Demystifying SAST, DAST, IAST, and RASP: A Comparative Guide
In this comparative guide, explore the inner workings of the essential security testing tools driving the shift-left security movement.
Join the DZone community and get the full member experience.
Join For FreeThis is an article from DZone's 2023 Enterprise Security Trend Report.
For more:
Read the Report
Effective application security relies on well-defined processes and a diverse array of specialized tools to provide protection against unauthorized access and attacks. Security testing is a critical part of an application security strategy and should be seamlessly integrated into the secure software development lifecycle (SDLC), acting as a proactive and continuous defense against vulnerabilities throughout the software development process.
Development teams are now delivering increasingly complex software using fast release cycles and continuous development and deployment practices. Identifying and addressing potential vulnerabilities at an early stage in the SDLC has given rise to the implementation of a security approach referred to as shift-left security.
Within this article, we'll explore the inner workings of the essential security testing tools driving the shift-left security movement. Along our exploration, we'll also demystify runtime application self-protection (RASP) and compare it with the other security testing technologies.
Static Application Security Testing
Static application security testing (SAST) is a well-known and mature technology that is used to statically analyze source code for known potential vulnerabilities and insecure coding practices without executing it. SAST tools leverage techniques and technologies that are already in use in compilers, such as lexical and semantic analysis, type checking, control and data flow analysis, and taint tracking.
In the last decade, these tools have rapidly evolved these compiler techniques to a set of much more comprehensive and complex methods for analyzing the security of the code.

Figure 1: The main phases of SAST
In modern DevSecOps, static analysis security testing is typically performed as early as possible by integrating SAST tools into developers' development environments and build pipelines. They are valuable security tools to establish good code hygiene and overall secure development practices.
Challenges of SAST Solutions
Although modern SAST tools demonstrate high effectiveness in identifying coding flaws, they have limitations in identifying business logic or design flaws. Such flaws can only be found through security code review and threat modeling. Also, due to their lack of runtime visibility, SAST tools are not always accurate in their results, often producing false positives.
One major challenge of SAST solutions is that modern apps do not consist only of application source code. In modern development environments, the "everything-as-code" paradigm is embraced. That includes not just application source code, but it also extends to infrastructure, smart contracts, continuous integration and continuous delivery (CI/CD) pipelines, business process workflows, and declarative scripts. This diverse range of code artifacts poses a considerable challenge for SAST tools, which are traditionally designed to analyze application source code.
Another challenge arises when analyzing large codebases, like large monoliths, as it might take several hours to complete the process. However, if configured to scan only incremental changes, the time required to complete the static analysis is significantly reduced to just a few minutes.
SAST Tools and Solutions
In the last decade, a plethora of both open-source and commercial SAST tools have emerged, each with different sets of features and capabilities. Free-to-use and open-source tool options that have gained significant popularity include, but are not limited to: Spotbugs, Bandit, Brakeman, Checkov, CodeQL, Semgrep, Snyk, and SonarQube.
On the commercial front, SAST solutions offer comprehensive capabilities, often incorporating advanced features such as machine learning, analytics, secret scanning, software composition analysis, remediation recommendations, and integrations with development environments.
Dynamic Application Security Testing
Dynamic application security testing (DAST) stands as a well-established technology used to evaluate the security of web applications and APIs through simulated attacks. DAST tools invoke an application's entry points in the same way that attackers would. DAST tools don't depend on the source code. Instead, they employ reconnaissance techniques to dynamically discover the app's endpoints, generate an attack surface map, initiate probing by sending carefully crafted requests, and subsequently analyze the outputs for potential vulnerabilities.
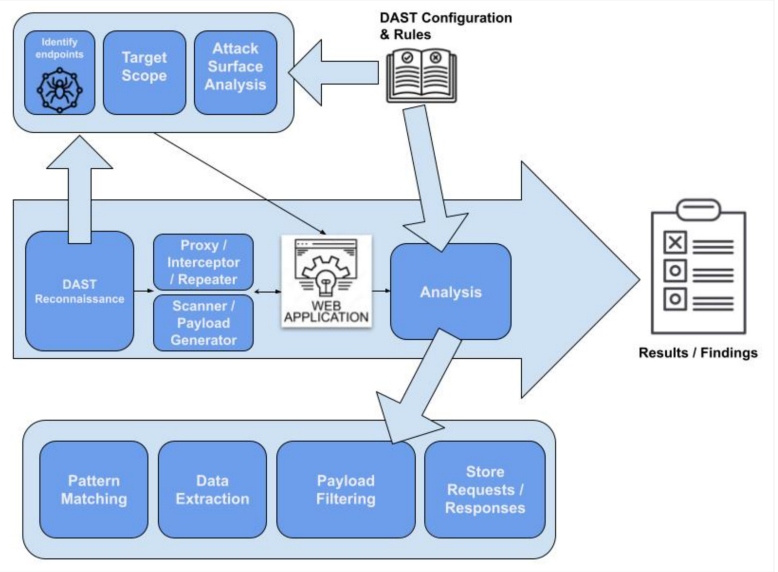
Figure 2: The main phases of DAST
DAST tools provide features and techniques commonly employed in penetration testing or security assessments of applications. These techniques include vulnerability scanning, request/response analysis, brute force, exploit generation, attack surface discovery, and simulated attacks. Over the years, DAST tools have advanced these features, providing a more comprehensive and fine-grained approach to identifying vulnerabilities in web applications.
Challenges of DAST Solutions
Due to their lack of source code visibility, DAST tools are not always accurate in their results, often producing false positives. They also cannot identify the exact location of a vulnerability in the code. When assessing large-scale applications, DAST tools often take several hours to complete their security testing. Configuring DAST tools to scan only specific application scopes, APIs, or incremental changes can help alleviate this challenge, reducing the time required to conduct dynamic analysis.
In modern DevSecOps, DAST is typically executed later in the development lifecycle, often in staging or production environments. Integrating a DAST tool into a CI/CD pipeline is also possible; however, it should be rolled out in phases after ensuring that the configuration of the deployed DAST tool does not produce false positives and does not delay the pipeline considerably more. For these reasons, many development teams have chosen not to integrate DAST tools into their CI/CD pipelines. On the other hand, penetration testers typically include DAST tools as standard tools in their toolkits.
DAST Tools and Solutions
Notable free-to-use and open-source options include, but are not limited to: ZAP, PortSwigger Burp Suite Community Edition, Nikto, and Wapiti. These tools provide basic scanning, testing, and reporting capabilities. On the other hand, commercial DAST solutions provide more advanced and powerful features with numerous configuration options, fine-grained customization, extensive payload libraries and generators, automated workflows, and professional reporting against security standards, such as OWASP Top 10 or PCI DSS.
Interactive Application Security Testing
Interactive application security testing (IAST) is an innovative approach to application security testing that examines vulnerabilities during the actual execution of the application with requests that originate from real users or automated tests. This newer technology utilizes instrumentation to monitor running applications, providing real-time visibility into security issues within the code.
IAST solutions not only actively monitor HTTP requests and responses exchanged with the application, but they also gather runtime information on the running instance. This level of visibility allows the solution to provide context-driven insights that effectively eliminate any blind spots and improve the detection accuracy. Consequently, IAST tools demonstrate a notably low false positive rate and offer advanced insights into vulnerabilities by correlating identified issues with precise source code locations — something not achievable through DAST tools.
IAST solutions typically require integration into the CI/CD environment in order to automatically run all the test suites that will exercise the system's execution paths. This integration enables the immediate delivery of vulnerability information and remediation guidance early in the SDLC.
To employ an IAST solution, an instrumentation agent must be deployed on the runtime platform of the application. The goal of the IAST agent is to embed specially created sensor modules in the application code through instrumentation. These sensor modules track the application's runtime state while tests are running.
Challenges of IAST Solutions
It is important to highlight that the effectiveness of IAST solutions depends on whether all the code paths are being actively exercised or executed with the proper attack payloads during the testing period. In a typical scenario, end-to-end negative tests and DAST scanners are used to send attack payloads against the app.
Meanwhile, the IAST tool monitors parts of the app while validating if the payloads uncover flaws or successfully exploit vulnerabilities. This is the reason why IAST tools may not deliver 100% code coverage and their results' effectiveness heavily depends on the coverage and capabilities of the security test suites and the accompanying DAST scanner. This limitation can result in gaps in vulnerability detection, especially in scenarios where certain parts of the application's code remain unexplored or untriggered during the testing process.
Another downside of IAST tools is that they are programming language dependent due to their dependence in instrumenting the runtime platform.
IAST Tools and Solutions
Notably, the OWASP AppSensor project deserves attention as the first open-source IAST tool. Implemented as a library, its primary goal is to provide prescriptive guidance on incorporating runtime application intrusion detection and automated response mechanisms. It serves as a reference implementation and is not intended for direct deployment in its current state. It is important to note that its feature development appears to have ceased since 2019.
Numerous commercial instrumentation-based security solutions have emerged, each contributing distinct features across all layers of the modern web application stack. Commercial IAST solutions provide unique security detection capabilities compared to other security testing tools that lack the visibility that runtime instrumentation provides.
Most commercial IAST solutions provide integrations with integrated development environments, facilitating security analysis during the application development phase. This integration proves valuable in aiding developers with precise and efficient remediation efforts to address identified security issues. Certain IAST solutions broaden their integration functionalities to include SIEM systems, issue-tracking systems, and compliance dashboards, and some even offer automated generation of web application firewalls (WAF) or RASP rules.
Runtime Application Self-Protection
RASP extends the principles of IAST, utilizing the insights gained from runtime monitoring, but it goes a step further by incorporating self-protecting capabilities directly within the application. Effectively, this means that unlike SAST, DAST, and IAST, which are testing technologies used to identify vulnerabilities during various stages of the SDLC, RASP focuses on realtime self-protection. It actively monitors and analyzes the execution of the application and responds to security threats as they occur, making it a proactive defense mechanism rather than a testing tool.
Similar to IAST, RASP uses instrumentation agents that hook into the runtime platform to monitor and analyze the application's behavior. Unlike other defensive solutions, such as WAF, RASP goes beyond analyzing inputs and outputs by actively monitoring and assessing the internal execution and state of the application. IAST utilizes instrumentation to monitor runtime execution for the identification of vulnerabilities and attacks, while RASP, not limited to detection, actively modifies the executing code to prevent attacks and protect the application.

Figure 3: Conceptual diagram of IAST/RASP architecture in a tech stack
Image source: Introduction to IAST, DZone Refcard
Having said that, not all RASP solutions implement the same type of self-protection mechanisms or analyze the internal execution of the app at the same code-level granularity. Different RASP solutions may employ diverse approaches and detection algorithms, achieving different levels of accuracy and efficacy in terms of real-time threat detection, false positive rates, and self-protection capabilities. RASP tools leverage the unique insights provided by the runtime platform to go beyond traditional pattern recognition techniques, identifying anomalous behavior and actual security attacks that may not be covered by known patterns or signatures.
Importantly, RASP solutions have the ability to provide self-protecting capabilities throughout the entire runtime stack and not only the application's business logic layer. This includes protection of the runtime environment, standard libraries, third-party libraries, frameworks, servers, and middleware.
Additionally, certain RASP solutions offer on-the-fly virtual patching of vulnerable applications. This means that they can dynamically apply security controls or mitigations to protect against known vulnerabilities without requiring the application to be rebuilt or restarted. This way, RASP solutions help bridge the gap between the discovery of a zero-day vulnerability and the implementation of a permanent fix, providing an immediate layer of protection.
Challenges of RASP Solutions
The issue of false positives is crucial in RASP solutions as there is a risk that the tool may block legitimate and revenue-generating traffic, causing disruptions to the normal operation of the application. Given the potential impact on business operations and the user experience, and the risk of losing trust in the tool, minimizing false positives is a significant concern when choosing or implementing RASP solutions. Striking the right balance between effective threat detection, performance impact, and avoiding false positives with minimal configuration is essential for a successful RASP deployment into production environments. By instrumenting the runtime platform, RASP solutions have unique visibility of the code, which provides the runtime context that is essential for evaluating security intelligence and minimizing false positives.
To achieve this unique visibility, RASP solutions inject specialized sensors in the runtime platform and perform a real-time analysis of the runtime insights. The challenge for RASP vendors is determining the appropriate injection points for these sensors and selecting which detection algorithms to analyze those runtime insights. These design decisions need to be made carefully in order to provide protection with as few false positives as possible while keeping the performance impact as low as possible.
RASP Tools and Solutions
The technical landscape of RASP is complex and marked by strong competition, which may be the underlying cause for the absence of actively maintained, enterprise-ready, open-source RASP solutions. The OpenRASP project is a notable exception. It is a plugin-based runtime security agent that supports Java and PHP, claiming to provide protection against the OWASP Top 10. However, the project's development is rather slow, with its last release in January 2022.
Commercial RASP solutions provide tailored protection across different types of applications. Some are designed for general application security or web applications only, while others specialize in mobile application security, providing runtime protection for both Android and iOS platforms.
When selecting a RASP product, users should take into consideration the trade-off that some vendors make between language support and the depth of security features. Some vendors opt for a more focused approach, offering advanced features for a smaller set of languages, while others prioritize broader language coverage, often with more basic protection capabilities.
A Comparison of Application Security Testing and RASP
Not all tools are the same, so developers and DevSecOps engineers must understand the key characteristics and differences of SAST, DAST, IAST, and RASP in order to make informed decisions about selecting and utilizing the most suitable tools for their specific needs, ultimately contributing to the improvement of the overall security posture in the development lifecycle.
|
COMPARING KEY CHARACTERISTICS OF SAST, DAST, IAST, AND RASP
|
||||
|---|---|---|---|---|
| Criteria | SAST | DAST | IAST | RASP |
| Purpose | Testing | Testing | Testing | Protection |
| Type of testing | White box | Black box | Gray box | N/A |
| How it works | Analyzes source code before compilation | Sends malicious requests and analyzes responses for vulnerability patterns | Instruments the application and analyzes data from both the source code and traffic | Embeds into the app, intercepts requests and responses, and analyzes executing code, aiming to detect and protect apps at runtime |
| Environment | Dev or Test | Dev or Test | Dev or Test | Prod |
| Remediation guidance | Detailed vulnerability information in the source code | Generic vulnerability information and best practices | Rich vulnerability information in the source code and running app | Detailed exploit information on the location and cause in the source code and running app |
| False positives rate | Low to moderate | Moderate to high | Low | Low to none |
| Programming language support | Programming language dependent | Language agnostic | Programming language dependent | Runtime platform dependent |
| Advantages | Finds vulnerabilities during development | Simulates real-world attacks | Provides more accurate results | Blocks attacks in real time |
| Disadvantages | Can miss vulnerabilities that manifest only at runtime | Can miss coding flaws and vulnerabilities that are not exposed by responses | Requires instrumentation agent and is language specific | Installing the agent may pose difficulties and affect performance; is language specific |
Conclusion
This article emphasizes the need for a comprehensive understanding of SAST, DAST, IAST, and RASP to make informed decisions in the development lifecycle. Despite the distinct roles of SAST, DAST, and IAST as testing tools, and RASP as a defensive tool, they share a common focus on proactive security and the shift-left approach. Each of these testing tools contributes to strengthening security measures by identifying vulnerabilities early in the SDLC, aligning with the proactive and preventative principles of the shift-left philosophy in DevSecOps practices.
To protect applications against evolving threats, a comprehensive security testing strategy is required. There is no such thing as absolute security. Thus, it is crucial to implement a testing strategy that combines different security testing methods in all stages of the SDLC and implements defense in depth. This layered strategy focuses on implementing diverse security controls in both testing and production environments.
Striking a balance between effective and thorough vulnerability detection, minimal performance impact, and false positive avoidance is key for a successful and resilient security testing and defense strategy. As the software landscape evolves, continuous adaptation of security practices becomes paramount for safeguarding applications and maintaining user trust.
On a final note, the future of security testing and protection tools will be significantly influenced by generative AI, particularly large language models. This trend involves the increasing integration of AI-based copilot tools to enhance security practices across all layers of the technology stack and throughout the entire SDLC. We should anticipate the advent of AI-powered SAST, DAST, IAST and RASP tools that will provide critical advantages in key areas, including security code reviews, pair programming, test coverage, design and threat model reviews, as well as vulnerability and anomaly detection and attack protection.
This is an article from DZone's 2023 Enterprise Security Trend Report.
For more:
Read the Report
Opinions expressed by DZone contributors are their own.

Comments