaining strong security. Traditional data management methods often fall short in providing deep insights or handling complex data relationships. By integrating semantic web technologies and RDF (Resource Description Framework), we can significantly enhance our data management capabilities.
This tutorial demonstrates how to build a web application using Flask, a popular Python framework, that leverages these technologies for advanced semantic search and RDF data management.
Understanding the Semantic Web
The Semantic Web
Imagine the web as a huge library where every piece of data is like a book. On the traditional web, we can look at these books, but computers don't understand their content or how they relate to one another. The semantic web changes this by adding extra layers of meaning to the data. It helps computers understand not just what the data is but also what it means and how it connects with other data. This makes data more meaningful and enables smarter queries and analysis.
For example, if we have data about various cybersecurity threats, the semantic web lets a computer understand not just the details of each threat but also how they relate to attack methods, vulnerabilities, and threat actors. This deeper understanding leads to more accurate and insightful analyses.
Ontologies
Think of ontologies as a system for organizing data, similar to the Dewey Decimal System in a library. They define a set of concepts and the relationships between them. In cybersecurity, an ontology might define concepts like "attack vectors," "vulnerabilities," and "threat actors," and explain how these concepts are interconnected. This structured approach helps in organizing data so that it’s easier to search and understand in context.
For instance, an ontology could show that a "vulnerability" can be exploited by an "attack vector," and a "threat actor" might use multiple "attack vectors." This setup helps in understanding the intricate relationships within the data.
Linked Data
Linked data involves connecting pieces of information together. Imagine adding hyperlinks to books in a library, not just pointing to other books but to specific chapters or sections within them. Linked data uses standard web protocols and formats to link different pieces of information, creating a richer and more integrated view of the data. This approach allows data from various sources to be combined and queried seamlessly.
For example, linked data might connect information about a specific cybersecurity vulnerability with related data on similar vulnerabilities, attack vectors that exploit them, and threat actors involved.
RDF Basics
RDF (Resource Description Framework) is a standard way to describe relationships between resources. It uses a simple structure called triples to represent data: (subject, predicate, object). For example, in the statement “John knows Mary,” RDF breaks it down into a triple where "John" is the subject, "knows" is the predicate, and "Mary" is the object. This model is powerful because it simplifies representing complex relationships between pieces of data.
Graph-Based Representation
RDF organizes data in a graph format, where each node represents a resource or piece of data, and each edge represents a relationship between these nodes. This visual format helps in understanding how different pieces of information are connected. For example, RDF can show how various vulnerabilities are linked to specific attack vectors and how these connections can help in identifying potential threats.
SPARQL
SPARQL is the language used to query RDF data. If RDF is the data model, SPARQL is the tool for querying and managing that data. It allows us to write queries to find specific information, filter results, and combine data from different sources. For example, we can use SPARQL to find all vulnerabilities linked to a particular type of attack or identify which threat actors are associated with specific attack methods.
Why Use Flask?
Flask Overview
Flask is a lightweight Python web framework that's great for building web applications. Its simplicity and flexibility make it easy to create applications quickly with minimal code. Flask lets us define routes (URLs), handle user requests, and render web pages, making it ideal for developing a web application that works with semantic web technologies and RDF data.
Advantages of Flask
- Simplicity: Flask’s minimalistic design helps us focus on building our application without dealing with complex configurations.
- Flexibility: It offers the flexibility to use various components and libraries based on our needs.
- Extensibility: We can easily add additional libraries or services to extend your application’s functionality.
Application Architecture
Our Flask-based application has several key components:
1. Flask Web Framework
This is the heart of the application, managing how users interact with the server. Flask handles HTTP requests, routes them to the right functions, and generates responses. It provides the foundation for integrating semantic web technologies and RDF data.
2. RDF Data Store
This is where the RDF data is stored. It's similar to a traditional database but designed specifically for RDF triples. It supports efficient querying and management of data, integrating seamlessly with the rest of the application.
3. Semantic Search Engine
This component allows users to search the RDF data using SPARQL. It takes user queries, executes SPARQL commands against the RDF data store, and retrieves relevant results. This is crucial for providing meaningful search capabilities.
4. User Interface (UI)
The UI is the part of the application where users interact with the system. It includes search forms and result displays, letting users input queries, view results, and navigate through the application.
5. API Integration
This optional component connects to external data sources or services. For example, it might integrate threat intelligence feeds or additional security data, enhancing the application’s capabilities.
Understanding these components and how they work together will help us build a Flask-based web application that effectively uses semantic web technologies and RDF data management to enhance cybersecurity.
Building the Flask Application
1. Installing Required Libraries
To get started, we need to install the necessary Python libraries. We can do this using pip:
pip install Flask RDFLib requests
2. Flask Application Setup
Create a file named app.py in the project directory. This file will contain the core logic for our Flask application.
app.py:
from flask import Flask, request, render_template
from rdflib import Graph, Namespace
from rdflib.plugins.sparql import prepareQuery
app = Flask(__name__)
# Initialize RDFLib graph and namespaces
g = Graph()
STIX = Namespace("http://stix.mitre.org/")
EX = Namespace("http://example.org/")
# Load RDF data
g.parse("data.rdf", format="xml")
@app.route('/')
def index():
return render_template('index.html')
@app.route('/search', methods=['POST'])
def search():
query = request.form['query']
results = perform_search(query)
return render_template('search_results.html', results=results)
@app.route('/rdf', methods=['POST'])
def rdf_query():
query = request.form['rdf_query']
results = perform_sparql_query(query)
return render_template('rdf_results.html', results=results)
def perform_search(query):
# Mock function to simulate search results
return [
{"title": "APT28 Threat Actor", "url": "http://example.org/threat_actor/apt28"},
{"title": "Malware Indicator", "url": "http://example.org/indicator/malware"},
{"title": "Phishing Attack Pattern", "url": "http://example.org/attack_pattern/phishing"}
]
def perform_sparql_query(query):
q = prepareQuery(query)
formatted_results = []
# Parse the SPARQL query
qres = g.query(q)
# # Iterate over the results
# for row in qres:
# # Convert each item in the row to a string
# #formatted_row = tuple(str(item) for item in row)
# formatted_results.append(row)
return qres
if __name__ == '__main__':
app.run(debug=True)
3. Creating RDF Data
RDF Data File
To demonstrate the use of RDFLib in managing cybersecurity data, create an RDF file named data.rdf. This file will contain sample data relevant to cybersecurity.
data.rdf:
<rdf:RDF xmlns:rdf="http://www.w3.org/1999/02/22-rdf-syntax-ns#"
xmlns:rdfs="http://www.w3.org/2000/01/rdf-schema#"
xmlns:stix="http://stix.mitre.org/">
<!-- Threat Actor -->
<rdf:Description rdf:about="http://example.org/threat_actor/apt28">
<rdf:type rdf:resource="http://stix.mitre.org/ThreatActor"/>
<rdfs:label>APT28</rdfs:label>
<stix:description>APT28, also known as Fancy Bear, is a threat actor group associated with Russian intelligence.</stix:description>
</rdf:Description>
<!-- Indicator -->
<rdf:Description rdf:about="http://example.org/indicator/malware">
<rdf:type rdf:resource="http://stix.mitre.org/Indicator"/>
<rdfs:label>Malware Indicator</rdfs:label>
<stix:description>Indicates the presence of malware identified through signature analysis.</stix:description>
<stix:pattern>filemd5: 'e99a18c428cb38d5f260853678922e03'</stix:pattern>
</rdf:Description>
<!-- Attack Pattern -->
<rdf:Description rdf:about="http://example.org/attack_pattern/phishing">
<rdf:type rdf:resource="http://stix.mitre.org/AttackPattern"/>
<rdfs:label>Phishing</rdfs:label>
<stix:description>Phishing is a social engineering attack used to trick individuals into divulging sensitive information.</stix:description>
</rdf:Description>
</rdf:RDF>
Understanding RDF Data
RDF (Resource Description Framework) is a standard model for data interchange on the web. It uses triples (subject-predicate-object) to represent data. In our RDF file:
- Threat actor: Represents a known threat actor; e.g.,
APT28 - Indicator: Represents an indicator of compromise, such as a malware signature
- Attack pattern: Describes an attack pattern, such as phishing
The namespaces stix and taxii are used to denote specific cybersecurity-related terms.
4. Flask Routes and Functions
Home Route
The home route (/) renders the main page where users can input their search and SPARQL queries.
Search Route
The search route (/search) processes user search queries. For this demonstration, it returns mock search results.
Mock Search Function
The perform_search function simulates search results. Replace this function with actual search logic when integrating with real threat intelligence sources.
RDF Query Route
The RDF query route (/rdf) handles SPARQL queries submitted by users. It uses RDFLib to execute the queries and returns the results.
SPARQL Query Function
The perform_sparql_query function executes SPARQL queries against the RDFLib graph and returns the results.
