Blockchain Reference Architecture
In this article, explore the layers of blockchain reference architecture, such as application, Smart Contract, integration, distributed ledger, and security.
Join the DZone community and get the full member experience.
Join For Free
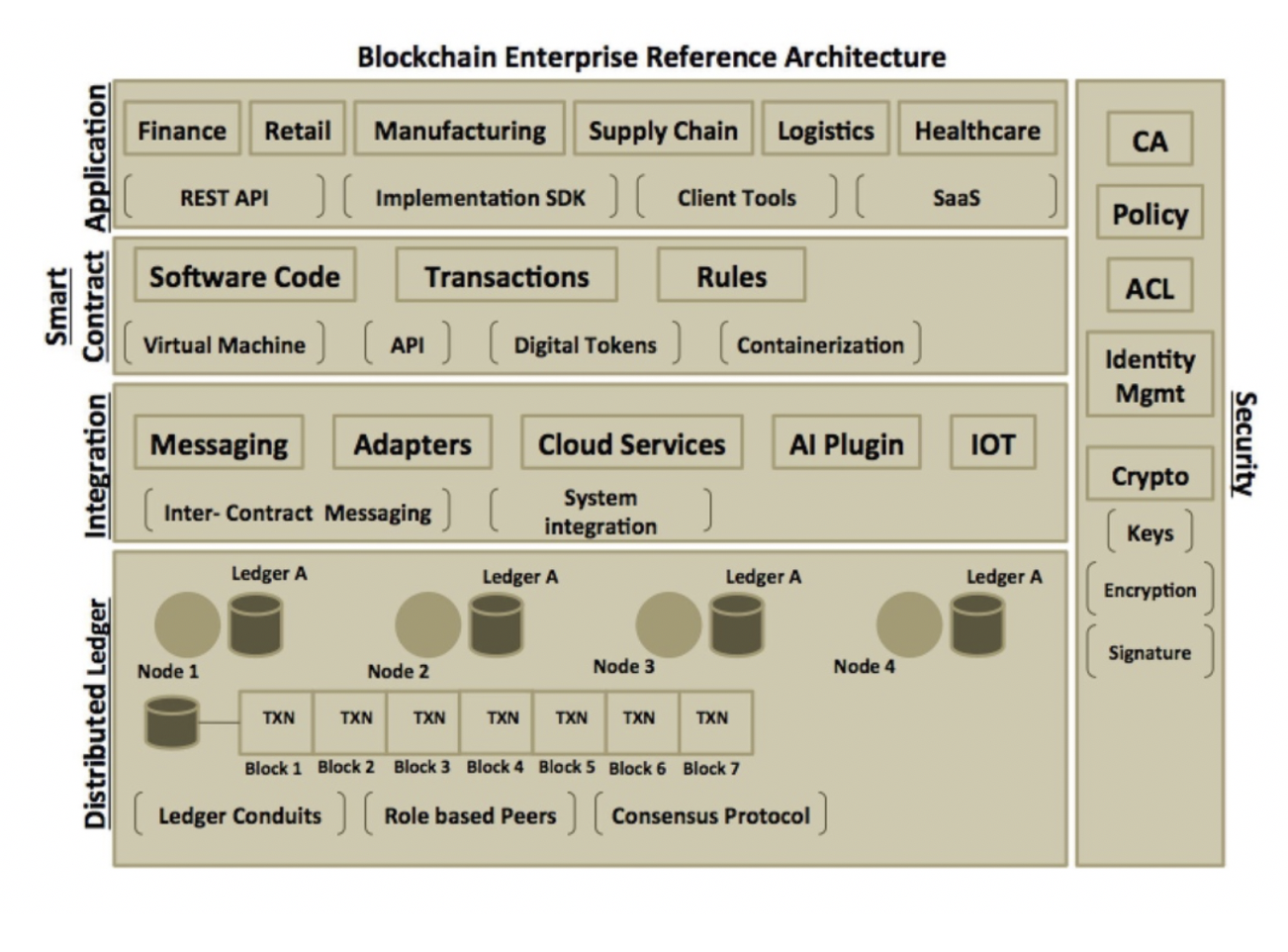
The blockchain design of today has moved beyond cryptocurrency. It has evolved into a platform that supports industry-wide use cases suitable for public and enterprise needs. The reference architecture shown below will serve as a foundation for building or implementing blockchain applications for industry-wide use cases.
It depicts a layered architecture that provides components and services necessary to implement blockchain applications for enterprise needs. It can be used to develop a blockchain of single or multiple networks (involving multiple business units or organizations) based on the business goals and objectives. One can follow the reference architecture to design both permissioned (private) as well as permissionless (public) blockchain applications.
You may also be interested in: Reference Architecture for an Effective Ground Transportation System
The above reference architecture can be used to build any blockchain applications. The architecture is divided into logical layers of importance. These layers are Application, Smart Contract, Integration, Distributed Ledger, and Security. Let’s look at each of these layers and its components:
Application
The application layer is where your end user or client application sits. The client application typically kick starts your business workflow by initiating a transaction. The transactions are executed by the nodes using a smart contract. The client application could be implemented in any software language and can run on a wide variety of operating systems. The application could use a command line interface (CLI) tool as provided by any blockchain framework implementation or it could use language specific SDK (Software Development Kit) to communicate with nodes on the network.
As the blockchain evolves beyond its traditional image of digital cryptocurrency-based network, we are seeing different types of clients and tools supporting the blockchain framework. The client application can also listen to various types of events occurring on the blockchain network and perform the necessary actions on those events. The event may be as simple as providing a status update to the application from the network. One can also have a separate dedicated application to monitor the blockchain network.
Smart Contract
Smart contract is a software code that represents transactions in the blockchain network. It is a collection of business rules or conditions that are invoked by the nodes in the blockchain network. Smart contract can have its own execution runtime or a virtual machine environment. It can be made to run in a secured context, like a virtualized container. Smart contract can be implemented in any software languages, the popular being, but not limited to, Java, Python, Go, JavaScript and Scala. Smart contract can be also written as services and placed in registries so that client can look up for the same in a location independent way.
The registries can be secured, and access can be controlled so that only authorized clients can act upon that contract. Smart contract itself can be made secured using cryptographic hash algorithms so that it’s content (software code and related metadata) is made confidential. Smart contract can also be programmed to communicate or broadcast transaction state transitions in the form of events. It could be lifecycle events of the contract itself. The application client can listen to these events and handle them accordingly.
Integration
In today’s world of disruptive technologies where application integration and communication has become so imperative, no one platform can stand in isolation. Blockchain is no different. Blockchain network should be able to access any data outside of the network. The data could be part of any external application or system that can provide significant value to the blockchain workflow. Similarly, external systems must also be able to communicate with the blockchain network.
One approach could be to set up an external event hub as a medium to exchange data with external systems through event processing. An external application can listen on to a specific event on the hub and accordingly perform some task. On the other hand, a smart contract can listen to events coming from external systems and accordingly execute the business function. The following section explains some other interesting use cases in the integration scenario:
Artificial Intelligence (AI) Integration
Blockchain, as we know, is essentially a distributed ledger with a decentralized and automated approach towards a transaction settlement process based on consensus. So, where does AI fit into blockchain? AI can be influenced by data. Blockchain is a database with loads of transactions that can be made available to branches of AI, like machine learning, that can apply complex algorithms on data to optimize a particular business function.
The branch of AI can also be used to improve the overall business process or workflow. AI algorithms can detect significant anomalies and perform predictive modeling or analysis to find indicators that can reduce the transaction cost and increase the revenue of business for all parties across the blockchain network. AI solutions can also be employed for consensus between systems that need to work autonomously. The combinatorial power of AI and blockchain could be a real game-changer in the future.
Cloud Integration
Blockchain architecture can be extended to implement a component hosted on the cloud that can provide application integration services like routing, data transformation, protocol translation, extended certificate authority, etc. This component can act as a middleware, offering its capabilities as a ‘blockchain as a service’ function in the cloud. The blockchain implementation can provide adapters to connect to the middleware component from within the blockchain network and outside of the network.
The blockchain middleware component can be hosted in a secured ‘sandboxed’ environment or inside a secured virtualized container. An external application can interact with the blockchain middleware using adapters and upon obtaining valid certificates to access the blockchain network.
IoT Integration
A new wave of integration will involve arbitrary devices to communicate with the blockchain network. Different types of IoT devices or sensors can inject data into the blockchain network that can then be validated by the blockchain nodes. A standardized middleware can be implemented that can take the data from the device and perform the necessary conversion and transformation of data as required by the blockchain network. The peers or the nodes in the blockchain network can then go about validating this data using a specific consensus algorithm using smart contracts.
