Leveraging AI to Bolster Cloud Security for APIs and Microservices
AI-powered cloud security solutions are essential for protecting APIs and microservices from online threats. Learn more about how AI improves cloud security.
Join the DZone community and get the full member experience.
Join For FreeOverview
An API serves as a set of guidelines and protocols that facilitate communication, between software applications. It outlines the methods for software components to interact simplifying the process of developing and integrating systems.
Microservices architecture represents an approach to software development in which a large application is divided into services. Each service concentrates on a business function. They can be developed, deployed, and scaled autonomously.
Cloud security holds importance for APIs and microservices due to the following reasons:
- Data protection: APIs and microservices often handle information. Maintaining security is crucial to safeguard this data from access, leaks, or breaches.
- User authentication and authorization: Implementing security protocols in the cloud environment helps verify the identities of users and services interacting with APIs and microservices. This ensures that authorized entities can engage with the services.
- Compliance with regulations: Numerous industries have regulations concerning data privacy and security. Adhering to cloud security practices ensures alignment with these requirements.
- Ensuring secure communication: APIs and microservices rely on network communication. Securing these channels through encryption and other protective measures is vital to prevent data interception or tampering.
- Mitigating DDoS attacks: Effective cloud security strategies can help minimize the impact of Distributed Denial of Service (DDoS) attacks, which have the potential to disrupt service availability. By defending against attacks the reliability of APIs and microservices is upheld.
- Safeguarding infrastructure: APIs and microservices operating in a cloud environment are components of an infrastructure. Security measures play a role in protecting the cloud infrastructure from vulnerabilities that could be exploited.
In summary, prioritizing cloud security, for APIs and microservices is essential to safeguard data ensure compliance uphold service availability, and shield the system from cyber threats.
Challenges in Cloud Security Without Artificial Intelligence
Dealing with cloud security challenges without the assistance of AI can be quite complex. Some typical hurdles include the following:
- Promptly identifying and responding to evolving cyber threats is crucial for maintaining security. Without the aid of AI-powered threat detection capabilities, organizations might find it tough to detect threats that can evade security measures.
- Manual security procedures are time-intensive and prone to mistakes. AI technologies offer the ability to automate security tasks like vulnerability scanning patch management and incident response allowing security teams to concentrate on strategic endeavors.
- Recognizing abnormalities in user behavior or network traffic patterns is vital for pinpointing security breaches. AI can sift through amounts of data to spot deviations from behavior and raise alerts for further scrutiny.
- Given the changing nature of cloud setups, keeping tabs on all assets and actions can pose a challenge. Without the support of AI-driven monitoring tools swiftly spotting and addressing security incidents becomes quite a task.
- Cloud environments expand based on need, which makes it tricky to ensure security controls across all instances. AI can assist in automating security policy enforcement and guaranteeing that security measures are scalable alongside the infrastructure.
AI-Enhanced Security for APIs and Microservices
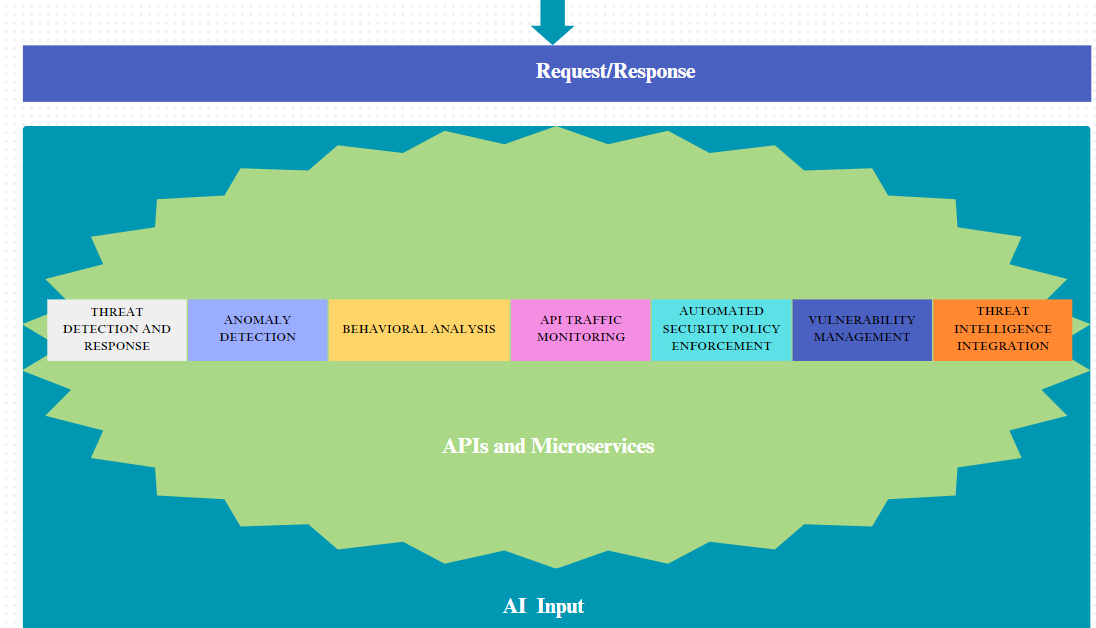
AI-driven cloud security solutions play a role in safeguarding APIs and microservices against emerging cyber threats and vulnerabilities. Here are some essential ways AI enhances cloud security for APIs and microservices:
- Detecting and responding to threats: Security tools powered by AI can analyze data to identify security threat patterns respond promptly to incidents and prevent data breaches and unauthorized system access.
- Spotting anomalies: AI algorithms can recognize behavior in API requests and microservices activities issuing alerts for activities, potential attacks, or unauthorized access attempts.
- Analyzing behavior: AI conducts analysis on users and applications interacting with APIs and microservices to identify normal behavior patterns and deviations that could indicate security risks.
- Monitoring API traffic: AI tools monitor API traffic, analyze request patterns, and detect anomalies to pinpoint security issues like DDoS attacks, data exfiltration, or malicious activities.
- Implementing automated security policies: AI systems automate the enforcement of security policies, for APIs and microservices ensuring the application of security measures while minimizing the risk of errors.
- Managing vulnerabilities: Artificial intelligence-powered systems can scan APIs and microservices to identify vulnerabilities and prioritize patching based on risk assessments. They provide recommendations, for enhancing security to address threats and risks.
- Integrating threat intelligence: Security platforms driven by AI can incorporate feeds of threat intelligence to keep abreast of emerging threats, patterns, and methods of attack. This integration facilitates defense strategies for APIs and microservices.
Organizations aiming to strengthen their cybersecurity defenses safeguard information and uphold the security of their cloud-based applications must implement AI-driven security measures for APIs and microservices. By utilizing AI technologies companies can enhance their ability to detect threats reduce incident response times and reinforce security in a rapidly evolving digital environment.
1. Detecting and Responding to Threats
Ensuring threat detection and response mechanisms for cloud-based APIs and microservices is crucial for maintaining the security and reliability of infrastructures. Here's how AI can be utilized for threat detection and response in this context:
- Real-time network traffic scan: AI-powered tools have the capability to constantly observe network traffic, API requests, and interactions among microservices in time to pinpoint any irregularities, suspicious activities, or unauthorized access attempts.
- Machine Learning models: Utilizing AI-driven machine learning models can identify cyber threats by scrutinizing data sets to detect patterns that suggest actions, enabling proactive identification and response to threats.
- Automated incident response: AI has the ability to automate incident response procedures by triggering predefined actions in response to security incidents, such as isolating compromised services blocking traffic, or isolating affected systems.
- Forensic analysis: AI tools can aid in conducting analysis after an incident, by reviewing logs audit trails, and network activity to reconstruct the sequence of events pinpoint the cause of security breaches, and guide remediation efforts.
- Adaptive security measures: Artificial intelligence has the capability to adjust security controls and settings in response, to changing threat landscapes allowing cloud-based APIs and microservices to adapt to evolving risks and vulnerabilities.
2. Spotting Anomalies
The detection of irregularities plays a role in AI-powered APIs and microservices by enabling the recognition of deviations from patterns or behaviors within the system. This function is crucial for ensuring the dependability, security, and efficiency of the services.
Within the realm of AI-driven APIs and microservices, algorithms for detecting irregularities can be employed to monitor metrics like request/response times, traffic volumes, error rates, and resource utilization. By examining these metrics in time any anomalies or abnormalities can be promptly identified, facilitating intervention and resolution of potential issues.
Incorporating irregularity detection into AI-driven APIs and microservices entails utilizing machine learning models and algorithms to establish behavior patterns. Any deviations from these patterns can trigger alerts or automated responses to address risks or performance concerns.
By integrating irregularity detection into AI-powered APIs and microservices, organizations can improve the reliability, security, and effectiveness of their systems ultimately enhancing user experiences and operational efficiency.
3. Analyzing Behavior
When it comes to AI-driven APIs and microservices, analyzing user behavior involves monitoring and evaluating actions, trends, and preferences. By observing how users interact with these services organizations can spot patterns, irregularities, and areas that could be improved.
This analysis covers aspects like user involvement levels, response times, error frequencies, and usage trends. With the help of AI tools organizations can gather information about user behaviors to customize their services efficiently.
By conducting analysis within AI-powered APIs and microservices, organizations can pinpoint roadblocks, security risks, or areas requiring performance upgrades. By grasping user behaviors businesses can refine their services for usability and responsiveness.
The overall integration of analysis in AI-driven APIs and microservices can result in increased user contentment levels boosted system efficiency and informed decision-making based on data-driven insights.
Here are some popular tools commonly used for analyzing behavior, in AI-driven APIs and microservices
- Google Analytics: Besides its use for web analytics, Google Analytics can also track user behavior within APIs and microservices providing insights into user engagement, interactions, and conversion rates.
- Mixpanel: An analytics platform that specializes in event tracking, Mixpanel allows organizations to monitor user behaviors such as feature usage, retention rates, and user paths within APIs and microservices.
- Amplitude: Another tool focused on product analytics and behavioral analysis, Amplitude helps organizations understand user behavior through cohort analysis and tracking user journeys in applications and services.
- Hotjar: Offering heatmaps, session recordings, and user feedback tools useful for analysis purposes, Hotjar visually showcases how users engage with APIs and microservices.
- Kibana: As part of the Elastic Stack, Kibana serves as a data visualization tool for analyzing log data to identify patterns, anomalies, and trends in user behavior within APIs and microservices.
4. API Traffic Monitoring
Monitoring API traffic is essential to ensure the efficiency, security, and dependability of AI-powered APIs and microservices. Through monitoring API traffic organizations can oversee, analyze, and enhance the flow of data and requests within their systems. This monitoring aids in pinpointing issues, irregularities, and patterns that could affect the well-being of the APIs and microservices.
Various tools and approaches can be utilized for API traffic monitoring in AI-driven environments.
- Monitoring API Gateways: These gateways serve as entry points for APIs and offer insights into incoming as well as outgoing traffic. Tools like Kong, Apigee, or AWS API Gateway can monitor metrics such as request rates, response times, and error rates.
- Logging and tracing: Incorporating logging and tracing mechanisms within APIs and microservices allows detailed information about API traffic to be captured.
- API monitoring tools: Tools such as Elasticsearch, Logstash and Kibana (ELK stack) are capable of analyzing logs and tracking requests as they move through the system. For monitoring APIs, tools like Postman, Insomnia, or Paw can be used to observe API endpoints, send trial requests, and assess response times. These tools prove valuable for gaining insights into API behavior from a user's standpoint.
- Real-time monitoring solutions: To enable real-time monitoring of APIs and microservices, solutions like Prometheus, Grafana, or Datadog offer features that allow organizations to visualize metrics instantly, create alerts, and analyze performance in time.
- Traffic analysis tools: When it comes to analyzing network traffic and inspecting payloads within API communications, tools such as Wireshark, Fiddler, or Charles Proxy are instrumental in providing insights.
- Security monitoring solutions: For enhancing security measures around API traffic, security solutions, like OWASP ZAP, Burp Suite, or AWS WAF can be utilized to monitor security threats anomalies, and Vulnerabilities effectively.
5. Automated Enforcement of Security Policies
Ensuring the security and confidentiality of AI-driven APIs and microservices requires automated enforcement of security policies. By automating this process, organizations can consistently apply, monitor, and enforce security measures across their systems. Below are some strategies and tools that can be utilized for automating the enforcement of security policies in AI-driven APIs and microservices:
- Token-based authentication: Employ token-based authentication mechanisms such as OAuth 2.0 or JSON Web Tokens (JWT) to verify and authorize access to APIs and microservices; automated processes for issuing tokens and validating them. Revoking them contributes to enhancing security.
- Security Policy as Code: Define security policies as code using tools such as Open Policy Agent (OPA) or HashiCorp Sentinel. By converting security policies into code format organizations can automate their implementation, throughout the software development lifecycle.
- Behavioral analysis tools: Utilizing tools for analysis such as Splunk, Elastic Security, or IBM QRadar enables the monitoring and assessment of user behaviors to identify irregularities and uphold security protocols concerning activities within APIs and microservices.
- Access Control Lists (ACLs): Implementing Access Control Lists (ACLs) helps in restricting access to API endpoints and microservices based on established regulations with automated management ensuring that only authorized users or services can access resources.
- Runtime Application Self-Protection (RASP): Employing Runtime Application Self-Protection (RASP) solutions like Contrast Security or Veracode involves embedding security policies into API runtime environments to enforce measures against common threats like injection attacks and data exposure.
6. Vulnerability Management
Effective vulnerability management plays a role in safeguarding AI-driven APIs and microservices by identifying, evaluating, mitigating, and monitoring vulnerabilities to protect systems from potential security risks and breaches.
Here are some important strategies and tools, for managing vulnerabilities in AI-driven APIs and microservices:
- Regular vulnerability scans: Utilize scanning tools like Nessus, Qualys, or OpenVAS to check APIs and microservices for known vulnerabilities. Consistent scans help pinpoint weaknesses that attackers could exploit.
- Security patching: Establish a process for managing patches to ensure that software components and dependencies stay updated with the security fixes. Timely patching can address known vulnerabilities. Lower the risk of exploitation.
- Secure code reviews: Regularly review code for security issues to address insecure practices and vulnerabilities. Tools like SonarQube, Checkmarx, or Fortify can automate code analysis to detect security flaws in the codebase.
- API security practices: Follow practices for API development, including authentication, authorization, encryption, input validation, and error handling. Adhering to these practices reduces the attack surface. Enhances the security of APIs and microservices.
- Incorporating threat intelligence: Integrate feeds on threat intelligence to stay updated on emerging security threats and vulnerabilities that are pertinent to AI-driven APIs and microservices. Tools like ThreatConnect or Recorded Future can help in threat detection and response.
- Incident Response Plan: Develop a plan for responding to incidents that involve vulnerabilities in APIs and microservices. This plan should outline procedures for addressing security incidents, including steps for remedying vulnerabilities, communication strategies, and recovery processes.
7. Integrating Threat Intelligence
It is crucial to integrate threat intelligence into AI-driven APIs and microservices as a way to bolster security measures identify threats and effectively manage risks. By utilizing threat intelligence resources, organizations can keep abreast of threats, vulnerabilities, and malicious activities that may pose risks, to their APIs and microservices.
Here are some important strategies and tools, for integrating threat intelligence in AI-driven environments:
- Threat intelligence feeds: Stay updated by subscribing to threat intelligence feeds from trusted sources like CERTs, ISACs, and commercial providers. These feeds offer real-time insights into known threats, indicators of compromise (IOCs), and attack patterns that are relevant to APIs and microservices.
- Incorporate Security Information and Event Management (SIEM): Integrate threat intelligence feeds into SIEM solutions such as Splunk, ArcSight, or LogRhythm. This integration helps in correlating security events analyzing logs and identifying threats based on indicators provided by threat intelligence.
- Monitor Indicators of Compromise (IOC): Keep a watch for matches against IOCs from threat intelligence feeds within the logs of APIs and microservices traffic data and system activities. Tools like MISP (Malware Information Sharing Platform) or OpenCTI can be valuable for managing and correlating IOCs
- Implement Security Orchestration, Automation, and Response (SOAR): Deploy SOAR platforms such, as Demisto, Phantom, or Swimlane to automate tasks related to managing threat intelligence. These platforms streamline incident response processes and remediation workflows specifically designed for APIs and microservices. Employ machine learning algorithms to analyze data from threat intelligence identify patterns and anticipate security incidents in AI-driven APIs and microservices. Machine learning models can enhance the ability to detect threats and automate response measures effectively.
Conclusion
By integrating AI-based technologies for detecting and responding to threats in cloud-based API and microservice environments, organizations can strengthen their cybersecurity defenses improve incident response capabilities, and safeguard their assets against cyber threats.
Opinions expressed by DZone contributors are their own.

Comments