5. Creating HTML Templates
Index Page
The index.html file provides a form for users to input search queries and SPARQL queries.
index.html:
<!DOCTYPE html>
<html>
<head>
<title>Cybersecurity Search and RDF Query</title>
<link rel="stylesheet" type="text/css" href="{{ url_for('static', filename='style.css') }}">
</head>
<body>
<h1>Cybersecurity Search and RDF Query</h1>
<form action="/search" method="post">
<label for="query">Search Threat Intelligence:</label>
<input type="text" id="query" name="query" placeholder="Search for threat actors, indicators, etc.">
<button type="submit">Search</button>
</form>
<form action="/rdf" method="post">
<label for="rdf_query">SPARQL Query:</label>
<textarea id="rdf_query" name="rdf_query" placeholder="Enter your SPARQL query here"></textarea>
<button type="submit">Run Query</button>
</form>
</body>
</html>
Search Results Page
The search_results.html file displays the results of the search query.
search_results.html:
<!DOCTYPE html>
<html>
<head>
<title>Search Results</title>
<link rel="stylesheet" type="text/css" href="{{ url_for('static', filename='style.css') }}">
</head>
<body>
<h1>Search Results</h1>
<ul>
{% for result in results %}
<li><a href="{{ result.url }}">{{ result.title }}</a></li>
{% endfor %}
</ul>
<a href="/">Back to Home</a>
</body>
</html>
SPARQL Query Results Page
The rdf_results.html file shows the results of SPARQL queries.
rdf_results.html:
<!DOCTYPE html>
<html>
<head>
<title>SPARQL Query Results</title>
<link rel="stylesheet" type="text/css" href="{{ url_for('static', filename='style.css') }}">
</head>
<body>
<h1>SPARQL Query Results</h1>
{% if results %}
<table border="1" cellpadding="5" cellspacing="0">
<thead>
<tr>
<th>Subject</th>
<th>Label</th>
<th>Description</th>
</tr>
</thead>
<tbody>
{% for row in results %}
<tr>
<td>{{ row[0] }}</td>
<td>{{ row[1] }}</td>
<td>{{ row[2] }}</td>
</tr>
{% endfor %}
</tbody>
</table>
{% else %}
<p>No results found for your query.</p>
{% endif %}
</body>
</html>
6. Application Home Page
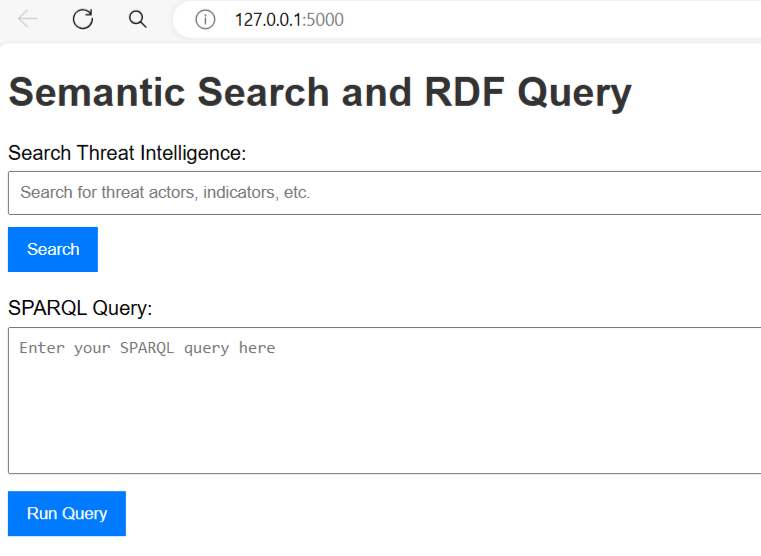
7. SPARQL Query Example
Query Attack Pattern
To list all attack patterns described in the RDF data, the user can input:
SELECT ?subject ?label ?description WHERE {
?subject rdf:type <http://stix.mitre.org/AttackPattern> .
?subject rdfs:label ?label .
?subject <http://stix.mitre.org/description> ?description .
}

Result

Practical Applications
1. Threat Intelligence
The web application’s search functionality can be used to monitor and analyze emerging threats. By integrating real threat intelligence data, security professionals can use the application to track malware, detect phishing attempts, and stay updated on threat actor activities.
2. Data Analysis
RDFLib’s SPARQL querying capabilities allow for sophisticated data analysis. Security researchers can use SPARQL queries to identify patterns, relationships, and trends within the RDF data, providing valuable insights for threat analysis and incident response.
3. Integration With Security Systems
The Flask application can be integrated with existing security systems to enhance its functionality:
- SIEM systems: Feed search results and RDF data into Security Information and Event Management (SIEM) systems for real-time threat detection and analysis.
- Automated decision-making: Use RDF data to support automated decision-making processes, such as alerting on suspicious activities based on predefined patterns.
Conclusion
This tutorial has demonstrated how to build a Flask-based web application that integrates semantic web search and RDF data management for a cybersecurity user case. By utilizing Flask, RDFLib, and SPARQL, the application provides a practical tool for managing and analyzing cyber safety data.
The provided code examples and explanations offer a foundation for developing more advanced features and integrating them with real-world threat intelligence sources. As cyber threats continue to evolve, using semantic web technologies and RDF data will become increasingly important for effective threat detection and response.
Opinions expressed by DZone contributors are their own.

Comments