Distributed Ledger
This distributed ledger is the core persistent layer in the blockchain architecture. It provides a decentralized and distributed database containing the transaction entries. These entries are recorded in the order of its occurrence and composed into hashed blocks. The database or the ledger, therefore, represents a chain of hashed blocks of transactions with each block referring to the previous block in the chain. The ledger is shared across the blockchain network, which means every node has a copy of the ledger, and each node verifies the transactions independently.
When every node agrees and confirms the authenticity of the transaction, the ledger is said to be in consensus. The blockchain network uses different consensus algorithms to arrive at the consensus. The consensus algorithm is a set of rules and conditions that governs the transaction. The blockchain network implemented for the public has a permissionless ledger, while in a private network or a consortium, a ledger can be made permissioned. A permissioned ledger introduces some form of access control in the way transactions are accessed and managed.
Ledger Conduits
For a permissioned-based blockchain network, one can implement a pattern called ledger conduits. Conduits can be thought of as private channels in the blockchain network where two or more nodes perform transactions even more privately. The nodes must be members and authorized to use these conduits. Conduits are small networks inside a large network. Such a pattern further enforces security when implementing blockchain in an enterprise.
Consensus Algorithms
The blockchain network typically is governed by anonymous entities or nodes that are not trusted. The consensus is all about providing the trust factor in the network. Each node can update the blockchain network with data in the form of a transaction that eventually needs to be verified before it can be officially recorded as part of a block in the ledger. There are different consensus algorithms that convey how the block (of transactions) is created and validated, thereby enforcing trust in the network.
Practical Byzantine Fault Tolerance (PBFT)
This is the consensus based on majority. Each node updates and validates the blockchain network based on a certain given set of rules or conditions. If majority of the nodes in the network reflect the same result upon update, then the network is said to be in consensus. There could be few rogue nodes that could violate the network rules, but their outcome is not accepted as it goes against the accepted algorithm. The algorithm should fulfill the necessary conditions, and all the nodes must agree and execute the same conditions to derive at the desired output.
Proof-Of-Work (PoW)
One of the first and traditional algorithms devised is the Proof-of-Work. Bitcoin-based blockchain network and Ethereum use this algorithm. Unlike PBFT, PoW does not need consensus based on majority. It is an algorithm that takes enormous computing effort. Only nodes with greater computing power can take up the PoW. The first node that completes the task with the desired output gets a chance to create the block and is compensated for its efforts. PoW typically involves some kind of cryptographic hashing to achieve the desired target or outcome. We will talk of PoW in detail in Chapter 2.
Proof-Of-Stake (PoS)
With PoW, one needs enormous computing power that results in high-energy consumption. This may not be desirable. PoS overcome this by providing an alternative approach called the stake of the user. The user possessing or owning the highest digital currencies (or some asset) gets a chance to create the block in the blockchain network. So instead of investing in high power computing nodes, one can rather buy out cryptocurrency (or own assets) and increase their stake to validate and create a block of transactions.
Security
We talked about security earlier in the components of the blockchain section. Security is one of the important components in the blockchain architecture. Based on the implementation of blockchain —whether permissionless or permissioned — required security and consensus strategies are applied. In public blockchain, every node can participate in the network, while in the permissioned network, you have some form of access control that only allows required nodes to participate in a transaction.
Every entity in the blockchain network must be bound to an identity. In a permissionless network, entities are typically restricted to users participating in the transaction, while in case of a permissioned network, the entities comprise of organization, nodes, users and anything that has a role to play in the blockchain network.
For a permissioned blockchain, Public Key Infrastructure (PKI) platform can be used where a trusted Certificate Authority (CA) can issue crypto credentials. The crypto credentials could take the form of certificates and keys. Private keys can be used for signing and public key for verification. It results in a trusted network where all the participants know who they are and their roots of trust. Now as the parties involved in the blockchain network might leverage their own crypto credentials, possibly setting up their own CA, it is essential that the blockchain implementation provides a plug-and-play service or a level of abstraction to effectively manage, verify and validate entities using different security mechanism across the network.
In short, the blockchain security should be equipped with five effective measures viz. authentication, access control, integrity, confidentiality, and non-repudiation.
You can learn how to build Blockchain applications with my free course — https://www.udemy.com/course/building-blockchain-applications-using-ethereum-hyperledger-fabric/
Published at DZone with permission of Navveen Balani, DZone MVB. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments