Basic Authentication Using Spring Boot Security: A Step-By-Step Guide
Learn how to implement basic authentication in Spring Boot, as well as the basic steps required to configure Spring Security, load user data, and authenticate users.
Join the DZone community and get the full member experience.
Join For FreeThe importance of secure web applications can never be overstated. Protecting sensitive user data and making sure proper authentication is in place are essential whether you're creating a straightforward blog or a sophisticated corporate solution. This is where the potent Java application framework Spring Boot Security comes into action.
One of the core techniques for securing online applications is basic authentication. It entails using the users' credentials — typically a username and password — to authenticate their identity. A solid basis for safe user authentication, Spring Boot Security offers efficient and dependable techniques to deploy basic authentication in your Java applications smoothly. Therefore, be certain to engage qualified Java engineers who are familiar with Spring Boot security procedures.
A seasoned technocrat with years of experience building technical solutions for various industries using Microsoft technologies. With sharp understanding and technical acumen, I have delivered hundreds of Web, Cloud, Desktop, and Mobile solutions and am leading the technical department at Excel Add-in development company — iFour Technolab Pvt. Ltd.
A qualified developer will possess a solid understanding of authentication protocols, such as Basic Authentication, and be capable of integrating them seamlessly into your application's architecture. Their expertise will not only enhance the security of your application but also contribute to its overall performance and reliability.
What Is Spring Boot Security?
Spring Security is a framework that provides authentication and authorization features to Spring applications. One of the key benefits of using Spring Security is that it can help protect your application against various types of attacks, such as CSRF, XSS, Brute Forcing, and MITM. Configuring Spring Security properly ensures that your application is secure and protected from malicious actors.
Why Spring Boot Security?

What an excellent point! Assuming you are new to application security, it is consistently smart to depend on a security system that has been planned and approved by experts in the business. This may assist in ensuring that your application is protected from common security threats and is secure.
You can use the expertise of the framework's developers and community with Spring Security to make sure that your application is safe and protected from common security threats.
- In this blog, we will discuss how to implement user authentication in Spring Boot using Java.
Overview
In your web applications, user authentication ensures the identity of users and grants them access to the application.
Spring Security is the most popular and customizable security framework for Java applications that provides a wide range of security features, including user authentication.
Implementing user authentication with Spring Security involves configuring authentication providers, defining user roles and permissions, and configuring security filters. By implementing user authentication with Spring Security, you can ensure that your application is secure and protected against unauthorized access.
Important Terms
Authentication: It is a process of verifying the user’s identity.
Authorization: The process of giving access rights and privileges to authenticated users is known as authorization.
Filter: A filter is an object that is invoked at the pre-processing and post-processing of a request.
How Spring Security Works
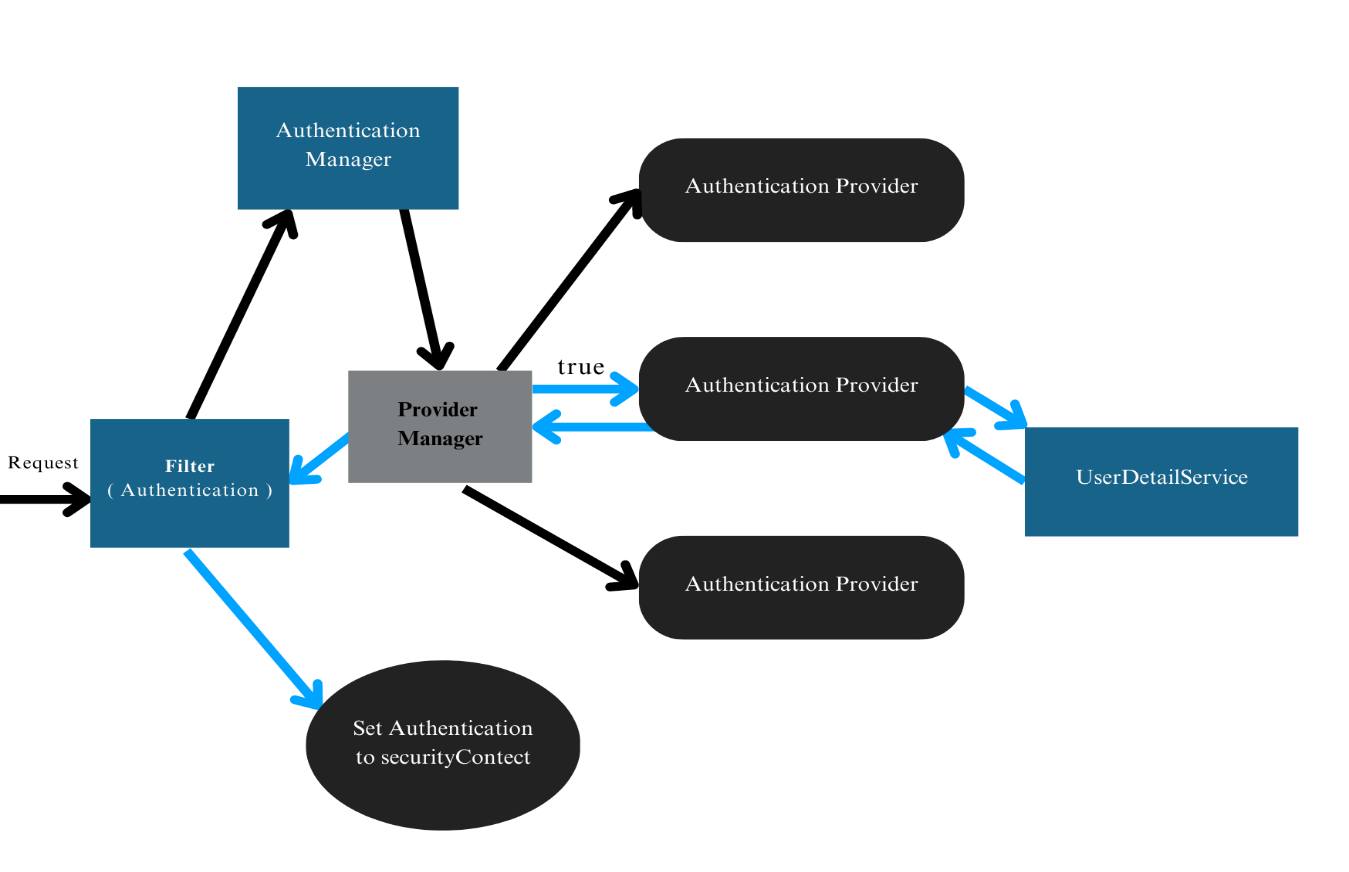
Internal working of Spring Security
When a request comes to the filter, it is Create an authentication object, adds essential information to it, and then delegates the request to the authentication manager. The authentication manager calls authenticate (Authentication auth). The authentication manager is an interface. That’s why we use an authentication provider to authenticate the user. There are many authentication providers available, each with its own set of techniques. The authentication manager calls the provider manager to choose a suitable authentication provider. If the provider manager finds a suitable authentication provider, it takes the help of a user detail service that interacts with the database. Then, it will return the valid authentication object, and then the provider manager sends that valid authentication object to the filter, and then the filter sets authentication to the security context.
Implementation
Getting Started
To get started, you are going to head over to start.spring.io and create a new project. Fill in the metadata for the project and add the dependencies. You can choose the project version and metadata as you prefer. Here I use spring boot version 2.7.12 and Java version 17.
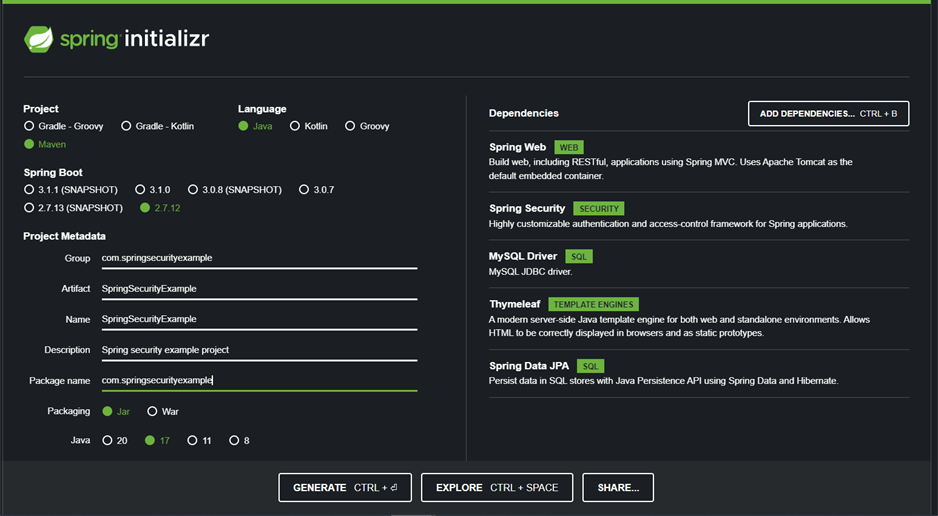
This will generate the following dependencies in your pom.xml:
<dependencies>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-security</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>com.mysql</groupId>
<artifactId>mysql-connector-j</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-thymeleaf</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-data-jpa</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
<scope>test</scope>
</dependency>
<dependency>
<groupId>org.springframework.security</groupId>
<artifactId>spring-security-test</artifactId>
<scope>test</scope>
</dependency>
</dependencies>Spring Boot automatically secures our application by adding the spring-boot-starter-security dependency in our pom.xml. We cannot access applications without authentication.
By default, when Spring Security is added, it provides a default username and password. The username is set as “user,” and the password is generated when the application is run.
Conclusion
In this blog, we have discussed how to implement basic authentication in Spring Boot. We have covered the basic steps required to configure Spring Security, load user data, and authenticate users. By following these guidelines, you should have the knowledge and understanding to incorporate user authentication into your Spring Boot applications.
With Spring Boot Security, implementing basic authentication becomes a breeze. It provides a comprehensive set of features and pre-configured components that allow you to focus on your core application logic without getting bogged down in the complexities of authentication implementation. By integrating Spring Boot Security, you can ensure that only authorized users gain access to your application's protected resources.
Thus, businesses should keep a strong emphasis on building basic authentication with Spring Boot security techniques for their application. Additionally, it's important to confirm knowledge of these security techniques before they hire a Java developer.
So, prefer hiring a skilled Java developer who is well-versed in Spring Boot Security. A competent Java developer will deeply understand the Spring framework, security concepts, and best practices. They can leverage the power of Spring Boot Security to create a robust authentication system tailored to your application's specific requirements.
Opinions expressed by DZone contributors are their own.

Comments