Automating Application Security in Modern Software Development
It’s irresponsible at every level to ignore the risk of insecure code while doubling-down on anti-virus solutions and firewalls — neither of which protects applications.
Join the DZone community and get the full member experience.
Join For FreeToday, every organization has become a software company. The increasing dependence on automation demands that software survive and thrive despite an increasingly hostile environment. Insecure code has become the leading security risk and, increasingly, the leading business risk as well. It’s irresponsible at every level to ignore this risk while doubling-down on anti-virus solutions and firewalls — neither of which protects applications.
Application Security Demands Automation
As software increasingly “eats the world,” the security of that software becomes increasingly important. Every line of code you write makes you easier to attack. Insecure software caused 82% of financial breaches in 2015 and has been the leading cause of breaches overall for the past nine years. Virtually every study has shown that almost every web application and API has serious vulnerabilities.
But the scale of the problem is out of control. We need tools that enable novice developers to reliably build and operate secure applications and APIs. We must transform paper-based security policy and guidance into “security as code” without disrupting modern, high-speed software development.
Unfortunately, even well-established application security programs often can’t operate at the speed and scale required. These programs rely on experts and their tools are for use by experts only. The traditional approach disrupts the software lifecycle and is incompatible with modern high-speed software development. When you combine the technology and human cost, the annual per-application cost for these programs can range from $50,000 to $100,000 per year.
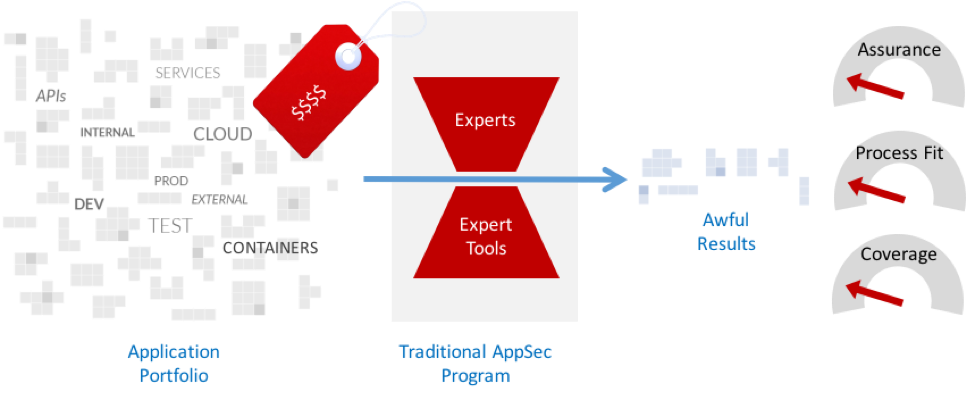
And Software Is Getting Increasingly Difficult to Secure
Let’s look at some of the factors that make securing modern software difficult.
First, there has been an explosion of frameworks and libraries since the inception of automated dependency resolution tools like Maven. This has resulted in applications with several hundred libraries instead of just a few. This massive increase in size makes it much more difficult to find vulnerabilities. So tools must be aware of these libraries and how they are used by custom application code.
Further, there is also a trend towards using APIs (REST, SOAP, RPC, etc.) to create applications with Angular or mobile front ends. These APIs are difficult to assess and protect because the structure of their communications is more difficult to understand. Unless tools can understand
the application, they don’t produce very good results. And if the tools require a lot of expert tailoring and configuration, they won’t get used.
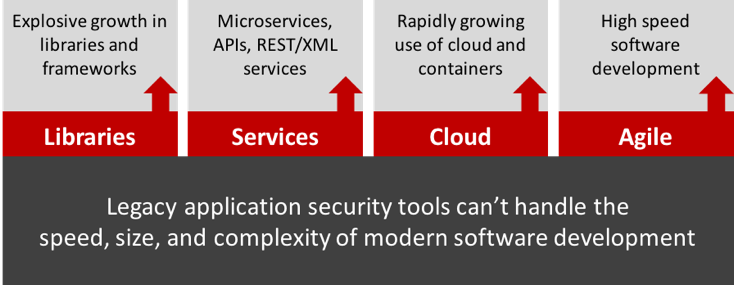
Finally, high-speed software development practices like Agile and DevOps have broken traditional approaches to security. Organizations used to wait until just before deployment to do an in-depth security review that could take weeks to complete. However, when projects are deploying weekly, daily, or hourly, there’s just no time for that approach. We need a different approach and different tools.
Best Practices for Automating Application Security in Modern Software Projects
Modern software development requires continuous security to go along with continuous integration/delivery/deployment. The challenge in a nutshell is enabling an existing development pipeline to reliably produce secure software without creating roadblocks or even speedbumps. The reality is that if security slows down innovation, it will be bypassed.
Choose applications security tools for speed, ease-of-use, accuracy, and scalability. Instant feedback and ease of use are critical. Appsec tools need to be usable by people in development and operations without any security experience. Any inaccuracy will require an expert to resolve, and experts don’t scale.
Integrate security directly into your pipeline. To shorten those feedback loops, look for tools that deliver results directly into tools you’re already using, like Slack, HipChat, JIRA, Maven, Jenkins, SIEM, and PagerDuty. Security issues should look and feel like any other kind of development or operations issues.
Detect vulnerabilities. Modern software development demands high-speed feedback on vulnerabilities. Legacy static (SAST) and dynamic (DAST) scanners are difficult to automate
and generate false alarms. Investigate the use of newer interactive (IAST) tools that assess your applications from within, using the latest instrumentation technology.Protect against attacks. Application attack protection isn’t just for defense against known attacks, it provides a fast and flexible way to block novel attacks that emerge. Legacy web application firewalls (WAF) create network architecture complexity and aren’t very accurate. Fortunately, runtime application self-protection (RASP) is gaining wide adoption for its flexible deployment and impressive accuracy.
Use threat intelligence and security research to improve your security architecture. Using generic tools that search for “negative” coding patterns is a good start. But as you mature, you may want your tools to automatically enforce the security patterns you’ve chosen. This is a “positive” approach to security. Ultimately, you want to be able to automatically verify that all your applications have the right security defenses in place, that all the defenses are correct, and that they have been used in all the right places.
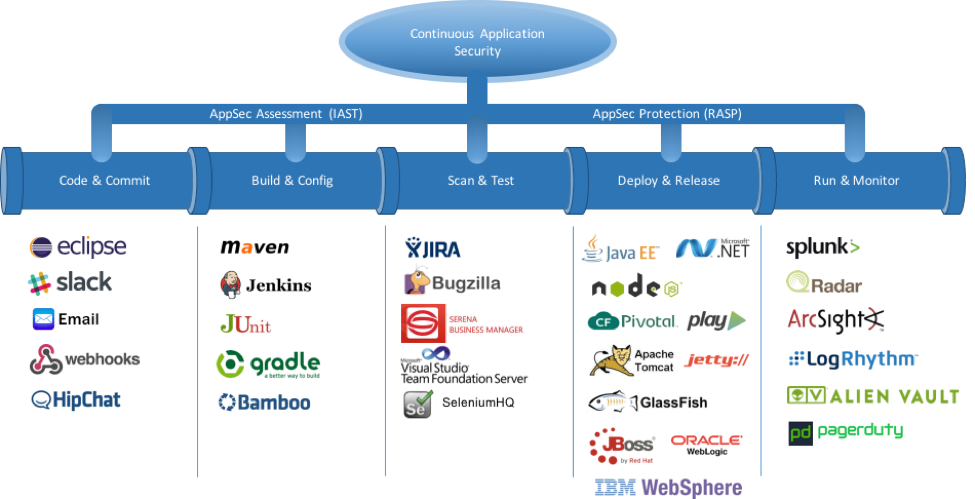
The good news is that it is possible to create a software pipeline that can enable you to reliably secure code and protect applications in operations. Modern application security tools can give you instant feedback on both vulnerabilities and attacks.
More Security Goodness
Published at DZone with permission of Jeff Williams, DZone MVB. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments