AI/ML Techniques for Real-Time Fraud Detection
The importance of AI/ML techniques in real-time fraud detection, with a focus on behavioral analytics to combat increasingly sophisticated fraud methods.
Join the DZone community and get the full member experience.
Join For FreeIn today's technologically advanced society, fraud detection is a major concern. According to the Association of Certified Fraud Examiners (ACFE), fraud costs companies trillions of dollars worldwide, or nearly 5% of their yearly sales (ACFE Report to the Nations 2024). Businesses are increasingly using cutting-edge technology like artificial intelligence (AI) and machine learning (ML) as fraudsters become more skilled. Behavioral analytics is at the forefront of this movement and directly fights fraud.
Problem Statement
In today's modern era, fraud is growing beyond conventional methods because of utilizing the volume and velocity of online transactions.
The primary challenges include:
- Transaction volume: Financial institutions conduct 100,000+ transactions a day on average, making manual reviews impracticable (Statista Report on Banking Transactions).
- Changing strategies: Con artists constantly modify their methods by using social engineering, fake identities, and credentials that have been stolen (FTC 2023 Fraud Trends Report).
False positives: Overly conservative fraud detection can lead to $48 billion in false declines annually, frustrating customers and damaging business reputations (Juniper Research Report 2023).
Understanding Behavioral Analytics
To find abnormalities, behavioral analytics uses dynamic user behavior. It detects minute behavioral anomalies, including odd keystrokes, mouse movements, or transaction patterns, in real time, unlike static fraud detection systems. It identifies unusual typing speed during a login attempt in mobile applications, which is significantly quicker than the user's usual pattern and may indicate bot activity.
Example from recent news:
In 2024, a major retailer used behavioral analytics to uncover a coordinated fraud ring exploiting their gift card system. By analyzing transaction timings and purchase patterns, they flagged suspicious activity and prevented a potential loss of over $15 million (Retail Dive).
In essence, behavior analytics are required in your product to stop malicious actors from abusing it. Let's examine the many industry trends that have been observed thus far to address this issue.
AI/ML Techniques Empowering Behavioral Analytics
1. Supervised Learning Models
- This technique uses labeled datasets where input-output pairs are known.
- This uses ML train models to predict specific outcomes, such as fraud likelihood.
- Here are the algorithms usually used under this technique: Decision Trees, Random Forests, Support Vector Machines (SVM), and Neural Networks.
Example: A bank used a neural network to analyze transaction data, achieving a 40% reduction in fraud-related losses within six months (Financial Times).
2. Unsupervised Learning Models
- This technique focuses mainly on identifying hidden patterns or groupings in the data instead of depending on labeled data. This technique is most effective for anomaly detection, clustering similar behaviors, and reducing dimensionality. This technique does not rely on labeled data; instead, it focuses on identifying hidden patterns or groupings in the data.
- The algorithms usually used in this technique are K-Means Clustering, Principal Component Analysis (PCA), and Isolation Forests.

Example: PayPal employs clustering algorithms to monitor over $900 billion in payments annually, detecting outliers indicative of fraud (PayPal Annual Report 2023).
3. Reinforcement Learning
- This technique uses trial and error to learn optimum behaviors in a dynamic environment.
- This method is best suited for real-time fraud detection since adaptive strategies are required. Based on the decisions, the ML training model may receive rewards or penalties.
Case study: A leading e-commerce platform integrated reinforcement learning to optimize fraud detection. This resulted in a 30% decrease in customer complaints due to false positives (McKinsey Insights).
Key Features With Visuals
1. Anomaly Detection
This technique focuses on learning optimal actions through trial and error in a dynamic environment.
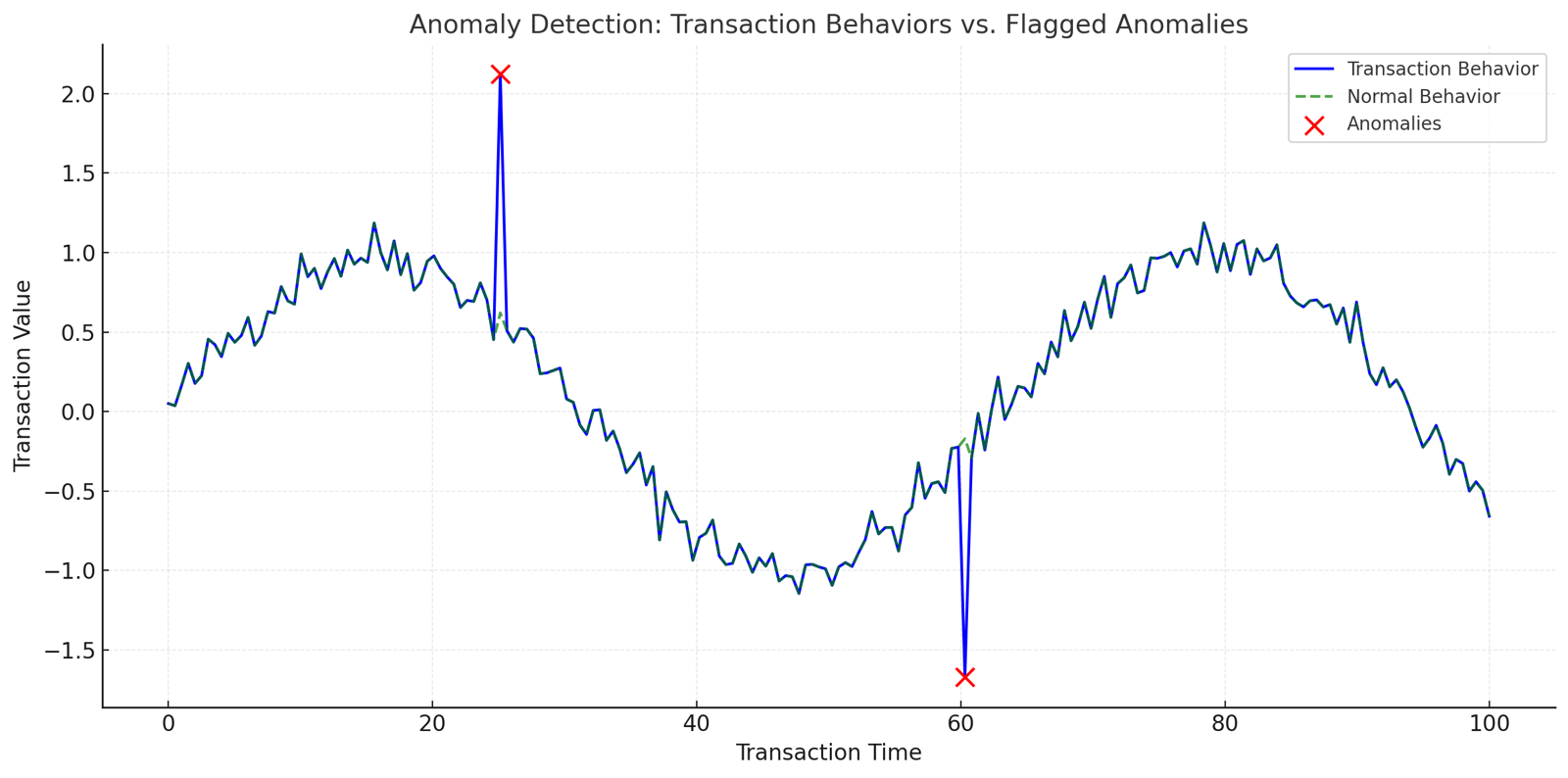
Anomaly detection is used to identify patterns in data that deviate significantly from anticipated behavior. These outliers, or anomalies, typically indicate crucial events such as fraud, system failures, or data errors. It employs machine learning, artificial intelligence, and statistics to detect aberrant activities in real time.
Key Steps in Anomaly Detection
- Define normal behavior: Establish a baseline using historical or behavioral data (e.g., average transaction amounts or typical login times).
- Identify deviations: Use algorithms to detect deviations from the baseline.
- Flag anomalies: Label transactions or behaviors that exceed thresholds as anomalies for further investigation.
Example of Anomaly Detection in Action
Scenario: A Mobile Banking App
An illustration of anomaly detection in action is provided.
- Typical conduct: In the United States, a user usually signs in from their home device and transfers modest sums once a week.
- Anomaly found: The same account attempts a high-value transfer while logging in from a fresh device in a foreign nation.
- Reactive: The software flags the transaction as suspicious and starts an additional verification procedure.
By analyzing these deviations in real time, anomaly detection helps organizations respond quickly to threats and ensure legitimate users are minimally impacted.
2. Behavioral Heatmaps
Behavioral heatmaps highlight places with high or low activity and graphically reflect user interactions. They are used in fraud detection to identify patterns or abnormalities in user behavior across several dimensions, such as app screens, transaction types, and geographic locations.
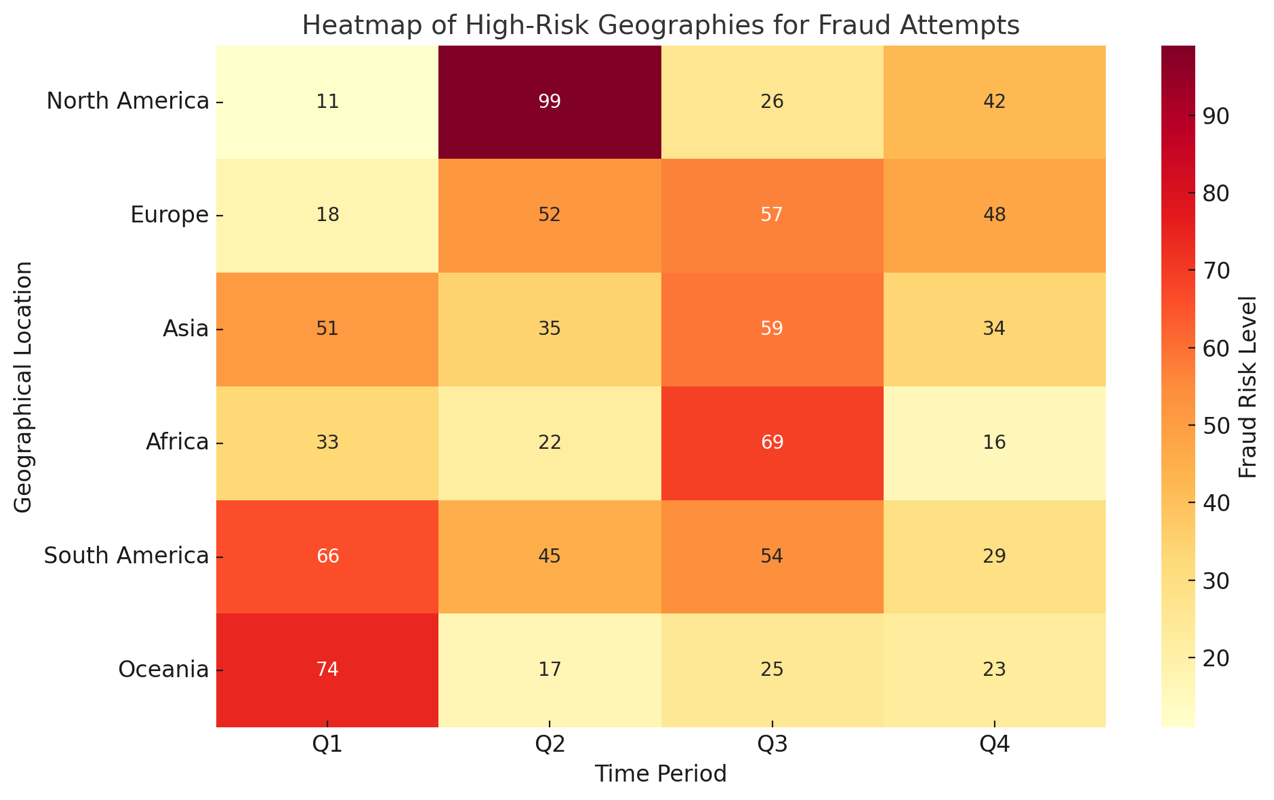
Applications of Behavioral Heatmaps
- Geographic Fraud Detection
- Heatmaps show regions with unusual transaction activity, which helps to identify high-risk areas for fraud.
- Example: A spike in failed login attempts from a specific country can indicate a bot attack.
- In-App Behavior Monitoring
- This tracks which parts of an app users interact with the most. Unusual activity in least-used features may indicate malicious behavior.
- Example: A sudden increase in interactions with the account recovery feature could potentially signal account takeover attempts.
- Transaction Anomalies
- This highlights patterns in transaction volume or frequency.
- Example: A user initiating multiple high-value transactions in quick succession may trigger a fraud alert.
3. User Flow Diagram
A user flow diagram visually represents the step-by-step process in which a system detects and responds to fraudulent behavior in real time. Below is an example tailored for a mobile app.
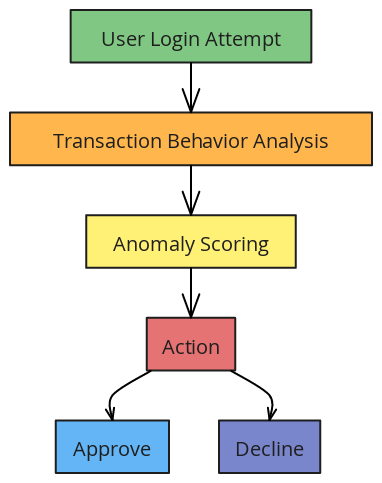
Key Steps in the Flow Diagram
- User Login
- The user enters credentials like username, password, or biometric data, and behavioral data such as device details, typing speed, and location is captured.
- Behavioral Analytics Engine
- This includes analyzing login patterns against historical data and then assigning an anomaly score based on deviations (e.g., new device, location).
- Risk Assessment
- High-risk: Block access and notify the user or security team.
- Medium-risk: Prompt for additional verification (e.g., OTP, security question).
- Low-risk: Proceed to the app dashboard.
- Transaction Monitoring
- This includes user actions such as navigation patterns and transaction types in real time.
- Anomaly Handling
- This consists of flagging unusual transactions or interactions and temporarily holding high-risk activities for manual review or user confirmation.
- Fraud Prevention Action
- In the event that fraud is verified, reverse transactions, block the account or notify authorities.
- If it is real, then communicate the reported behavior to the user in order to maintain trust.
Challenges With Supporting Data
Here are possible challenges.
|
Challenge |
Impact |
Example |
|---|---|---|
|
Data Privacy Regulations |
Compliance with GDPR/CCPA slows data collection |
EU fines on data misuse reached €2 billion in 2023 (EU GDPR Fines Tracker) |
|
Scale of Data |
Real-time analysis of millions of events |
Major banks process 1M+ transactions per minute (Statista Banking Data 2023) |
|
Adversarial Tactics |
Fraud mimics legitimate behaviors |
Fraudulent credit card use rose 15% in 2023 (FTC Report 2023) |
Conclusion
Organizations struggle to detect fraud because of privacy regulations, the volume of data, and evolving adversarial tactics. Finding a balance between compliance, scalability, and agility is necessary to maintain effective and lawful fraud protection systems.
To efficiently combat fraud, businesses must embrace AI/ML-driven behavioral analytics. Future innovations will likely include hybrid systems combining biometric and behavioral analytics for robust fraud prevention.
Thanks for reading this! You can connect with us on Milav’s Linkedin and Swapnil’s Linkedin!Opinions expressed by DZone contributors are their own.

Comments